In a wake of rising tensions between Israel and Iran, researchers from Check Point Research (CPR) discovered numerous attempts of spear phishing attacks from the supposedly Iranian Phosphorus APT group.
Researchers also assume that the activity might have been conducted earlier, but so far they traced back it to at least December 2021. It is believed that among the goals of the operation was to steal passport scans, access to email accounts and personal information.
Many high profile targets of the operation included people like:
- Senior executive that works in the Israeli defense industry;
- Former Chair, that once worked at one of the most known Middle East research centers;
- A person, who was Former US Ambassador to Israel;
- Chair, that currently works in one of Israel’s leading security think tanks;
- Former Major General, who once had the position in a high position at the IDF (Israel Defense Forces);
- Tzipi Livni, who was a former Foreign Minister and Deputy Prime Minister of Israel.
To conduct the attacks, threat actors took control over existing email accounts of senior officials and pretended to be them engaged in long correspondence with targets or inserted themselves into existing conversations between executives and other persons.
It’s not the first time Israeli officials have become targets to Iranian threat actors via email attacks
The spoofed emails in the attack included phishing pages from Yahoo, links to upload some documents’ scans, faked invitations to a conference or research or links to other real documents relevant to the target.
One of Israeli former high officials who was Israeli Former Foreign Minister received one of the faked emails coming from another senior official who was a well known former Major General in the IDF.
The email appeared to have a genuine address and which the Former Foreign Minister had correspondence in the past with.
Tzipi Livni, Former Israeli Foreign Minister was approached by someone via a hijacked email account of a former Major General in the IDF with a link to a file which she was asked to open and see.
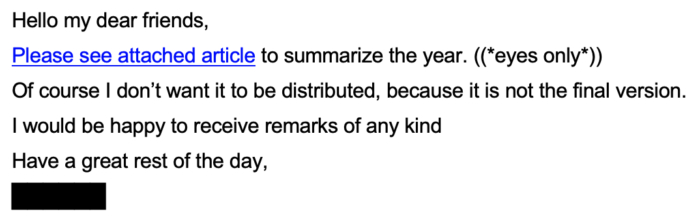
When she postponed the action she was approached again with another email from the same address asking her again to open the email. This brought some suspicions to the former executive.
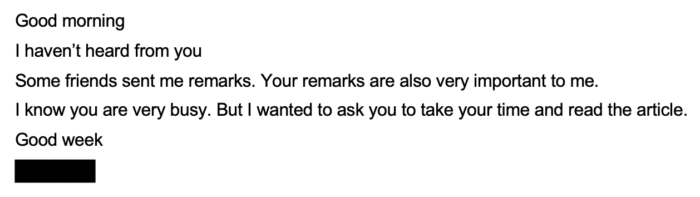
She met the former Major General in person and asked about the emails which turned out he never actually sent.
Iranian Phosphorus APT group is supposedly behind these spear phishing attacks
CPR researchers assume that an Iranian-backed entity is responsible for the attacks. They note that all possible evidence points to the operation of the Iran-attributed Phosphorus APT group.
This well known group has a long history of targeting high profile officials mainly from Israel thus propagating the interests of the Iranian regime.
How To Recognize Phishing Emails
But not only high profile officials can be the targets of phishing because ordinary people also become one. To know if you possibly received a phishing email look for the next signs to confirm or discard suspicions:
- Fake Domains. If you received some unexpected email and you are not sure if it’s legit the best first thing would be to look at its domain where this email came from. Often to downplay your attention, threat actors will create domains that at a first glance look like legit one which in reality aren’t.
For example, you may receive an email from what appears to be the lionsbank.com domain of your bank but if you look closely you may spot a difference. Instead of lionsbank.com it can be something like lionsdank.com; - Suspicious Requests. Phishing emails exist to steal your personal information, money, credentials and if you are asked to produce one of those or other unusual or suspicious requests the sure thing is that you’re dealing with a phishing email;
- Psychological Tricks. If you feel that the email you received reads a little coercive it means that most likely you’re dealing with phishing. They urge you to do something, even threaten with some legal consequences to do what the email asks. No doubt it’s a phishing.
What Other Sings Hint At Phishing
First of all, the received email gives you a sense of urgency.
Recipients are advised that something needs to be done right away unless you don’t want unpleasant consequences.
It is done so because a person in a hurry is less likely to think of the genuity of the received email.
The second popular phishing trick is to send email from some authority. In this case most likely threat actors will conduct business email compromise (BEC) scams and similar spear phishing tricks that are commonly disguised as if to be sent from a CEO or someone else in authority.
Phishing emails with such tone prove the fact that people are sometimes too inclined to believe emails coming from someone in authority to be surely legit.
Another popular method among threat actors but usually not among those targeting high profile persons is to threaten a recipient or blackmail them.
They put a requirement that if a recipient doesn’t do what they ask they will either leak some sensitive information or destroy other valuable information.
Fear is what in such cases makes the phishing attempt successful. People fear to be punished or feel embarrassment and that’s what makes the recipient comply with phishers’ requests.
And the last thing to mention is that if you suspect that the email you received might be phishing it will be better not to do anything with it. Don’t open any attachments, don’t click on any links in it and, of course, don’t reply with anything.
It will be better just to delete that email or report to the IT team if you received such an email at work.




