Unwanted Program
Potentially unwanted program, or shortly PUP, is the application that appears to be dangerous for usage. There are several reasons for the program to be considered potentially unwanted. That app can have a declared functionality and be useless at; it may even be safe to use - but have so many malignant usage facts that it is easier to ban them preventively. The only thing they all have in common is the damage level: it does not let the security vendors define them as malicious since their danger is not as severe as in full-fledged malware.
Types of Potentially unwanted programs
As it was mentioned above, potentially unwanted programs differ by their origins. Some of them are released without diligent testing, some are questionable, and some are often used by cybercriminals. These properties directly affect the further actions the user must take.
Poorly-made applications
Not all programs that are spread on the Internet are well-designed and tested. Sometimes, the developer is not experienced enough to find and fix the issues. That’s why the final product may malfunction. In the best-case scenario, such an odd job will crash without any serious effects on the rest of the system. However, if the app touches the important OS mechanisms, like file system, drivers, or exact hardware, the program's malfunction will likely cause problems with these elements or the entire system. It is OK when you can bring it back to normal by simply rebooting the computer - but that is not always the case.
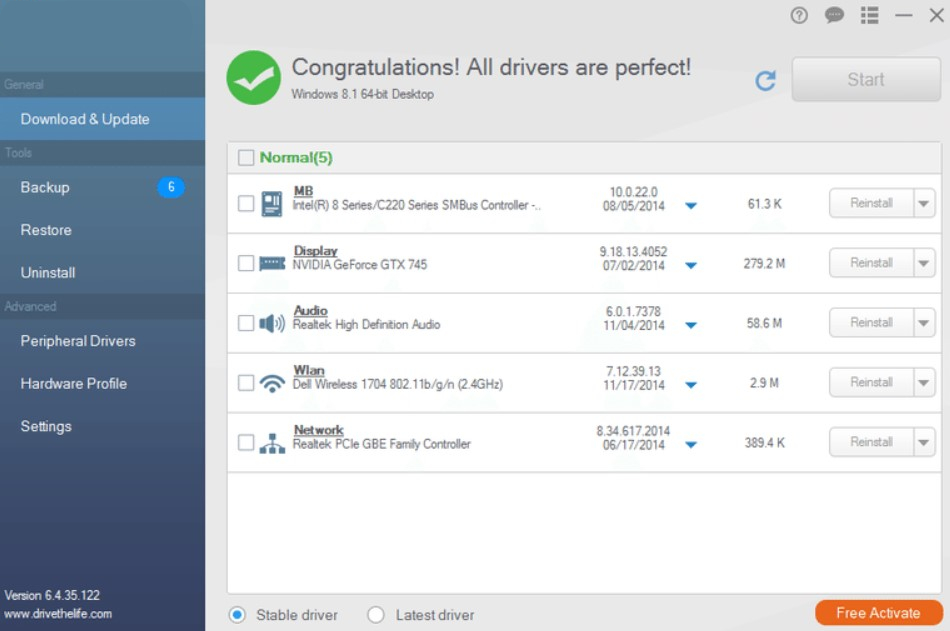
The perfect example of such dangerous, unprofessional apps are various tools for drivers updating and adjusting the hardware properties. Sure, it is possible to find a well-working app that will supply you with the most recent drivers, but many more programs do that terribly. The developers do not publish their sources of drivers - and it would be perfect if those were official hardware vendors’ sites. More often, they take the drivers somewhere else - the main danger. Besides the fact that drivers are the only way your OS can manage the devices properly, the security layer your CPU uses to handle the drivers is shallow. If the malware is injected as a driver, it is capable of taking control over your programs or even the whole operating system.
Questionable apps or hacktools
The most often class of a questionable program classified as PUP is hack tools. Hacktools, as you can guess from their name, are made to hack something, usually the system components or elements of certain applications. Most often, they aim at license-checking mechanisms of different programs - breaking it makes it possible to use the program without buying a license. The popularity of such applications makes the ideal carrier for different malware. The other category of such apps hacks the encryption-related mechanisms to decrypt the data or get the credentials. Although users may apply these apps for their intended purposes, hackers often use these tools.
