Intruders try to keep up with the development in the digital world. The technology seeks to provide users with more effective resources, but the attackers in turn try to come up with even more sophisticated methods of cyberattacks.
The two types of attack are Phishing and Pharming. Here we consider their characteristics and the difference between them. The work principle of these two attack types is completely different and the methods are different, but their goal is to harm the user, steal his data and use it in their evil intentions.
What is Pharming?
Pharming is a kind of cyber theft, also it is better to call it a type of fraud, through which a hacker fraudulently forces the user to go to a website that will pose a threat to him. In the process of pharming, the hacker installs the malicious software into the victim’s system, after which this pest directs the user to the infected websites. These websites are disguised as legitimate, so when users switch to them, they are not aware that they endanger their operating systems.
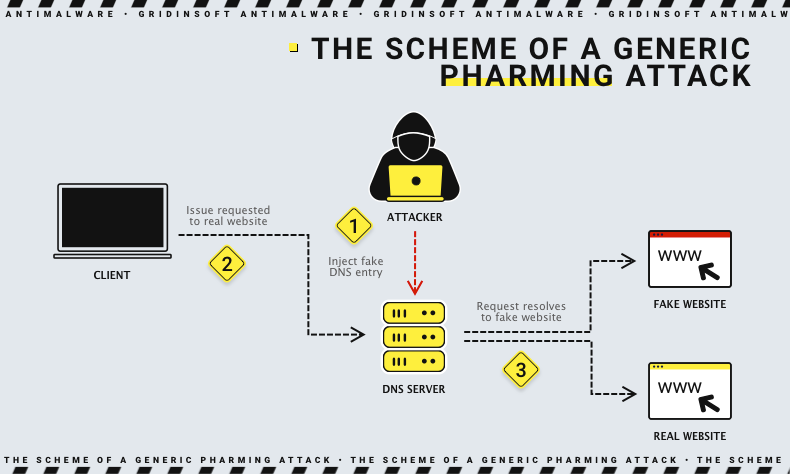
The objective of the attacker is to collect the user’s personal data, financial and confidential information and use it for further actions. If the attacker has managed to hack the DNS server or a domain name, then a simple click on the link will redirect the user to the site altered by the attackers.
Related Content: QR code phishing is very similar to other forms of phishing. It is a social engineering attack designed to trick people into handing over personal information, be it login credentials or financial information.
This attack works so cleverly that the user will initially be unaware whether he is entering data on a fake site or on a legitimate one. The only thing that can give out pharming is that the request to fill in personal data will be in the form of a pop-up window.
What is Phishing?
Phishing is a type of attack aiming to steal user data. It works through social engineering, that is, deception of the user. This often happens through e-mails in which a fake company pretends to be legitimate and requests confidential information about the victim. The process is very simple: in the letter, you can see the attached link that you will be persuaded to click on, and then you go to the malicious resource. Phishing might also look for vulnerabilities in your security system, after which it will install its malicious software.
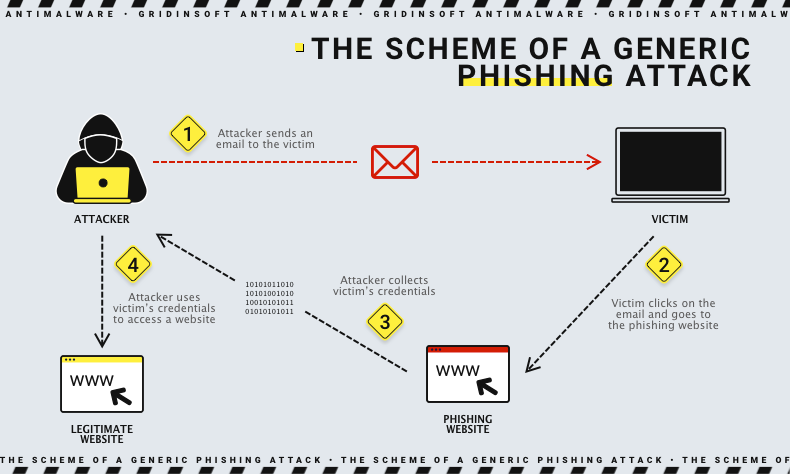
Phishing can spread not only through e-mail but also through voice and text messages. Through these types of phishing, many data leaks were made.
