Capita, a London-based international business process outsourcing company, was hacked recently. Users noticed strange events in the company earlier this month, but the confirmation appeared only on April 20, 2023. Black Basta ransomware gang posted Capita among other victims on its Onion leak website.
What is Capita?
Capita is a company for business processes outsourcing. Back office management, financial, treasury and management advisory, property and infrastructure management – that all to it. Being the biggest company of its sector in the UK, it has clients from all over the world, including large companies and even governments. According to their latest reports, the company has over £6.5 billion in contracts with governmental organisations. Despite such bright success, the company had its own story of failures – minor, but remembering ones. And it seems that we witness another case where its name will be mangled with an extra “r” letter.
Capita Hacked, Gigabytes of Data Leaked
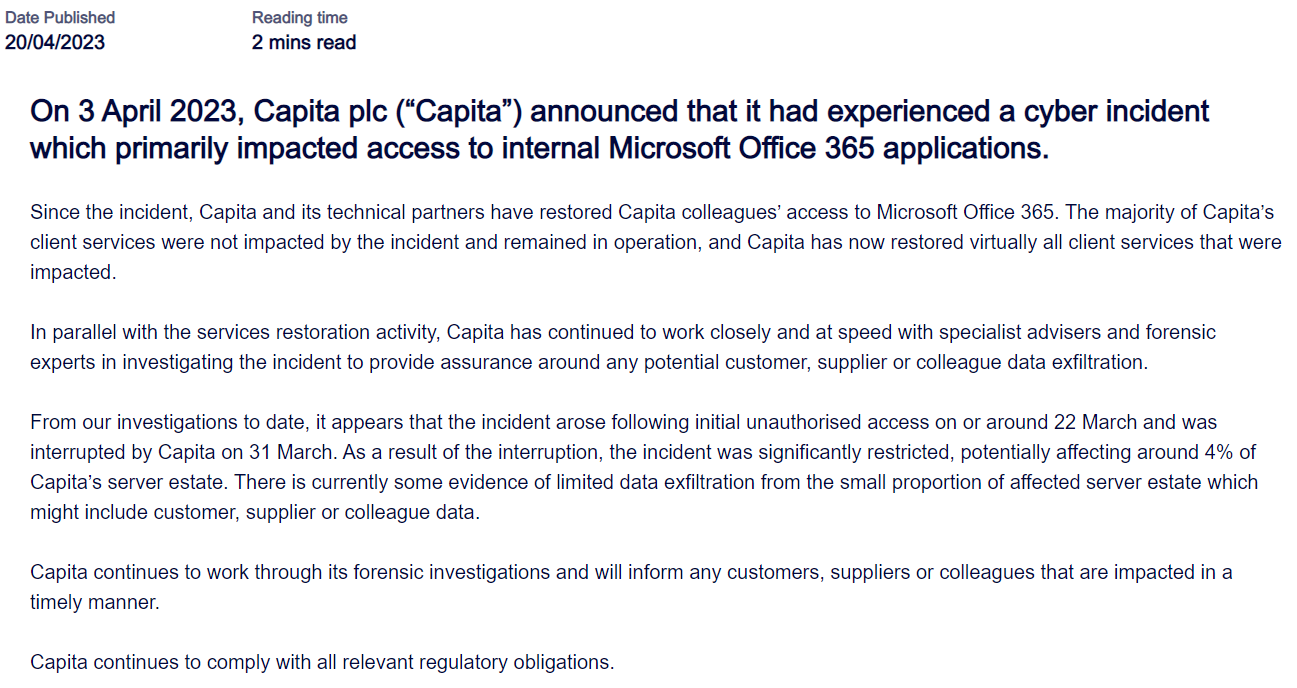
In early April 2023, Capita’s executives claimed the “minor security incident”. Later, they disclosed that this “minor incident” involved ransomware deployment. The exact gang disclosed the successful attack by adding Capita to their list on their Darknet website. However, the company was in no haste to name the intruder and enumerate the consequences. Until April 20, when another official notification was released, the company was rejecting any claims on data leaks. However, it still states only about a minor leak – contrary to what can be found in the data samples published by hackers.
This, however, contradicts the other evidence of the attack. Black Basta is not a “hit-and-run” gang; aside from ciphering, they commonly steal a certain amount of data. On average, this gang grabs around 500GB of data from each of its victims. Then, following double extortion methods, they ask for an additional ransom to delete the leaked information. If it is not paid, the gang releases the stolen, making it accessible to everyone. Other crooks sell the data on the Darknet – i.e. receiving their profit despite the company’s ignorance.