The best examples of such programs are Mimikatz (credential hacking tool) and KMSAuto. The former exploits the Windows offline authentication mechanism bugs to get the system login credentials. It can be handy for cases when you’ve forgotten the password from one of the machines or a fired employee set his password and did not tell it. For obvious reasons, it is viral among hackers as well. KMSAuto is an infamous Windows hacking tool that makes it possible to use Windows without the licence. But very often, this app acts as the trojan downloader, which installs a pack of malware to your PC.
Bundle installers
The vast majority of PC users have installed free software at least once. Such programs do not bring money to their developers, which is suboptimal for anything bigger than a narrowly-used utility for a small group of people. Larger audience obviously creates a demand for new functions, and program devs start seeking for funding. Some stick to donations, others – embedding advertisements, but some people contract other software developers to install their programs together with their own development.
To manage such a process, they use so-called bundle installers. They offer the functionality needed to install several apps along, without downloading each program separately. Because of the concealed nature of such installations, security software detects them as unwanted programs. You may know them by the detection names from Microsoft – OfferCore, InstallCore, BundleInstaller and the like.
Rogue software
Rogue programs, also known as scareware, are the type of unwanted programs that attempt to look like a legit program but extort money from the user by scaring them. System cleaners, anti-malware software, and driver updates are often disguised for rogue programs. Usually, they are spread through the affiliated websites and advised on various forums. After the installation, they will likely show that you have dozens of problems on your PC. Those “hazardous” items are OK, and all the program wants is for you to pay for the license.
Some of these programs can easily be removed in a traditional manner - via programs list or the uninstall.exe file. However, you will most likely struggle to do this - just because such apps are made to be hard to remove. None of the aforementioned ways will be workable, and the harsh removal through deleting the root directory will likely fail, too.
Potentially unwanted programs examples
There are hundreds and thousands of examples of unwanted applications, but only the most exceptional receive attention wherever. The most odious PUP examples are worth a separate article, but we will try to explain them shortly.
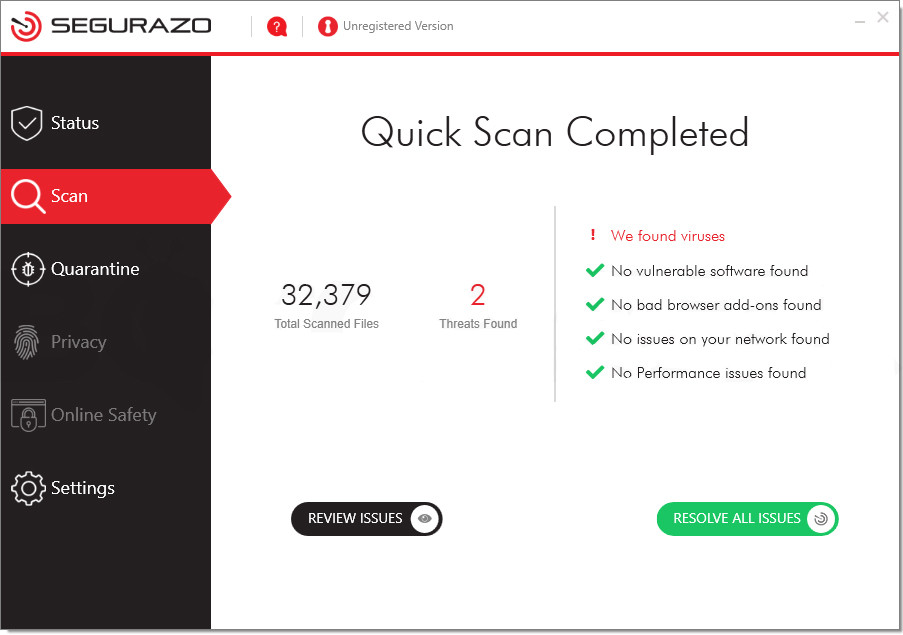
sAntivirus, also known as Segurazo Antivirus
The unwanted app that mimics anti-malware software. It randomly blocks the files on your computer and then asks you to purchase a license. It is not just a poorly designed antivirus that falsely detects clean files. It specifically aims for programs like Photoshop or Maya. It is impossible to use these programs unless you pay for the thing or manage to remove it from your PC.
CCleaner by Piriform
An odious system cleaning tool that is not harmful by design. The main problem of CCleaner is a chosen way to monetize the development. As it is free, the developers decided it may be a great option to put third-party apps in the installation bundle to receive a commission payment for each installation. Hence, most users who do not check the installation window diligently will also receive junk apps they’ve never intended to install.
