Virus:Win32/Expiro is a detection of Microsoft Defender that refers to a malware with backdoor capabilities. It allows attackers to control the compromised system, spy on it, install other malware, manipulate systems, and create botnets.
This malware is distributed under the guise of legitimate software. Once the computer is infected, it can spread to other executable files on the system, complicating its removal. The specific behaviors and capabilities may vary depending on the variant. However, typical activities associated with this malware group are the delivery of other malicious software.
Virus:Win32/Expiro Overview
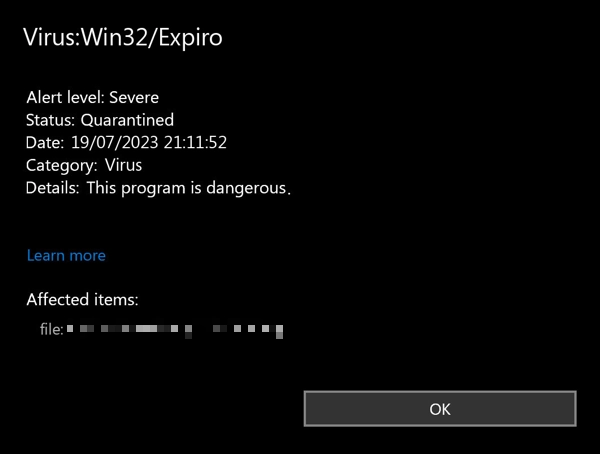
Virus:Win32/Expiro is a generic detection name used by Microsoft Defender Antivirus to identify malware belonging to the Expiro family. In our case, this family includes backdoors and RATs, which are similar in their principle of operation. The primary purpose of this class of malware is to provide remote access to the target system.
Expiro malware often enters a system through various means, but mainly through malicious advertising or within pirated software. Once installed, they operate stealthily, avoiding detection by antivirus programs thanks to the extensive usage of detection evasion tricks.
Significant number of Expiro malware samples leverage JDK to establish communication channels and hide their activities. Using this legitimate toolkit the malware is capable of avoiding the checks of a significant number of antivirus software. Though, the detailed analysis shows even more interesting details.
Detailed Analysis
Let’s take a closer look at one of the samples. The original sample masquerades as a Java update file, imitates accessing Java servers and using the Java library. After the execution though it morphs into a regular binary file. Once on the victim’s device, Virus:Win32/Expiro performs some basic check-ups. Most aim to determine whether the malware is in a sandbox or virtualized environment. To do this, it checks the following keys:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\AppV\Client\RunVirtual\
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl
The last key contains settings that may indicate whether the system is running within a virtual environment by controlling certain features or behaviors of Internet Explorer. After the successful check, the malware decrypts the rest of its file and launches.
Persistence & Networking Trickery
To gain a foothold in the system and permanence, the malware adds itself to the autoloader by adding appropriate keys to the registry:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
For providing reliable and hardly detectable connection to the C2, Expiro modifies several files related to Adobe software suite and Google Chrome update mechanisms. Also, malware performs a call to the Java Web Start, potentially to look benign. This is probably why Microsoft gave this a designation of a virus.
C:\Program Files (x86)\Google\Temp\GUM871F.tmp\GoogleCrashHandler.exe
C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrServicesUpdater.exe
"C:\Program Files (x86)\Java\jre1.8.0_121\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate
Command and Control Communications
Next, the malware establishes communication with the server. It performs DNS lookups, and posts data to the command server. Malware then requests the following files, which are probably the payload.
- 104.198.2.251/dybacct
- 34.128.82.12/horvwm
- 34.128.82.12/jeeifmfnna
- 34.174.61.199/kvlpjj
- 34.41.229.245/otmxwev
- 72.52.178.23/
- 72.52.178.23/qqhxribl
- 82.112.184.197
- cvgrf.biz/dybacct
- cvgrf.biz/flk
How To Remove Virus:Win32/Expiro?
To remove Virus:Win32/Expiro, I recommend GridinSoft Anti-Malware. It is an advanced solution that finds and neutralizes malware and provides proactive protection. It also has an Internet Security feature that blocks potentially dangerous pages, thus minimizing the risk of downloading something malicious.