As you could have seen in the screenshot above, the company rejects experiencing any problems. This, however, contradicts the webinar cancellations and rescheduling for later. In recent interviews with BBC, the company’s officials again stated that no data leaks happened. Meanwhile, they confirm the breach and name the approximate date of its beginning – March 22, 2023.
Capita Breach Lasted for Weeks
Several independent investigations confirmed that hackers were inside the network weeks before the incident was uncovered. Analysts found evidence of usage of a specific sample of QakBot – QBot BB20 – for initial access. This dropper trojan is a pretty common guest when it comes to attacks aimed at corporations. After getting into the network, hackers were not enrolling their main payload for the next 11 days. Most probably, this gap was used to infect as many computers as possible.
Considering the term it took to spread payloads, and the overall duration of the “incident”, claims of “limited data exfiltration from the small proportion of affected server estate” look unconvincing. Currently, Black Basta hid the Capita from its board, yet it can be accessed through a direct link. Considering changes in official meetings schedule, the problem touches not only internal documents but also a number of ones related to investments and public relations. It is hard to predict the reaction of the company’s contractors when the entire impact will be uncovered – but that will not be pleasant for both parties.
What is Black Basta ransomware group?
Black Basta group is a novice ransomware gang, which appeared in April 2022. Some evidence points to this gang being a re-branding of a ceased Conti group. Key one is the fact that several ex-Conti members continued their careers in cybercrime together with that group. Other members seem to be experienced hackers as well. Overly strong design or their software and used techniques clearly say that being attacked by Black Basta is no joke. Some analysts say it is related to the FIN7 (Carbanak) threat actor.
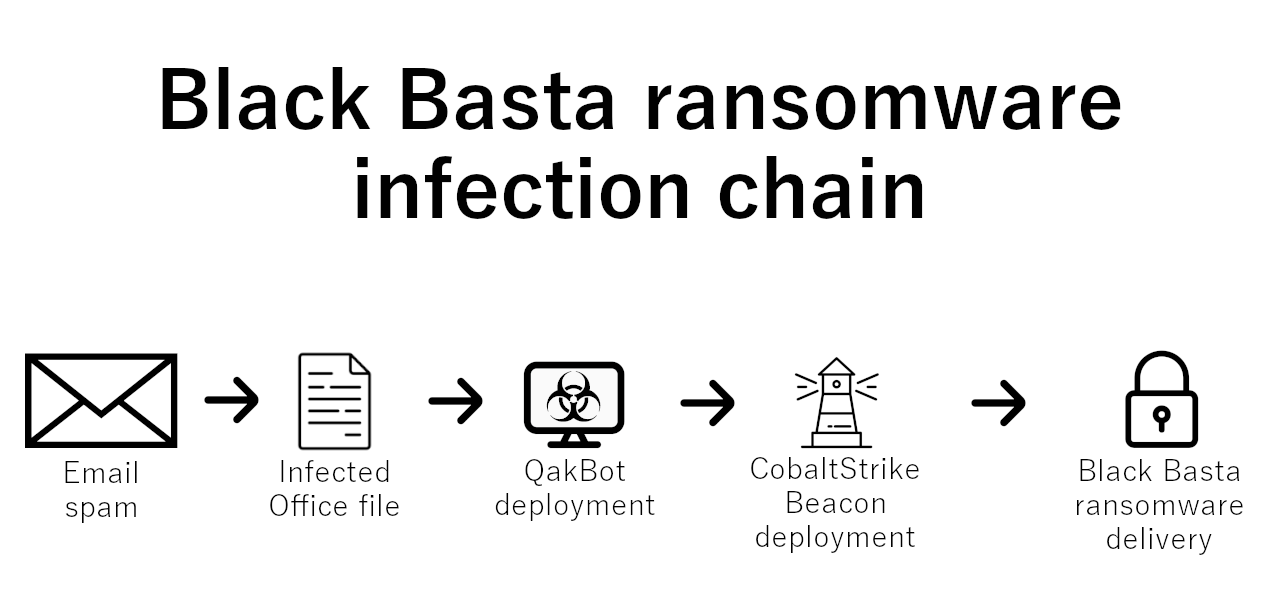
Over time, they developed a specific pattern of attack. First, they deploy the QakBot trojan using email spam. Crooks use a specific sample, coined BB20, controlled by themselves. Further, this malware connects to the command server and pulls the second-stage payload – Cobalt Strike Beacon. Advanced capabilities of the beacon allow hackers to perform lateral movement even before deploying the final payload. The final stage is, obviously, dropping ransomware on all the infected systems.