Data Loss Prevention (DLP) is a method of detecting data loss and preventing a given case, including awareness of the protected content or context. It also includes using tools that protect your personal data or avoid data leakage in some way.
It is straightforward to understand how this happens:
- Data loss – is the situation when a pest program attacks.
- Data loss prevention – is a precaution to prevent an attacker from stealing data at the slightest attempt.
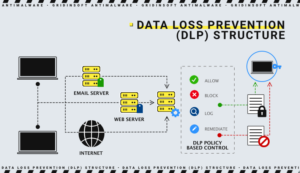
Causes of Data Leaks
Data breaches (or data leakages) can occur for the most inexplicable reasons; in our article, we will highlight three main reasons, see below:
- Extrusion by attackers. Most cyber-attacks are aimed at stealing sensitive data. It happens through malware, phishing, and embedded codes. The intruders thus infiltrate your PC and steal what they need, then use it for their evil intentions.
- Insider threats. An internal intruder who accesses your data and misuses it.
- Unintentional or negligent data exposure is due to the negligent treatment of its data. Users do not restrict access to their data as required by the privacy policy, resulting in their data loss.
- Too Many Permissions.This reason will amuse the hacker. Don’t give anyone permission to access your data and generally control to whom you give permission. Also, do not use unauthorized permissions that will no longer have the capacity to protect your data.
- Improper Configuration, User Error. To ensure that this feature does not interfere with you and does not lead to data leakage, use appropriate protection to prevent different types of errors.
- Weak and Stolen Credentials, a.k.a. Passwords. A common reason for hacking is a weak and unreliable password. It is easy for hackers to crack an unprotected system with a reliable password. Statistics show that the most common hack happens because of this. So be careful; put complex, strong passwords.
Causes of Data Loss
To know how to solve the problem of data loss, you need to understand what is at stake and why. Below we list the most common causes of data loss:
- Hard drive malfunction. One of the common causes of data loss is a hard drive malfunction. It is due to improper use of the hard drive. That’s because of the power surges, the external damage, the uneven load, and the overheating. To recover lost data on your hard drive, you will need the help of a professional who knows it. The solution can be to create regular backups. Your saved data in a secure repository is the solution to a corrupted hard drive.
- Power Outage. Power outages can abruptly interrupt all your operations, which will disrupt the software. However, the power failure itself will not lead you to permanent data loss; your computer may not correctly shut down, after which the hard drive will give frequent system failures.
- Human factor. Everything here is as unforeseen as possible. Here everything can begin with an accidental removal and end with physical damage. In this case, store all the data in cloud storage and do not put your technique near drinks and products; put it better in a safe place.
- Theft and Destruction. The theft and theft of equipment are not up to you, and they will not prevent even antivirus software. You don’t know what might happen to your computer, so back up and store all your data in cloud storage.
- Cybercrime. These are various attacks from cybercriminals, virus software, and phishing. If all of the above threats get into your operating system, they can steal your data and use it in their evil thoughts. To avoid this, use a firewall and antivirus software to protect your PC from data loss threats.
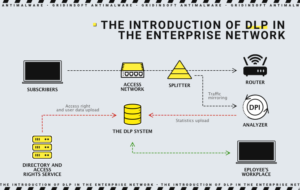
The introduction of DLP in the enterprise network
Data Leakage Prevention
To prevent data leakage, you can use standard and reliable methods. Here we will look at what are the options to prevent data leakage. Below we will give you some recommendations in this regard.
- Backup operations Perform regular backup operations, preferably weekly.Backups should be stored on other servers or at least on external drivers.
- Antivirus Software. The antivirus will protect against the attempt to get to the data by preventing the attacker from running. If you haven’t already installed antivirus software, it’s time to do so. It will help you protect your operating system from pests. But if you already have installed antivirus software, try to update it as new updates become available.
- Firewall. It is an essential barrier between you, your computer, and intruders. A firewall will prevent dangerous external traffic from getting into your PC network. Install new updates on the operating system.
- Robust password system. Set complex passwords. You can also set two-factor authentication for better protection. Try not to specify your cat’s identity, deposit, or name during password creation. Make it more unique and complex. Recommend changing your password from time to time.
- IDS is an intrusion detection system. It will warn you about potential intruders who are trying to log in illegally to you in the system.
Components of a Data Loss Solution
There are several compilations from which data loss protection comes.
- Securing data in use systems can detect unauthorized action in the release between users. Whether unintentionally or intentionally.
- Securing data at rest stores protects and gives access to the encryption of archived data.
- By securing endpoints based on endpoints, agents can manage and control data transmission between users. These systems are designed to prevent otherwise, or more precisely block, the transmission of data between users.
- Securing data in motion is an installed technology on the border that analyzes traffic to detect sensitive data sent outside of the privacy policy.
- Data identification. Examine the status of your data. Whether they need protection in principle, data privacy can be defined in several ways: automatically-machine, metadata, and rules manually.
- Data leak detection security systems that notify about data leaks. These are such as IPS, SIEM, and IDS.




