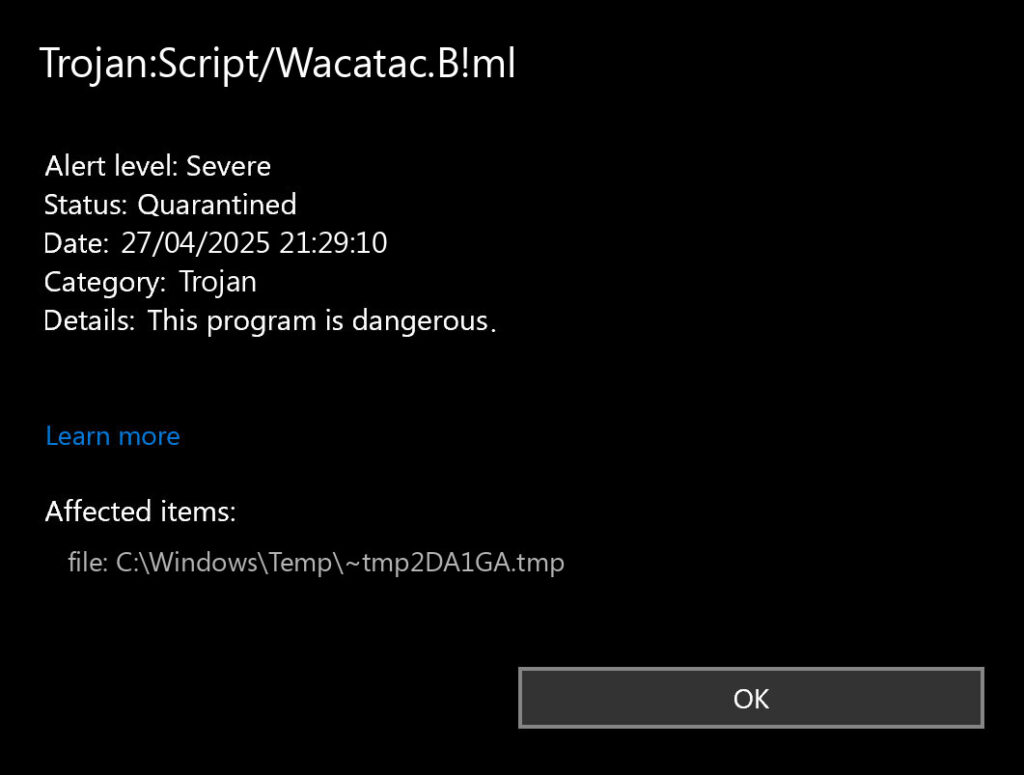
If you’re seeing “Trojan:Script/Wacatac.B!ml” detected by Microsoft Defender and wondering whether your computer is actually infected, this guide will help you determine if it’s a real threat and remove it completely. Don’t panic—while this can be legitimate malware, many detections are false positives, especially with development tools and certain applications.
This step-by-step removal guide will show you exactly how to eliminate Trojan:Script/Wacatac.B!ml from your system using both manual methods and automated tools. Whether you’re dealing with a real infection or a false positive, you’ll have your computer clean and secure by following these instructions.
Threat Summary
| Detection Name | Trojan:Script/Wacatac.B!ml |
| Threat Type | Script-based Trojan / Malicious JavaScript/VBScript |
| Primary Function | Downloads additional malware, steals information, provides remote access |
| Common Sources | Email attachments, drive-by downloads, fake updates, bundled software |
| False Positive Rate | High (40%) – Frequently flags legitimate development tools |
| Risk Level | Medium to High – Entry point for more serious infections |
Quick Navigation
Is Your Detection Real or a False Positive?
Trojan:Script/Wacatac.B!ml is a script-based variant of the Wacatac malware family, written in scripting languages like JavaScript, PowerShell, or VBScript. Unlike its more dangerous cousin Trojan:Win32/Wacatac, this detection has a high false positive rate—approximately 40% of detections are false alarms.
Common false positive triggers:
- .NET 9 AOT binaries in ZIP files
- 7-Zip archives containing executable files
- Game emulators like Xenia
- Android APK files
- B4X development tools
Signs of a real infection:
- File detected in %TEMP% with random names like “t3mp_45fd.js”
- You don’t recognize the detected file
- Recent suspicious downloads or email attachments
- Computer showing slowdowns, pop-ups, or browser redirects
Manual Removal: Step-by-Step Instructions
If you’ve determined this is a real infection (not a false positive), follow these detailed steps to remove Trojan:Script/Wacatac.B!ml manually. This process will eliminate the malware completely from your system.
