ARP Spoofing Attacks: The Silent Network Threat You Need to Know in 2025
ARP spoofing attacks (also known as ARP cache poisoning) remain one of…
Phishing vs Spoofing: Definition & Differences
What is a Phishing Attack? Phishing is a cyber-attack method that introduces…
Sniffing and Spoofing: Difference, Meaning
Users are increasingly encountering malicious links that, when clicked, unleash a different…
Black Hat SEO: Is Someone Phishing With Your Site Domain?
Search engine optimization (SEO) is a process of optimization and upgrading of…
Twilio Falls Victim To Phishing Attack
Twilio, a tech giant from San Francisco, became a victim of a…
11 Types of Spoofing Attacks
Spoofing is a kind of cybercrime in which attackers impersonate a trusted…
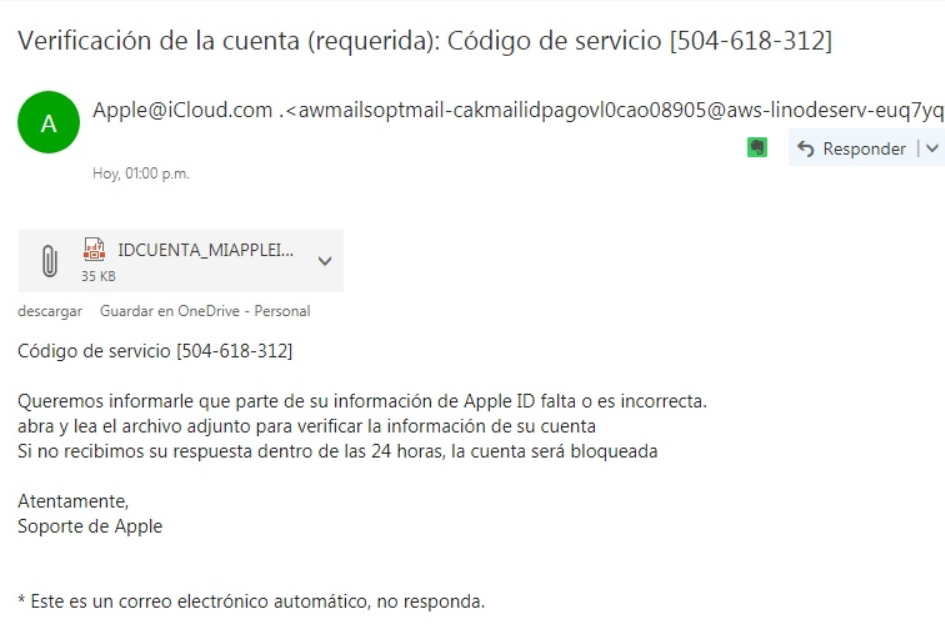
Extension spoofing strikes Spanish-speaking countries
An old-good form of malware disguisment sparked recently in several Spanish-speaking countries…
DNS Spoofing: Key Facts, Meaning
What is DNS Spoofing? DNS (Domain name server) spoofing or DNS cache…
IP Spoofing Attack: Explanation & Protection
Among other types of attack, IP spoofing stands out for its simple…