MediaArena
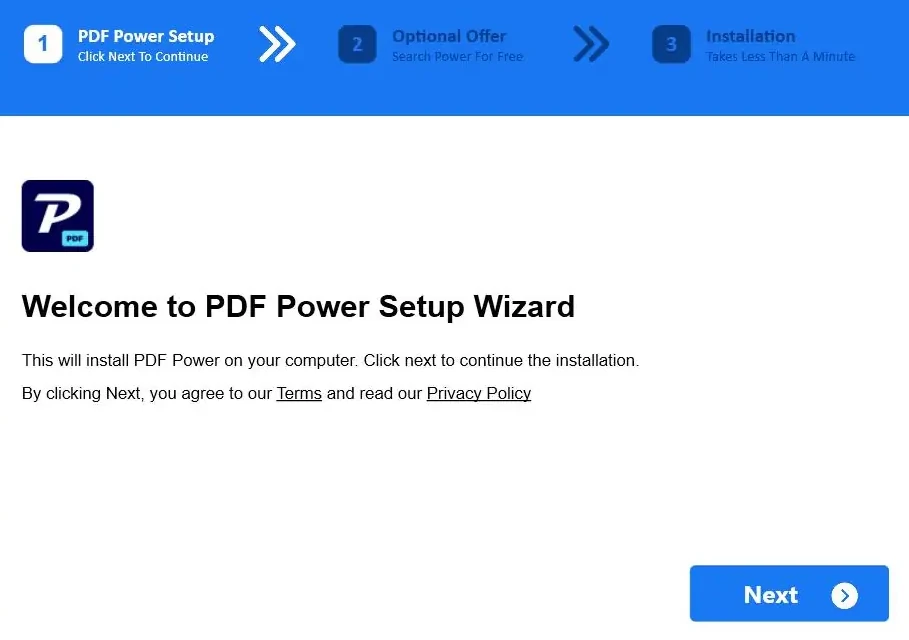
This group of unwanted programs mimics a browser plugin or a stand-alone app for news monitoring, file converting, or similar small activities. It is best known for the PDFPower app, which mimics, obviously, a file converter. But in fact, it modifies your browser and starts showing dozens of ads each time, acting like a mix of adware and browser hijacker. Besides being obviously unwanted, it may still be promoted on forums or software collection sites. Though, the main way of MediaArena injection is the aforementioned bundling.
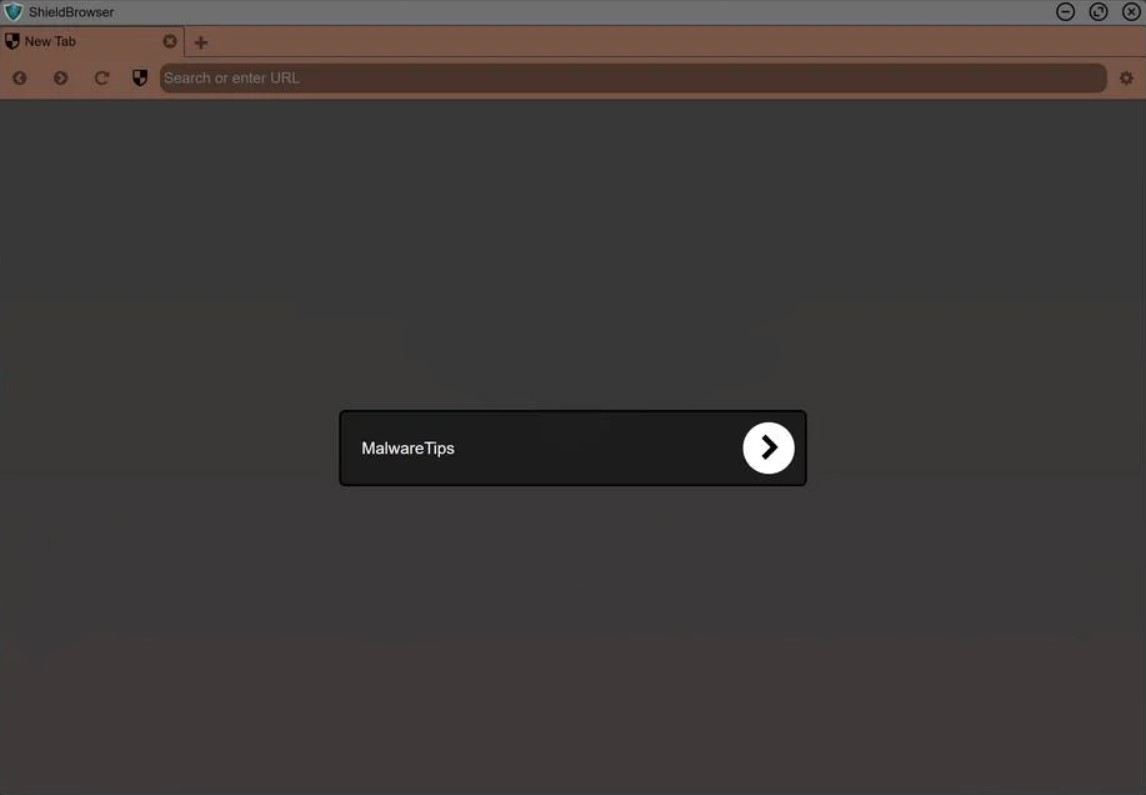
ShieldBrowser
A Chromium-based web browser is a 100% secure alternative to the Chrome browser. In fact, does not offer anything new or outstanding but annoys the user with unwanted ads and constant changes to the used search engine. Moreover, there is no guarantee that this “secure” web browser does not steal the information you type. As with any other software that uses the open-source Chromium core, it should be open-source as well - but its developers neither communicate with users nor offer a static link to the source code.
