Akamai has identified a new phishing kit that is being installed on hacked WordPress sites and targets PayPal users.
The malware tries to steal the personal information of the victims, and also asks to take a selfie with identity documents.
Let me remind you that we also wrote that Iranian Spear-Phishing Operation Targets US And Israeli High Executives, and also that Ukrainian Cyber Police Arrested the Author of uPanel Phishing Kit.
The new threat was discovered after attackers infected researchers’ honeypots with it. Apparently, the attackers break into any poorly protected WordPress sites using lists of common logins and passwords. Once they break into someone else’s site, hackers use access to install a file management plugin that allows them to download a phishing kit.
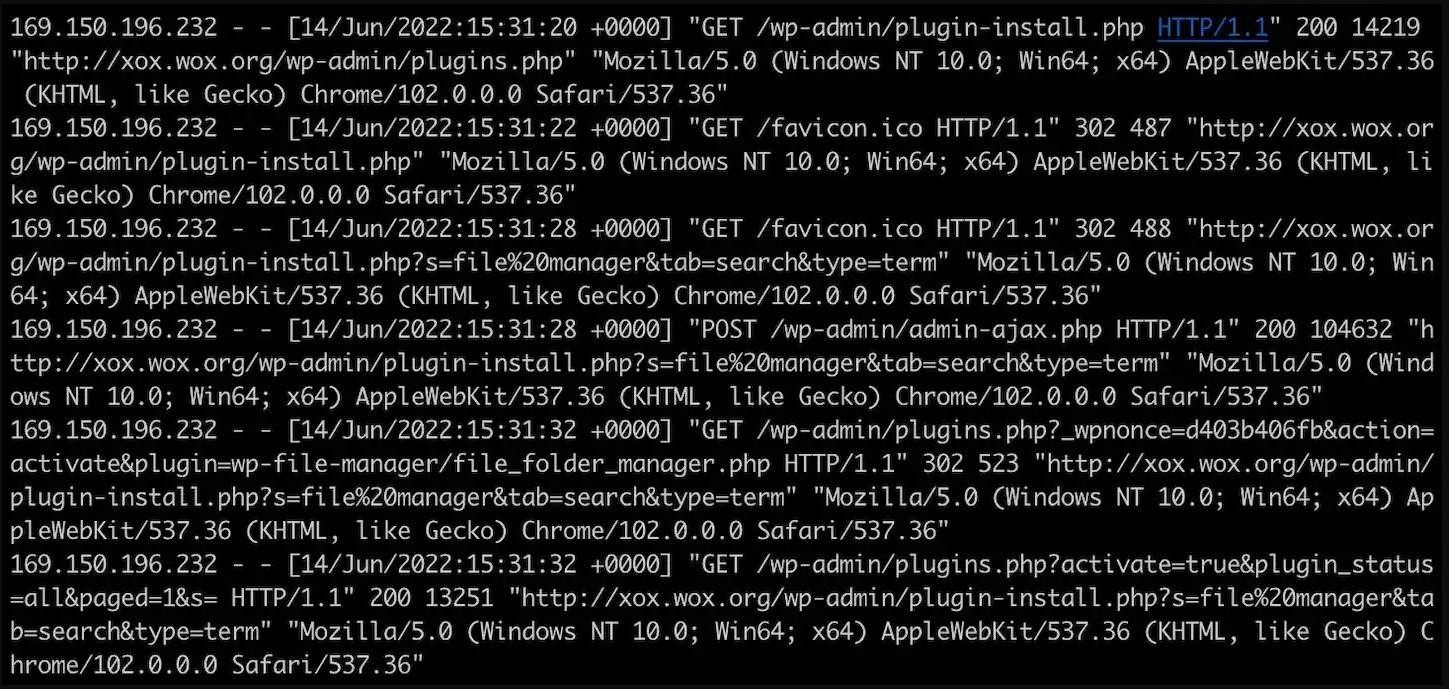
The developers of this phishing kit have tried to make their fraudulent page look professional and completely imitate the real PayPal website. So, the malware author even uses htaccess to rewrite the URL so that it does not end with a PHP extension.
The victim’s identity theft begins with a CAPTCHA that the user is asked to solve. Analysts say the move creates a false sense of legitimacy for victims. The victim is then prompted to log in to their PayPal account, and the credentials are, of course, automatically transferred to the attacker.
