A recently-discovered vulnerability in SLP, a legacy network protocol, can be used for disastrous increasing in DDoS-attack efficiency. As researchers say, the use of SMP vulnerability can push the amplification factor of an attack up to 2200 times – an unseen level.
What is SLP?
First of all, let’s clear things up. SLP, or Service Location Protocol, is a legacy protocol that provides LAN devices interactivity. Simply put, it allows all the devices in the network to see the ways to interact with each other. It primarily intended to ease the setup of file servers, printers and stuff like that. Devices were informing about their presence and activity, and were accepting the commands via SLP. With time, other means of communication with such devices appeared – such as UPnP or DNS-SD. Nonetheless, the technology remains demanded, especially in places where old hardware is used.
BitSight researchers, who claimed the detection of a new vulnerability, detected more than 2000 organisations around the world that use this protocol. It includes ~54,000 instances of SLP protocol usage. Hence, this technology is hard to call “dead” or “unused”. And having the possibility to exploit it in any way may have disastrous consequences.
SLP Vulnerability Causes Unseen DDoS Amplification
DDoS attacks that rely on IoT devices are not a new thing. But using CVE-2023-29552, it is possible to push them to a completely different scale. This vulnerability allows an adversary to register services within the network that uses SLP, and send commands to it using a UDP connection. It does not have a serious potential for hackery purposes, but these pseudo-services can wreak havoc on networks. The only thing that limits hackers in their attacks is the max number of services supported by the protocol.
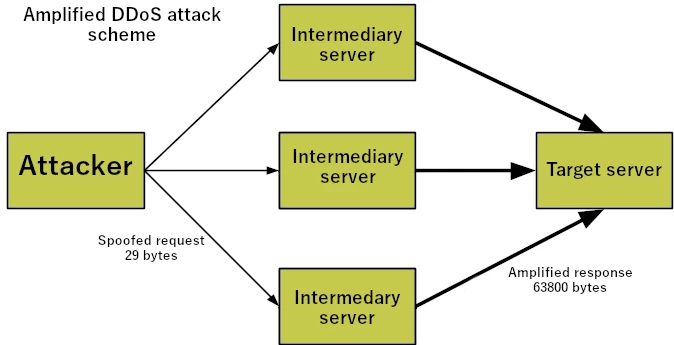
DDoS amplification attack is pretty simple in its essence. Instead of sending a direct request to a target server, crooks send a tiny request to an intermediary server. The request is picked specifically to call for a much bigger response package. And the key trick there is to spoof the request source IP and set – yes, you guessed it right – a target’s IP. Having extreme amounts of services in the network, ready to respond to requests, it is easy to jam even well-protected targets. Moreover, crooks can boost up the response package size to its limits – 65,000 bytes. Considering that, an amplification factor may reach 2200 – 500KB of traffic sent in requests will end up at 1.7GB in responses. To compare, one of the most massive DDoS attacks – against AWS in 2020 – had an amplification factor of 55X.
How to Protect Against This Breach?
Being a pretty popular and widely-used type of attack, DDoS forced the creation of a huge amount of counteraction measures. It can be implemented on all possible levels – from a specific network design to cloud services that will take the strike for you. However, in this specific case, the defensive strategy should build up from securing the SLP vulnerability.
The problem here is that this protocol does not receive updates itself, and vendors that develop their solutions for the use with SLP are the only place to rely. Some of the ones touched by the problem have already released patches. However, there are over 650 products that can use this protocol, and can be vulnerable to this breach. It could take months or even years for all of them to receive security updates. It is possible to mitigate the issue partially – by closing the 427 UDP port, used by SLP – but it causes a lot of inconvenience. If your network uses SLP, a much better option is to contact the software vendors whose products you use. Once they offer a patch, it is recommended to install it as soon as possible.
For that reason, a much better and faster solution is the use of specific network security methods. Most efficient ones against DDoS attacks are firewalls and network detection and response solutions (NDR). The former will restrict any external and unauthorised connections, making it impossible for hackers even to connect to your network. NDRs, on the other hand, act in a more complicated way. They are designed to track and log any network activities, detecting unusual activities and potentially dangerous connections. Such a software will not only block the attack attempt, but also provide extensive logs about events, giving the security team the ability to adjust their actions in future.