Authorities have seized the LabHost phishing service, accused of stealing personal information from victims worldwide. This service specialized in creating fake websites to harvest user data illegally. However, law enforcement agencies have taken down in a series of coordinated raids in several countries. LabHost reportedly accumulated data on nearly half a million credit cards and secured over a million passwords.
Police Operation Halts LabHost Phishing Service
In a sweeping international law enforcement operation, authorities have dismantled a notorious cybercrime syndicate. They arrested 37 individuals linked to the LabHost phishing service. So, between April 14 and 17, a coordinated effort led by Europol resulted in the arrest of 32 individuals. This included four individuals in the U.K. who were responsible for developing and running a service. Additionally, 70 addresses were searched worldwide as part of this operation.
This global initiative, codenamed “Nebulae,” targeted a network accused of pilfering sensitive personal information from countless victims worldwide. Thus, the Australian Joint Policing Cybercrime Coordination Centre (JPC3) has successfully taken down 207 servers that hosted phishing websites created through the LabHost service. The Metropolitan Police in the U.K. has also announced the arrest of four individuals involved in running the service’s website, along with the original developer of the platform.
What Is LabHost?
LabHost (lab-host[.]ru) is a service recognized as one of the most expansive Phishing-as-a-Service (PhaaS) operations. It specializes in crafting deceptive websites that mimic reputable banks and institutions to harvest user data illegally. Europol, spearheading the effort, detailed that LabHost offered its illicit services through two distinct packages—a suite targeting brands primarily in the U.S. and Canada and a more global suite excluding these regions.
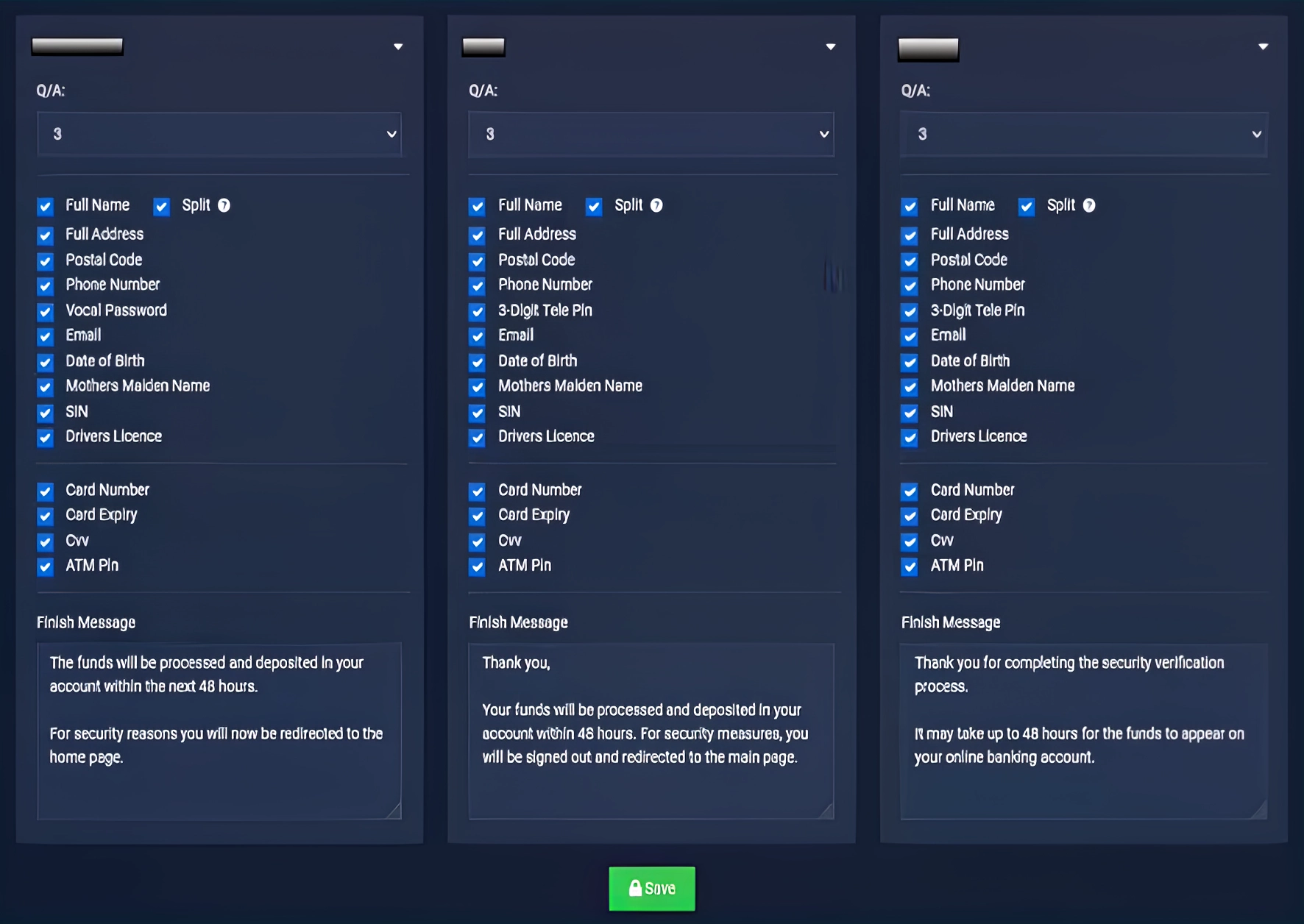
Subscription rates ranged from $179 to $300 per month, attracting many cybercriminals seeking to exploit unwary internet users. LabHost provided phishing kits for various services, including Spotify, postal and toll services, and even insurance providers. The platform simplified the phishing operation by managing the backend infrastructure, thus enabling criminals to launch attacks with minimal technical effort.
Financial Gains and Global Impact
The effectiveness of LabHost’s infrastructure was alarmingly evident in the number of its victims. According to Trend Micro, over 164,000 individuals in Australia and the U.K. had been duped into submitting their details on these fraudulent pages. The phishing sites were sophisticated enough to fool users into entering sensitive information. Among others were credit card numbers, passwords, and even two-factor authentication codes.
The U.K. Metropolitan Police highlighted the financial scale of this criminal enterprise, estimating that LabHost had amassed around £1 million from its illegal activities. The service reportedly accumulated data on nearly half a million credit cards and secured over a million passwords.