Another thing that makes ShieldBrowser questionable is the way it is spread. Generally, it is offered in malicious banners on the web that are trying to scare you with rants like “your web security is in danger”. Moreover, it is sometimes seen as bundled software - considered malicious.
KMSTools also known as KMSAuto or KMSPico
The other well-known application exposes the user to a double danger. First, this Windows activation tool uses leaked corporate keys to activate your system. At least this thing is enough to get punished for piracy. Even though it can complete its task - it is not legal to do so. But the problem of this tool is much wider.
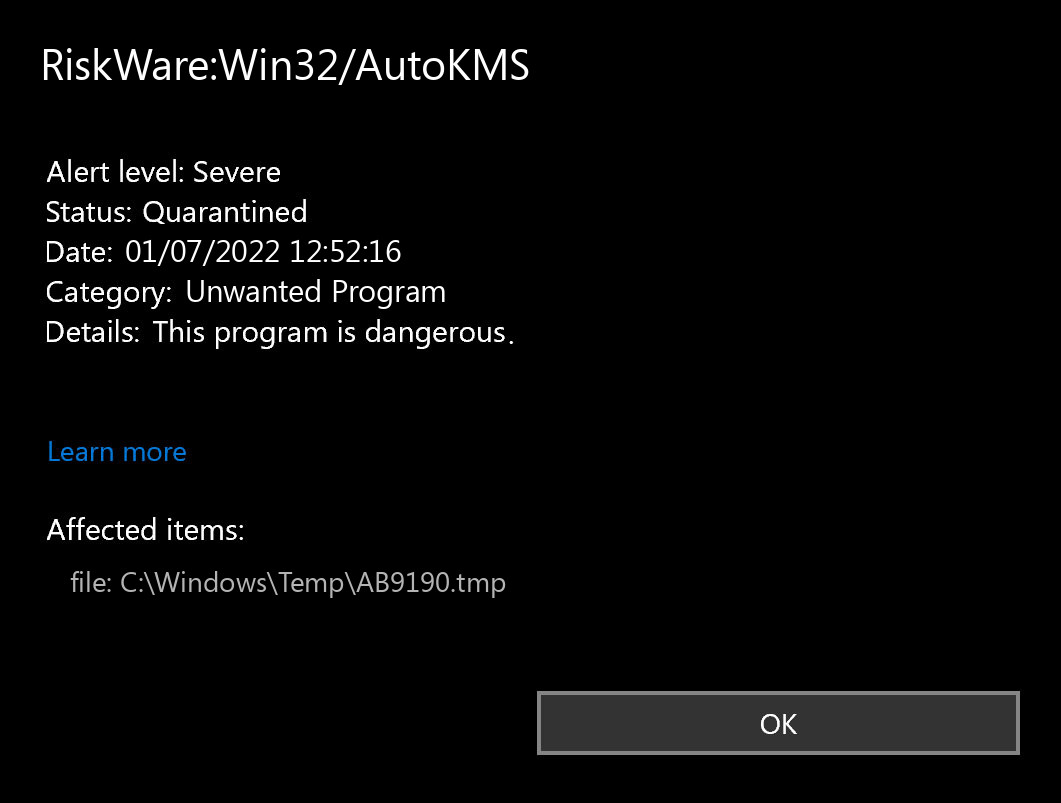
Since KMSTools and its contemporaries are trendy among certain categories of users and are detected by antivirus software, it is a perfect disguise for malware spreading. Most of the time you need to disable your security software to run this program. Malware is very easy to get in since it does not even need to have any tricks to circumvent the system's protection. Such a sly trojan virus inside of the Windows activators is such an often case that using KMS hacking applications is synonymous with getting a pack of malware on your computer.