Step 1: Prepare Your System
Boot into Safe Mode with Networking:
- Press Windows key + I to open Settings
- Click on Update & Security → Recovery
- Under Advanced startup, click Restart now
- Choose Troubleshoot → Advanced options → Startup Settings
- Click Restart and press 5 for Safe Mode with Networking
Create a backup of important data to an external drive before proceeding with removal.
Step 2: Identify Malicious Processes
Open Task Manager and look for suspicious processes:
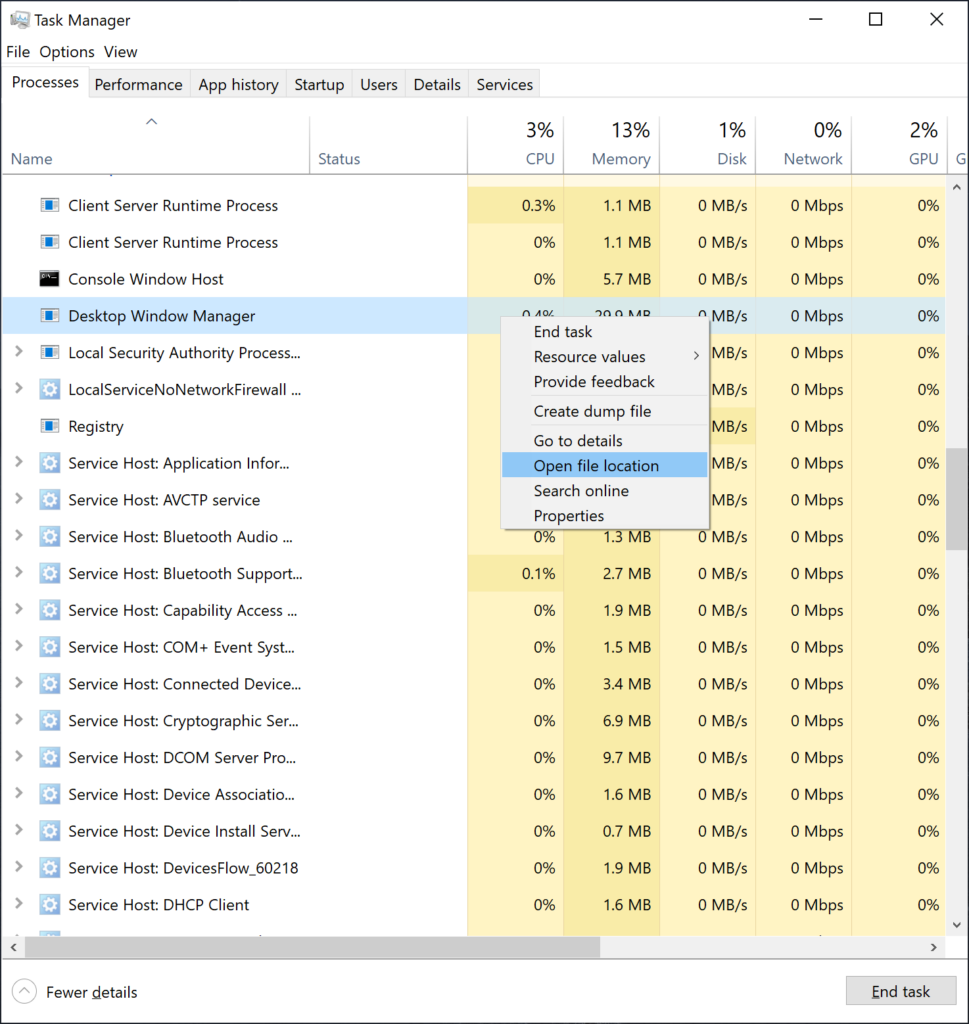
- Press Ctrl + Shift + Esc to open Task Manager
- Click the Processes tab
- Look for unusual processes with high CPU usage or random names
- Common malicious process patterns:
- Random letter combinations (e.g., “xyzabc.exe”)
- Scripts running through wscript.exe or cscript.exe
- PowerShell processes with encoded commands
- Right-click suspicious processes and select End task
- Note down the process names and file locations for later removal
Step 3: Remove from Startup Programs
Clean startup items in System Configuration:
- Press Windows key + R, type msconfig, and press Enter
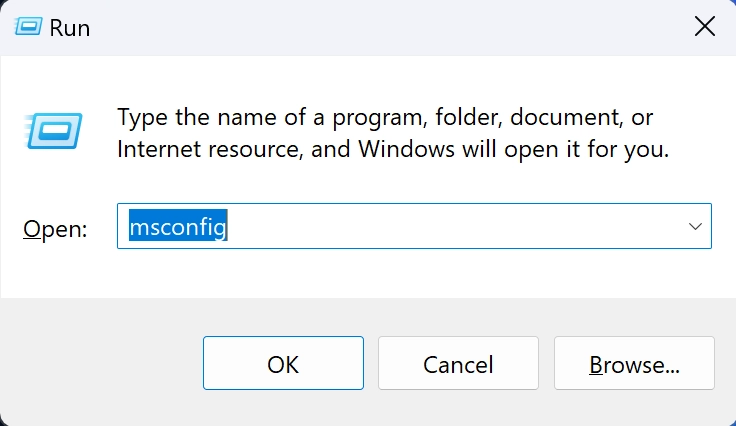
- Go to the Startup tab
- Look for unfamiliar entries, especially:
- Items with random names or no publisher information
- Scripts (.js, .vbs, .ps1 files)
- Files located in temporary directories
- Uncheck suspicious entries
- Click Apply and OK
Check startup folders manually:
- User startup folder: Press Windows key + R, type
shell:startup - All users startup: Press Windows key + R, type
shell:common startup - Delete any suspicious script files (.js, .vbs, .bat, .ps1)
Step 4: Delete Malicious Files
Search common infection locations:
Temporary folders (most common location):
- Press Windows key + R, type
%temp%, and press Enter - Look for recently created script files with suspicious names:
- Random letter/number combinations
- Generic names like “update.js” or “install.vbs”
- Files created around the time you first noticed the infection
- Delete suspicious files (right-click → Delete)
AppData folders:
- Press Windows key + R, type
%appdata%, and press Enter - Check these subfolders for malicious scripts:
- Roaming\Microsoft\Windows\Start Menu\Programs\Startup
- Local\Temp
- Any folders with random names created recently
