What is DNS Spoofing?
DNS (Domain name server) spoofing or DNS cache poisoning is a type of cyberattack used by an attacker to direct the victim’s traffic to a malicious website (instead of a legal IP address). Attackers use DNS cache poisoning to redirect Internet traffic and steal sensitive information.
For example, a hacker wants to trick users into entering personal information on an insecure site. How does he do that? By poisoning the DNS cache. The hacker spoofs or replaces the DNS data for a specific site and redirects the victim to the attacker’s server instead of the legitimate server. In this way, the hacker achieves his goal because he has many opportunities: he can commit a phishing attack, steal data or even inject malware into the victim’s system.
How Does DNS Spoofing Work?
Before talking about DNS cache poisoning, let’s first remember what DNS and DNS caching are. DNS is a worldwide directory of IP addresses and domain names. DNS pairs user-friendly addresses, such as facebook.com, into IP addresses, such as 157.240.22.35, that computers use on the network. DNS caching is a system for storing addresses on DNS servers worldwide. To speed up the processing of your DNS requests, developers have created a distributed DNS system. Each server keeps a list of available DNS records called a cache. If the DNS server closest to you does not have the required IP address, it queries the higher DNS servers until the address of the website you are trying to get to is not found. Your DNS server then saves this new record in your cache to get a response faster next time.
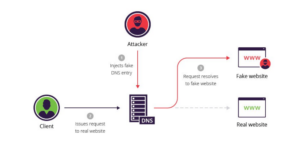
Unfortunately, DNS has several security flaws that attackers can exploit and insert forged Internet domain address records into the system. Typically, criminals send fake responses to the DNS server. The server then replies to the user who made the request, and at the same time, the legitimate servers will cache the fake record. Once the DNS cache server stores the fake pair, all subsequent requests for the compromised record will get the server’s address controlled by the attacker.
DNS Spoofing Techniques Can Include:
- Man in the middle (MITM) – The cybercriminal intercepts the traffic and passes it through his system, collecting information as he goes or redirects it elsewhere.
- DNS server compromise – directly hijacking the DNS server and configuring it to return a malicious IP address.
Cybercriminals can easily compromise DNS responses while remaining undetected due to security vulnerabilities in specific web applications and the lack of proper authentication of DNS records. Let’s take a closer look at them:
Lack of Verification and Validation
DNS has a first trust structure that does not require IP validation to verify before sending a response. Because DNS resolvers do not validate data in the cache, an invalid entry remains until it is manually deleted or the TTL expires.
Recursive DNS Resolver Vulnerability
When recursive querying is active, the DNS server receives the request and does all the work of finding the correct address and sending the response to the user. If it does not have a record in its cache, it will query other DNS servers until it gets the address and returns it to the user. Enabling recursive querying presents a security vulnerability that attackers can exploit to poison the DNS cache.
As the server looks for the address, the attacker can intercept the traffic and provide a fake response. The recursive DNS server will send the response to the user and simultaneously store the spoofed IP address in its cache.
No Encryption
Typically, the DNS protocol is not encrypted, making it easier for attackers to intercept its traffic. In addition, servers do not have to verify the IP addresses to which they route traffic. Hence they cannot determine whether it is genuine or spoofed.
How to Prevent DNS Spoofing?
Real-time monitoring of DNS data can help identify unusual patterns, user actions, or behaviors in traffic, such as visiting malicious sites. And while detecting DNS cache poisoning is difficult, there are several security measures companies and service providers can take to prevent it. Some measures to prevent DNS cache poisoning include using DNSSEC, disabling recursive queries, and more.
The Limit of The Trust Relationships
One of the vulnerabilities of DNS transactions is the high trust relationship between different DNS servers. Therefore, servers do not authenticate the records they receive, allowing attackers to send fake responses from their illegitimate servers.
To prevent attackers from exploiting this flaw, security groups should limit the level of trust their DNS servers have with others. Configuring DNS servers to not rely on trust relationships with other DNS servers makes it difficult for hackers to use a DNS server to compromise records on legitimate servers. There are many tools available to check for DNS security threats.
Use the DNSSEC protocol
Because Domain Name System Security Extensions (DNSSEC) uses public-key cryptography to sign DNS records, it adds validation and allows systems to determine whether an address is valid or not. This prevents forgery by verifying and authenticating requests and responses.
In regular operation, the DNSSEC protocol associates a unique cryptographic signature with other DNS information, such as CNAME and A records. The DNS resolver then uses this signature to authenticate the DNS response before sending it to the user.
Security signatures ensure that a legitimate source server validates responses to requests that users receive. Although DNSSEC can prevent DNS cache poisoning, it has drawbacks such as complex deployment, data provisioning, and zone enumeration vulnerabilities in earlier versions.
Use The Latest DNS and BIND Versions Software
Beginning with version 9.5.0 BIND (Berkeley Internet Name Domain) includes enhanced security features such as cryptographically secure transaction identifiers and port randomization, which minimizes the chance of DNS cache poisoning. It is also important that the IT staff keeps it up to date and ensures that it is the latest and safest version. Here are some more useful tips to help prevent DNS cache poisoning.
- Configure the DNS server to respond is exclusively related to the requested domain.
- Make sure that the cache server only stores data related to the requested domain.
- Forced to use HTTPS for all traffic.
- Disable the DNS Recursive queries.
DNS cache poisoning causes domain users to be redirected to malicious addresses. In addition, some attacker-controlled servers can trick unsuspecting users into downloading malware or providing passwords, credit card information, and other confidential information. To prevent this, it is essential to use reliable security methods.




