An investigation into a supply chain attack that hit 3CX last month found that the incident was caused by another supply chain compromise.
First, the attackers targeted Trading Technologies, which automates stock trading, and distributed trojanized versions of its software.
Let me remind you that the FBI warned about the increase of supply chains attacks, and the media, for example, wrote that the whole country of Vietnam suffered from a complex supply chain attack.
3CX is a developer of VoIP solutions whose 3CX Phone System is used by more than 600,000 companies worldwide, with more than 12,000,000 daily users. The company’s client list includes such giants as American Express, Coca-Cola, McDonald’s, BMW, Honda, AirFrance, NHS, Toyota, Mercedes-Benz, IKEA and HollidayInn.
Let me remind you that the attack on 3CX took place at the end of March 2023. An Electron-based desktop client, 3CXDesktopApp, was compromised and used to distribute malware to the company’s customers.
Unfortunately, it took 3CX representatives more than a week to respond to numerous customer reports that its software suddenly became malware, although experts from several large information security companies reported this at once, including CrowdStrike, ESET, Palo Alto Networks, SentinelOne and SonicWall.
When the fact of compromise had already become obvious, the head of 3CX said that the ffmpeg binary file used by the 3CX desktop client could serve as the initial penetration vector. However, FFmpeg denied these allegations.
As a result, 3CX advised its customers to remove the malicious desktop client from all Windows and macOS devices and immediately switch to the Web Client App, a progressive web application (PWA) that provides similar functionality.
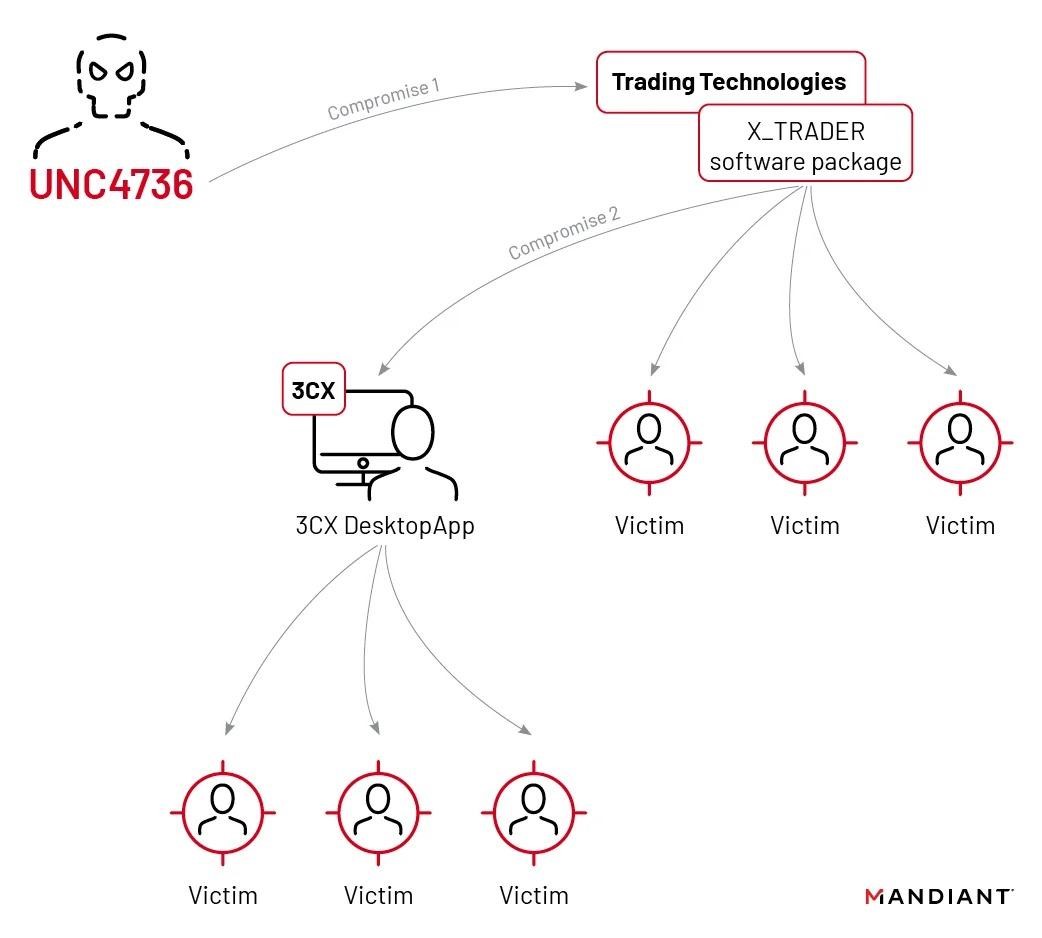
As it became known now, the attack on 3CX occurred as a result of a compromise of another supply chain. Mandiant experts, who helped 3CX investigate the incident, said that it all started when a trojanized X_Trader installer from Trading Technologies was downloaded and installed on the personal computer of a 3CX employee.
This led to the deployment of a modular VEILEDSIGNAL backdoor designed to execute shellcode, inject the communication module into Chrome, Firefox, and Edge processes, and then self-destruct.
As a result, the group, which the researchers track under the identifier UNC4736, stole corporate credentials from the employee’s device and used them to side-travel the 3CX network, eventually compromising the build environments for Windows and macOS.
That is, the initial compromise of the Trading Technologies website took place more than a year ago: the malicious version of X_Trader, equipped with the VEILEDSIGNAL backdoor, was available for download at the beginning of 2022, and the hack itself happened at the end of 2021. At the same time, it is not entirely clear where exactly the 3CX employee found the trojanized version of X_Trader in 2023.
According to experts, the UNC4736 group is associated with the financially motivated Lazarus hacker group from North Korea. Based on infrastructure duplication, the analysts also linked UNC4736 to two other APT43 clusters tracked as UNC3782 and UNC4469.
Worse, Mandiant believes that the incident could have affected a number of organizations that are simply not aware of the hack yet.