- Delete suspicious files and folders
System32 and SysWOW64 (advanced users only):
- Check
C:\Windows\System32andC:\Windows\SysWOW64 - Look for recently created .js, .vbs, or .bat files
- Warning: Only delete files you’re certain are malicious—system files here are critical
Step 5: Clean Browser Settings
Google Chrome:
- Open Chrome, click the three dots menu → Settings
- Go to Advanced → Reset and clean up
- Click Clean up computer → Find
- Check Extensions – remove any you don’t recognize
- In Settings, go to Search engine and verify your default search engine
Mozilla Firefox:
- Open Firefox, click the menu button → Help → Troubleshooting Information
- Click Refresh Firefox to reset browser settings
- Check Add-ons and remove suspicious extensions
Microsoft Edge:
- Open Edge, click the three dots menu → Settings
- Go to Reset settings in the left menu
- Click Restore settings to default values
- Check Extensions and remove unknown ones
Step 6: Registry Cleanup
Warning: Editing the registry can damage your system if done incorrectly. Create a registry backup first.
- Press Windows key + R, type regedit, and press Enter
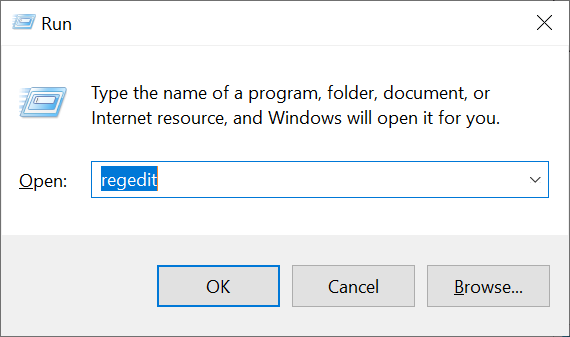
- Navigate to these autorun registry keys:
Check these registry locations:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnceHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Look for suspicious entries:
- Scripts (.js, .vbs, .ps1 files) in the data values
- Files located in temporary directories
- Random or generic entry names
- Right-click and delete suspicious entries
Step 7: Clean Task Scheduler
- Press Windows key + R, type taskschd.msc, and press Enter
- In Task Scheduler, click on Task Scheduler Library
- Look for recently created tasks with:
- Random or generic names
- Triggers set for login or system idle
- Actions running scripts or PowerShell commands
- Right-click suspicious tasks and select Delete
Step 8: Verification Scan
- Restart your computer in normal mode
- Open Windows Security (Windows Defender)
- Go to Virus & threat protection
- Click Quick scan or Scan options → Full scan
- Let the scan complete and remove any remaining threats
If manual removal seems too complex or you’re not comfortable with these steps, an automated solution can handle the entire process safely and efficiently.
