On October 19, 2023, a group of international law enforcement orgs claimed the seizure of server infrastructure of the Ragnar ransomware gang. This appears to be a new trend, as it is the third widely-discussed infrastructure seizure over the last 2 months.
What is the Ragnar ransomware group?
Ragnar a.k.a.Ragnar_Locker or RagnarLocker is a cyber extortion gang that runs ransomware attacks on corporations. Doble extortion, ransom sum negotiated on the Darknet page – quite common practices among modern hacker groups. However, the gang is not likely to operate on the Ransomware-as-a-Service model – the one that is used by the vast majority of other gangs.
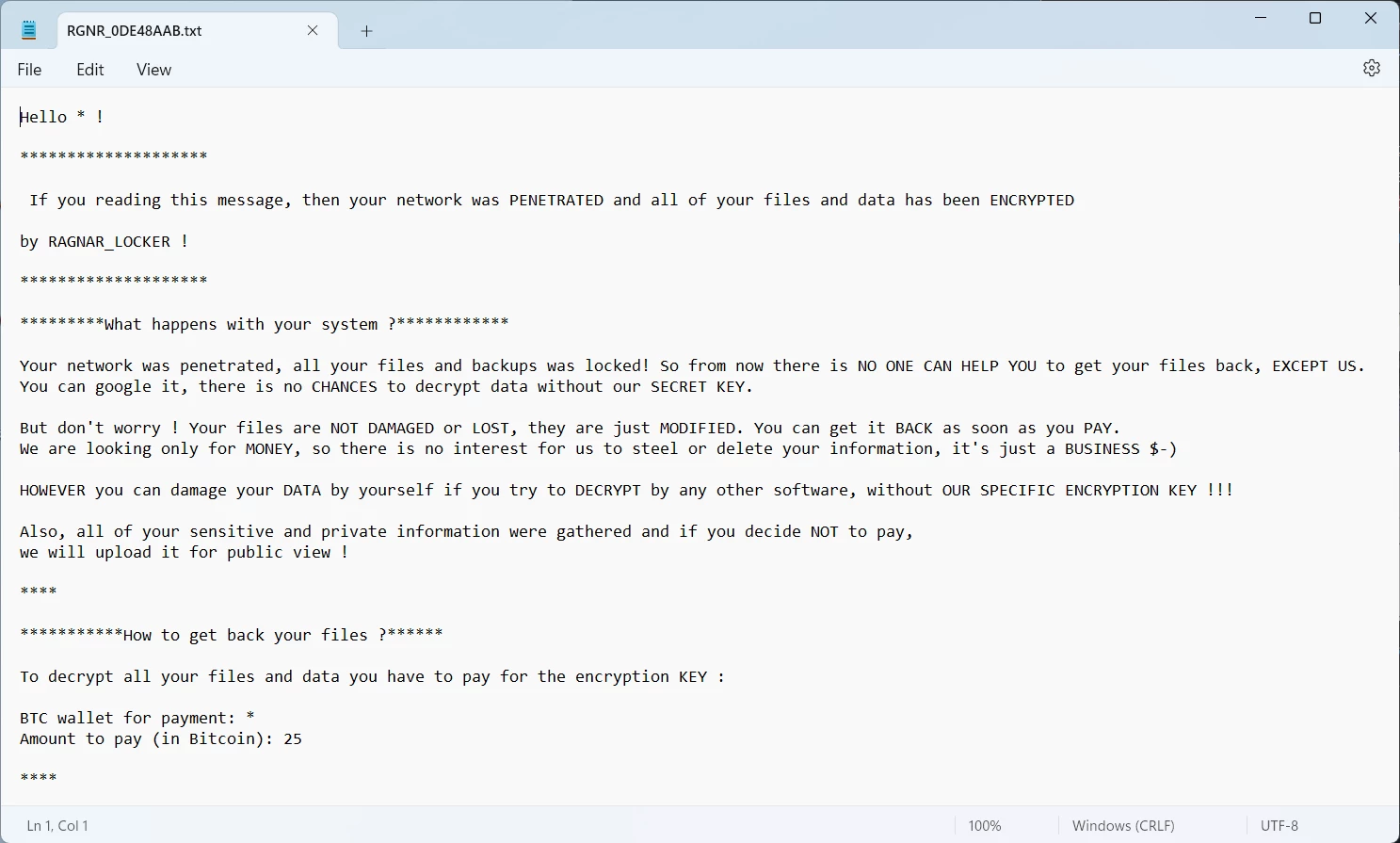
Key attack vectors used by these hackers consist of exploiting vulnerabilities in network protocols or cloud applications. Additionally, Ragnar is known for cooperating with cybercriminals who provide initial access. During their attack, ransomware deployment is not mandatory – there were cases when the attack was only about data exfiltration.
But why did law enforcement pay so much attention to RagnarLocker? Well, the answer becomes obvious when you have a look at the victims of this ransomware. Capcom, Campari, City of Antwerp, Energias de Portugal, ADATA – these and numerous other companies/municipalities were struck. It was not just about spooking small companies – they were regularly opting for serious targets.
RagnarLocker Shut Down By the FBI & European Law Enforcement
On October 19, Europol claimed the disruption of Ragnar Locker ransomware operations as the result of a successful operation. The latter consisted of locating and seizing the servers which belonged to the ransomware gang. This method repeats the one used by the FBI in the operation Duck Hunt, that took down the entire QakBot botnet in late August 2023.
Another similar event occurred days ago, when the Ukrainian Cyber Alliance wiped the network infrastructure of Trigona Ransomware. As I said in the introduction, this appears to be a new trend. And its adoption is understandable – it is much faster and still effective compared to detaining the key actors of the organised crime gang.

Currently, the visible effect of the infrastructure takedown is the banner on the Darknet negotiation site of RagnarLocker. Taking hands on the network infrastructure means not only making malware operations impossible. Most likely, all the decryption keys, along with the decryptor utilities hackers were offering for hundreds of thousands of dollars, are now in hands of law enforcement.
Is this the Ragnarok for Ragnar Locker?
The effect from complete confiscation of network infrastructure is hard to underestimate. Even though threat actors are not detained and can keep working, there is a lot of work to recover the servers. Moreover, the funding during this recovery is questionable – law enforcement could have accessed hackers’ crypto wallets as well.
My guess is that group members will simply move to other ransomware gangs, abandoning their own one. RagnarLocker never showed its passion towards the brand name, so there won’t be many stopping factors against this step. Though, we haven’t seen “full-fledged” gang dissolutions since Conti shutdown in 2022. Maybe, it will be different this time?