Is potentially unwanted program harmful?
This kind of software is not called “unwanted” occasionally. Its usage is related to a big risk for your system and files and possibly exposes you to a malware injection. However, that does not mean you will obligatorily get some bad consequences. As was mentioned, some programs can give you the functionality you want but are either unreliable or exploitable by cybercriminals. Such things as KMSAuto that we mentioned above are outlawed - hacking the Windows license can lead you to some big fines.
Therefore, we can assume three types of risk from using programs that are considered unwanted. Personal risk supposes the possibility of file loss or system damage because of the poor design of the program. Malware risk, as you can guess from its name, stands for the possibility of this app being used for malicious purposes - either directly or to install the payload. And the third one - financial - is for extorting money for “solving the problems”. The most positive thing about this type of PUPs is that it almost ceased to exist in recent years.
What unwanted programs do?
The effects of unwanted programs may differ from app to app, depending on what functionality it pretends to have. When the PUP tries to be a driver updater or system cleaner, it will likely annoy you with constant offers to purchase a license and sudden scans out of the blue that significantly harm your performance. These programs are not optimized, so you’d likely suffer even when you have a pretty powerful system.
Aside from that, such PUPs can cause serious system disruptions by modifying the important software elements. Such mischief is likely unintended but still makes your PC malfunction. Moreover, the possible relations with cybercriminals who develop and distribute malware may lead to the installation of the one as a driver for your hardware. In such a case, the virus will be able to manage your system.
Unwanted programs that act as organizers or time-management tools of some sort will likely throw you to the pages full of ads simultaneously with the scheduled notifications. So yes, such PUAs act more like adware, making money on you by showing you banners you never wanted to see. Alternatively, these unwanted programs may act as browser hijackers when used as browser plugins. The typical symptoms of such a thing are search engine hijack, query redirection, blockage of some of the browser functions, and ads on every page (even on the start one!).
“Family trackers” or other stuff that offers to keep track of the defined users may show no visible problems. Meanwhile, it diligently collects all user information, acting as typical spyware. Sure, such apps are less effective than genuine spyware examples, but they may still lead to identity theft or blackmailing. And still - if it is pleasant to know that a third party checks your activity hours, location, battery charge, and so on?
How can potentially unwanted programs be prevented?
Unwanted programs, contrary to “regular” malware, do not appear on your PC in a deliberate manner. They pretend to be normal programs and thus usually appear only when you do something wrong - in particular, install the program you are unfamiliar with. There is no feedback on it on the Internet. Hence, the steps to prevent the PUP appearance are the following:
- 1. Check up on the programs advised to you by somebody. Even if your friend recommended that photo editing software to you - it is better to read the reviews, especially if you have never heard this name.
- 2. Never apply any questionable things to system components. Will you take unknown medicine after the advice of a shaman in the bungalow? I don’t think so. The same thing is about such important stuff as drivers and system components. It is better to spend a day learning how to do that manually rather than rely on dubious programs - and make your system unusable.
- 3. Use proper anti-malware software. A well-done security solution will filter the unwanted program at the stage of the installation file. Hence, you should not spend a lot of time googling the information - antivirus will do all things for you. Of course, it is recommended to remember which apps were blocked - to avoid even downloading this in the future.