ESET experts have discovered the CloudMensis malware, which is used to create backdoors on devices running macOS and subsequently steal information.
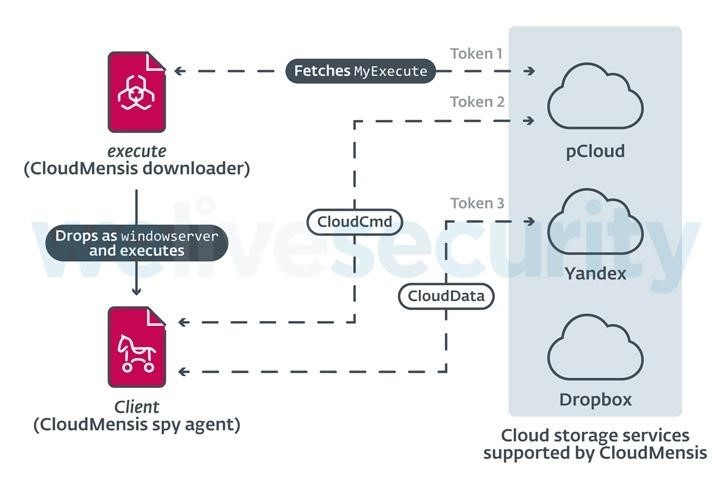
The malware received its name due to the fact that it uses pCloud, Dropbox and Yandex.Disk cloud storages as control servers.
Let me remind you that we also wrote that Vulnerability in macOS Leads to Data Leakage, and also that Microsoft Releases PoC Exploit to Escape MacOS Sandbox.
The capabilities of CloudMensis indicate that the main goal of its operators is to collect confidential information from infected machines. For example, the malware is capable of taking screenshots, stealing documents, intercepting keystrokes, and compiling lists of emails, attachments, and files stored on removable media.
CloudMensis supports dozens of different commands, which allows its operators to perform a variety of actions on infected machines:
- change in the malware configuration the cloud storage provider and authentication tokens, file extensions of interest, the frequency of polling cloud storage, and so on;
- make a list of running processes;
- to capture the screen;
- make a list of letters and attachments;
- make a list of files on removable media;
- run shell commands and upload the result to the cloud storage;
- download and execute arbitrary files.
According to ESET analysis, attackers infected the first Mac as early as February 4, 2022. Since then, they have only occasionally used the backdoor to compromise other machines, hinting at the targeted nature of this campaign.
Interestingly, once deployed, CloudMensis is able to bypass the Transparency Consent and Control (TCC) system, which asks the users if they need to grant the app permission to take screenshots or monitor keystrokes. The TCC mechanism is designed to block access to sensitive user data, allowing macOS users to customize privacy settings for various applications and devices (including microphones and cameras).
Rules created by the user are stored in a database protected by System Integrity Protection (SIP), which ensures that only the TCC daemon can modify them. Thus, if a user has disabled SIP on the system, CloudMensis will grant itself the necessary permissions by simply adding new rules to TCC.db.
However, even if SIP is enabled and any version of macOS Catalina prior to 10.15.6 is installed on the machine, CloudMensis can still gain the necessary rights by exploiting a vulnerability in CoreFoundation, which has the identifier CVE-2020-9934 and which Apple fixed two years ago. This bug will force the TCC daemon (tccd) to load a database that CloudMensis can write to.
The vector of infection, as well as the goals of the hackers, are still unknown, but the researchers write that, judging by the way the attackers handle Objective-C, they are practically unfamiliar with macOS. At the same time, experts admit that CloudMensis is still a powerful spy tool that can pose a serious threat to potential victims.