Examples of Phishing and Pharming
Below we consider examples of the most common phishing attempts.
- Through the Bank. In this case, fraudsters try to steal financial data from the user under the guise of bank employees.
- Spam messages. This is a mailing to a huge number of users from an allegedly authentic source.
- Through an email stating that your password is out of date and needs to be updated. To do this, you need to follow the link and update it.
Examples of pharming are as follows:
- When users log on to a legitimate site, they land on a fake one, although they have entered a request to a completely legitimate website.
- Changed DNS routers, unbeknownst to the user.
Phishing and Pharming Techniques
To make their attack more sophisticated, the attackers invent different methods for this, resulting in different types of the same attack. Therefore, they work on different platforms and through different services. Below we present several basic types of Phishing and Pharming.
Phishing Attack
Here we consider the types of phishing and their features:
- Spear Phishing – this type of phishing is aimed at a specific user, a specific hacker for a specific purpose. The goal is to steal data that will lead to financial gain and more.
- Clone Phishing – this type of attack involves cloning already available information. A hacker uses the email of a reliable source, modifies the created letter, and introduces malicious links, through which it can distribute malicious software to the user’s device.
- Catphishing – This method is most often used through dating sites, where fraudsters deceive their victims for financial and personal information.
- Voice Phishing – in this case, the user is received through a call. The fraudster makes a design of the caller ID because of which the user does not know what takes a call from the fraudster. Thus personal information about the user, his credit data, and finances can fall into the hands of the intruder.
- SMS Phishing – this type of attack provides a threat via text message. An attacker tries to reveal confidential user data via text messages.
Pharming Attack
This attack is aimed at harming the user. This happens when a user goes to a fraudulent website, thereby launching malware on his device.
Pharming can occur through two main methods:
- Through software vulnerabilities in the DNS server.
- By modifying the Hosts file on the user’s computer.
Pharming attacks can occur not only in different methods but also in different places and cases. Below we will discuss a few points through which pharming manifests itself if occurred on:
Client-Side
- Local hosts as the attack target
- Home router as a target
- Target of the proxy browser attack-configuration
Server-Side
- An attacker sends a DNS cache server to insert fraudulent records.
- There is transparency between the proxy server and the Internet user.
What is the difference between phishing and pharming?
Above we have reviewed the characteristics and types of phishing and pharming. We have already considered that these are types of cyberattacks, now let’s look at the difference between them.
| Parameters | Pharming | Phishing |
| Definition | A more sophisticated method for obtaining user data in which an attacker uses DNS servers to direct users to fake websites that pose a threat to the user and its device | Method of obtaining user data, through electronic communications (e-mail, phone numbers) |
| Objective | Steal data by redirecting the user to other traffic | Steal users’ confidential, financial data, via instant messaging or email |
| Category | A kind of cyber attack, a bit like phishing because of the use of email | Email fraud |
| Process | In a process of pressure or manipulation, the attacker forces the users to release their confidential data | The attacker receives data through domain spoofing, DNS interception, poisoned cache, and others |
| Difficulty Level and Detection | Easier to identify and execute | Harder to identify and execute |
| Technique | Users are redirected to another site via poisoned DNS | Users get to malicious sites through malicious links in emails from intruders |
| Medium | Fax, instant messaging, and email | Websites, local host files, DNS servers, home routers, and more |
How to avoid phishing and pharming?
We have considered all the characteristics, types, and methods of operation of such cyber attacks as phishing and pharming. Whether they are similar or not, the only thing that matters is that they are dangerous to your device and to your confidential data. This should be considered and precautions should be taken. Remember to check HTTPS in the email and URLs. Set yourself up with protection that will alert you to perceived threats. Try not to visit suspicious sites, do not click on everything that comes to you in emails, use antivirus, and do not share your confidential and financial information with everyone.