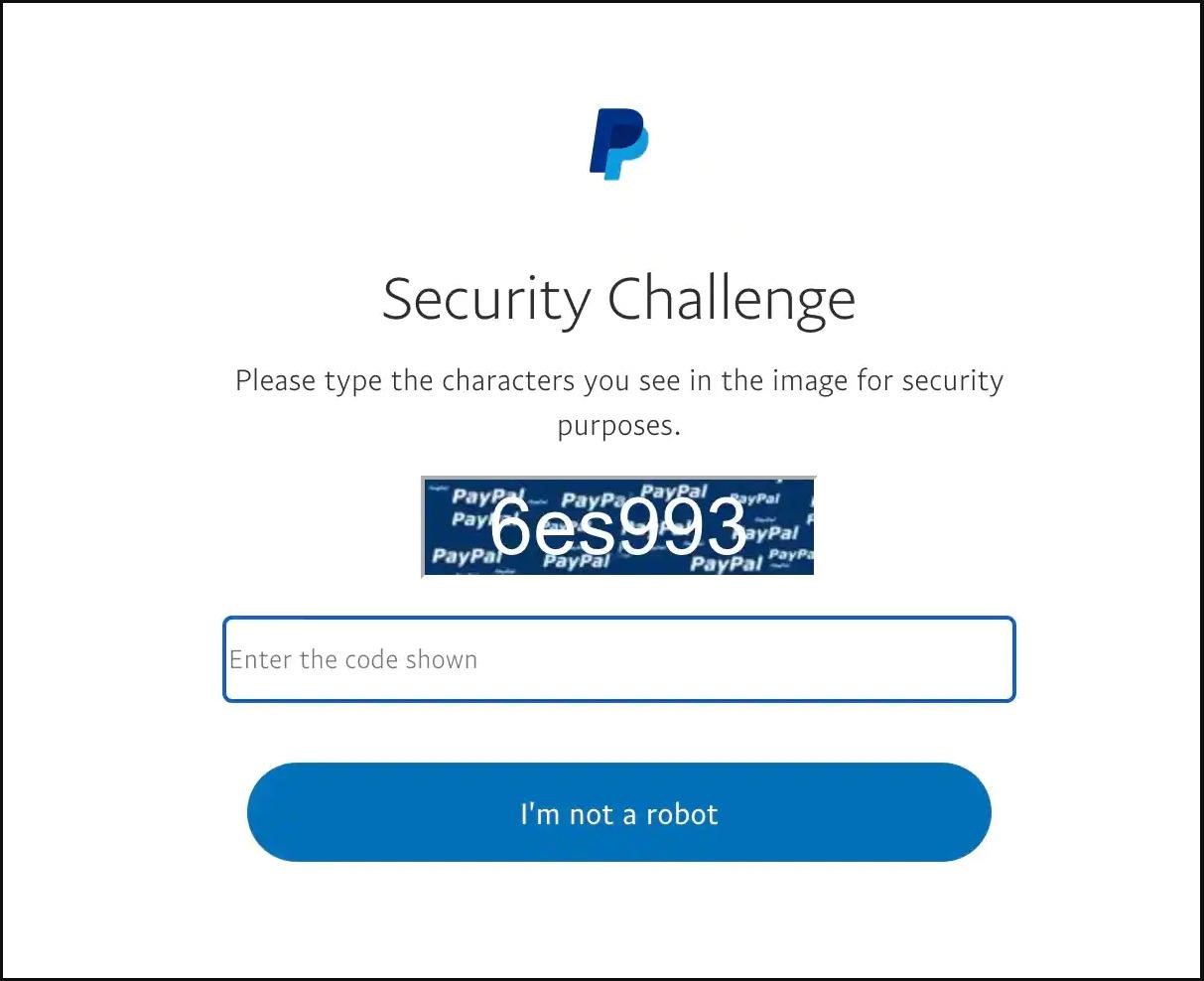
However, this is just the beginning of the scam. Further, the phishing page informs that suspicious activity was allegedly detected in the victim’s account, and now the user needs to provide additional information for verification. As a result, the victim is asked to provide a lot of personal and financial information, including payment card details (including the CVC code), physical address, social security number, and even the mother’s maiden name.
Collecting so many different data is not a common practice for phishing kits, but the attackers do not even stop there and ask the victim to link an email account to PayPal. As a result, hackers receive a token that can be used to access the contents of the provided mailbox.
And finally, in the last stage of the attack, the user is asked to take a photo with official identification documents. The hackers accept passports, other government-issued IDs, and driver’s licenses, with detailed instructions on how to download them.