Automatic Removal: The Faster, Safer Solution
Manual removal can be complex and time-consuming, especially for users who aren’t tech-savvy. If you want a faster, more reliable solution that detects hidden components manual removal might miss, GridinSoft Anti-Malware can automate the entire process for you.
This specialized anti-malware tool is specifically designed to detect and remove script-based threats like Trojan:Script/Wacatac.B!ml, including components that might be deeply embedded in your system or disguised as legitimate files.
Why Choose Automated Removal?
- Comprehensive detection – Finds malicious scripts hiding in obscure system locations
- Safe removal – Eliminates threats without risking system files
- Time-saving – Complete removal in minutes instead of hours
- Real-time protection – Prevents reinfection from similar threats
- User-friendly – No technical expertise required
Step-by-Step GridinSoft Anti-Malware Removal Process
Step 1: Download and Install
- Download GridinSoft Anti-Malware
- Run the downloaded installer as administrator
- Follow the installation wizard to complete setup
- The program will automatically update its malware definitions
Step 2: Run a Full System Scan
- Launch GridinSoft Anti-Malware from your desktop or Start menu
- Click on the “Scan” tab in the main interface
- Select “Full Scan” for the most thorough detection
- This scans all drives, system files, and hidden locations
- The scan typically takes 15-30 minutes depending on your system
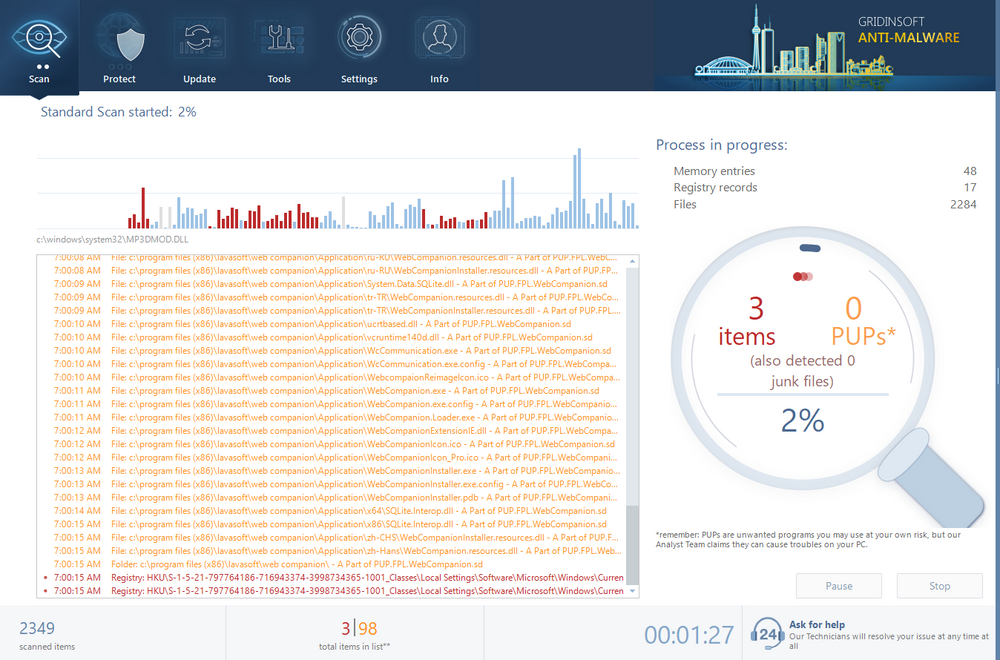
Step 3: Review and Remove Detected Threats
- Once the scan completes, you’ll see a detailed list of detected threats
- GridinSoft will automatically select all malicious items for removal
- Review the detection list:
- Trojan:Script/Wacatac.B!ml files will be clearly identified
- Related malware components will also be shown
- File locations and threat levels are displayed
- Click “Clean Now” to remove all selected threats
- The program will quarantine malicious files safely
Step 4: Restart and Verify
- Restart your computer when prompted (this finalizes the removal process)
- After restart, run another quick scan to confirm complete removal
- Check that your system is running normally without the previous symptoms
Additional GridinSoft Features for Enhanced Protection
Real-time Protection: Enable ongoing monitoring to prevent future infections from script-based malware and other threats.
Browser Reset: Use the built-in browser reset feature to clean any browser modifications made by the malware, restoring your homepage, search engine, and removing malicious extensions.
System Optimization: After malware removal, GridinSoft can help optimize your system performance and fix issues caused by the infection.
What Makes GridinSoft Effective Against Script Malware
Unlike basic antivirus programs, GridinSoft Anti-Malware uses advanced behavioral detection specifically designed for script-based threats:
- Script analysis engine – Examines JavaScript, VBScript, and PowerShell files for malicious patterns
- Registry monitoring – Detects unauthorized changes made by malicious scripts
- Task scheduler scanning – Finds hidden scheduled tasks created by malware
- Browser hijacking detection – Identifies and removes browser modifications
- Memory scanning – Catches script-based threats running in system memory
Free Trial and Full Version Benefits
GridinSoft Anti-Malware offers a free trial that allows you to scan your system and see detected threats. For complete removal and ongoing protection, the full version provides:
- Unlimited malware removal
- Real-time protection against new threats
- Automatic updates with latest threat definitions
- Priority customer support
- Advanced system optimization tools
Handling False Positives
If you’ve determined your detection is a false positive (such as with .NET 9 AOT applications, game emulators, or legitimate development tools), here’s how to handle it safely:
How to Verify It’s a False Positive
- Check the file context – Is it in a development folder, game directory, or software you just installed?
- Verify the source – Did you download it from the official website or trusted developer?
- Upload to VirusTotal – Check if other antivirus engines detect it (don’t upload confidential files)
- Look for symptoms – Real malware typically causes browser redirects, pop-ups, or system slowdowns
For Regular Users
Add Windows Defender Exclusions:
- Open Windows Security (Windows Defender)
- Go to Virus & threat protection
- Click Manage settings under Virus & threat protection settings
- Scroll down to Exclusions and click “Add or remove exclusions”
- Click “Add an exclusion” and choose:
- File – for specific files being falsely detected
- Folder – for entire directories (like development folders)
- File type – for specific extensions (like .exe from certain software)
- Navigate to and select the file or folder causing false positives
Report the False Positive:
- Go to Microsoft’s false positive submission form
- Submit the file for analysis to help improve future detection accuracy
- Include details about the software and why you believe it’s legitimate
For Developers and Power Users
If you’re developing software or frequently encounter false positives:
- Code signing – Sign your applications with a valid certificate to reduce false positives
- Alternative compression – Use 7z or RAR instead of ZIP if compression triggers detections
- User documentation – Include instructions for users on handling false positives
- Antivirus testing – Test your software with multiple antivirus engines before release
Common False Positive Scenarios
- .NET 9 AOT applications – Especially when compressed in ZIP files
- Game emulators – Xbox 360 emulator (Xenia), PlayStation emulators
- Development tools – B4X development environment, certain IDEs
- Android APK files – Legitimate apps downloaded for sideloading
- Compressed archives – 7-Zip files containing executable programs
Prevention: Protecting Against Real Script-Based Malware
To prevent genuine Trojan:Script/Wacatac.B!ml infections and other script-based threats, follow these essential security practices:
Email and Download Safety
- Never open script attachments – Avoid .js, .vbs, .hta, .ps1, or .bat files from emails, even from known contacts
- Verify email sources – Call or text the sender to confirm they sent script files before opening
- Download from official sources only – Avoid third-party download sites and “free software” portals
- Check file extensions – Be suspicious of files with double extensions like “document.pdf.js”
Browser and System Security
- Keep browsers updated – Install security patches that close script execution vulnerabilities
- Enable script blocking – Use browser extensions like uBlock Origin or NoScript
- Disable JavaScript on untrusted sites – Only enable when necessary
- Use Protected View in Microsoft Office for external documents
- Disable macros in Office unless specifically needed for work
Windows Security Configuration
- Enable Windows Script Host restrictions – Configure Group Policy to limit script execution
- Use standard user accounts – Avoid running as administrator for daily tasks
- Enable Windows Defender – Keep real-time protection active
- Configure Windows Firewall – Block outbound connections from script interpreters
System Maintenance
- Regular system scans – Run full antivirus scans weekly
- Keep Windows updated – Install security patches promptly
- Monitor startup programs – Regularly check for unauthorized additions
- Backup important data – Maintain current backups in case of infection
Signs to Watch For
Be alert for these early warning signs of script-based malware:
- Unexpected browser redirects or homepage changes
- New browser extensions you didn’t install
- Slow system performance or high CPU usage
- Unusual network activity or data usage
- Pop-up ads appearing outside of browsers
- Changes to default search engines
If you notice any of these symptoms, run a full system scan immediately using the methods described in this guide.