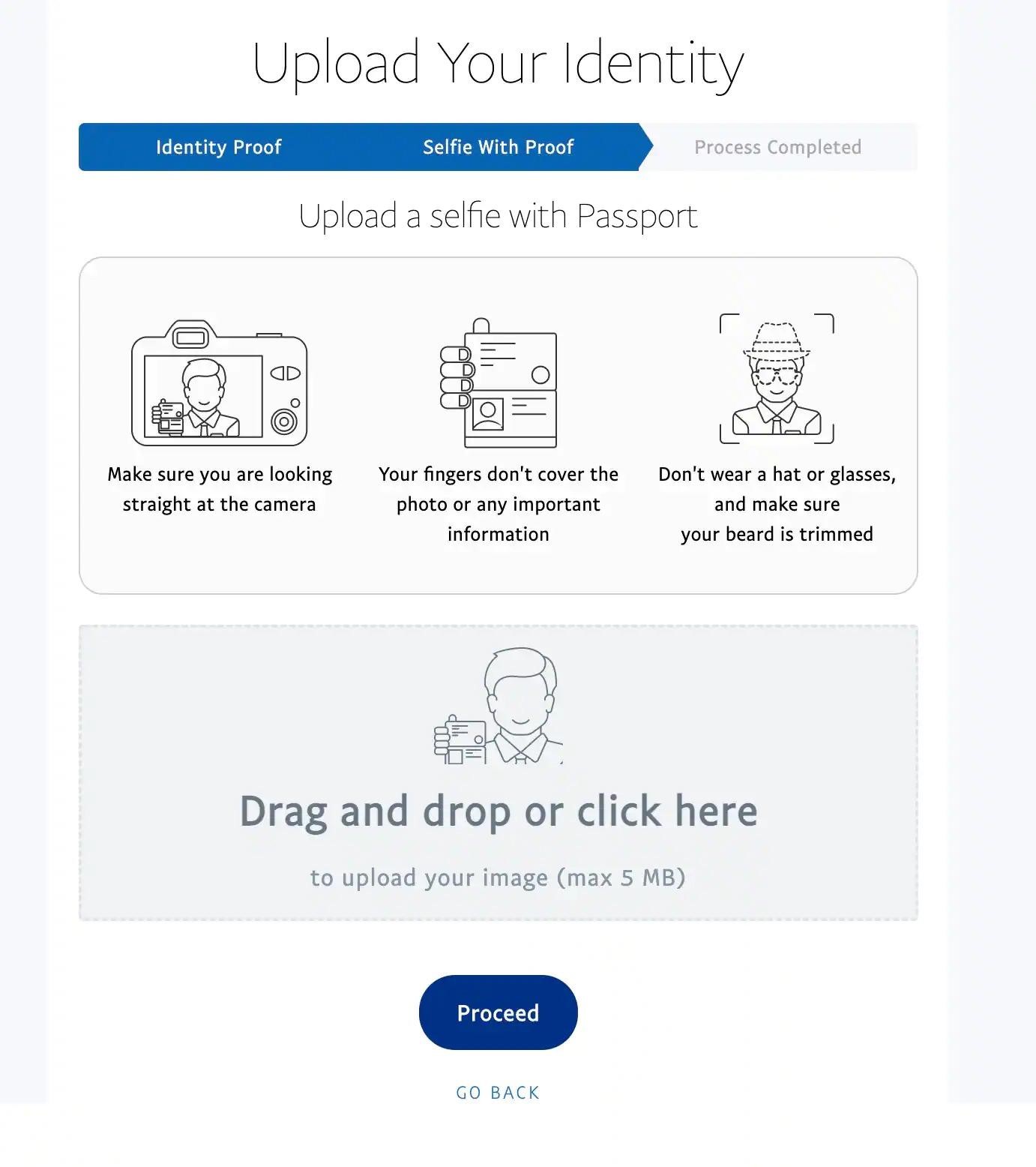
Akamai experts note that all this information can be used by attackers for a variety of illegal activities – from identity theft to money laundering (for example, creating cryptocurrency trading accounts, registering companies), from maintaining anonymity to seizing bank accounts or cloning payment cards.
Although this scam may seem too clumsy and obvious to many, Akamai researchers assure that social engineering makes this phishing kit very effective. They explain that identity verification is commonplace these days and can be done in a variety of ways, and the phishing kit mimics some of the real PayPal verifications quite successfully.