Frequently Asked Questions
How dangerous is Trojan:Script/Wacatac.B!ml?
When it’s a real infection, Trojan:Script/Wacatac.B!ml can be dangerous as it often serves as an entry point for more serious malware. It can download additional threats, steal information, or provide remote access to attackers. However, approximately 40% of these detections are false positives, especially with development tools and legitimate software.
Why is my legitimate software being flagged as Trojan:Script/Wacatac.B!ml?
Microsoft Defender uses heuristic scanning that can mistakenly identify legitimate code patterns as malicious. This commonly happens with .NET 9 AOT applications in ZIP files, game emulators, development tools, and certain compressed archives. The detection algorithm sees similarities to known malicious scripts even when the code is perfectly safe.
Should I ignore this detection if I think it’s a false positive?
Never ignore security alerts automatically. First, evaluate the context: if the detection is in a software folder you recognize, from a trusted source, and you’re not experiencing other malware symptoms, it’s likely a false positive. You can then add an exclusion in Windows Defender. If you’re unsure, run additional scans with other tools or seek expert help.
What’s the difference between manual and automatic removal methods?
Manual removal involves manually locating and deleting malicious files, cleaning the registry, and removing startup entries. It’s time-consuming and requires technical knowledge. Automatic removal using tools like GridinSoft Anti-Malware is faster, safer, and more thorough—it can detect hidden components and safely remove threats without risking system damage.
How can I prevent future Trojan:Script/Wacatac.B!ml infections?
Avoid opening script files (.js, .vbs, .ps1) from emails or untrusted sources, keep Windows and browsers updated, use script-blocking browser extensions, disable macros in Office documents, and download software only from official sources. Regular system scans and maintaining current backups also help protect against infections.
Can this malware damage my files or steal personal information?
Yes, genuine Trojan:Script/Wacatac.B!ml infections can steal passwords, banking information, and personal data. They can also download ransomware or other malware that encrypts or deletes files. That’s why it’s important to remove the infection promptly using the methods described in this guide and then change passwords for important accounts.
Summary: Remove Trojan:Script/Wacatac.B!ml Successfully
Whether you’re dealing with a real Trojan:Script/Wacatac.B!ml infection or a false positive, this guide has provided you with the complete solution. The key is first determining whether your detection is legitimate by checking the file context, source, and looking for symptoms.
For real infections: Use the manual removal steps if you’re comfortable with technical procedures, or choose the automatic removal option with GridinSoft Anti-Malware for a faster, safer solution that ensures complete elimination of the threat.
For false positives: Add appropriate exclusions in Windows Defender and report the false positive to Microsoft to help improve future detection accuracy.
Remember that prevention is always better than cure. Follow the security practices outlined in this guide to protect yourself from future script-based malware infections. Keep your system updated, be cautious with email attachments and downloads, and maintain regular backups of important data.
If you’re still unsure about your detection or need additional help, don’t hesitate to use specialized anti-malware tools or seek professional assistance. Your computer’s security is worth the investment in proper protection.
Still Need Help with Trojan:Script/Wacatac.B!ml?
If you’re unsure whether your detection is real or need assistance with removal, download GridinSoft Anti-Malware for a comprehensive scan. The free trial will show you exactly what’s detected on your system, and our support team can help you determine the best course of action.




