Among other types of attack, IP spoofing stands out for its simple yet graceful design. This is, exactly, what goes for its long life and widespread application throughout decades. Let’s see how this attack works, and where the hackers can use it.
What is IP Spoofing?
IP spoofing is a type of cyberattack where the attacker forces the server to think that a package sender is a completely different system. Hackers mostly use this approach to launch DDoS attacks or, in rare cases, to intercept the connection. The latter is a basic part of the attack called Man-in-the-Middle. As a fact, IP spoofing was among the first methods to launch a DDoS attack.
Depending on the network protocol targeted by the attack vector, there are several types of spoofing: IP-, ARP-, DNS-, MAC-, and GPS-spoofing. There, however, I will review only IP spoofing
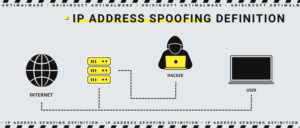
What is IP Address Spoofing?
Keyword: Internet Protocol (IP) is a network protocol that does not establish a connection (working on layer 3 (network) of the OSI model), meaning no transaction status information is used to route packets over the web. In addition, there is no method to ensure the correct delivery of the package to the destination.
IP spoofing is the renumbering IP addresses in packets sent to the attacking server. The sending packet specifies the address that the recipient trusts. As a result, the victim receives the data that the hacker needs. You can completely exclude the spoofing by comparing the sender’s MAC and IP addresses. However, this type of spoofing can be helpful. For example, hundreds of virtual users with false IP addresses were created to test resource performance.
How Does This Attack Work?
Any attack works according to some scheme, thanks to which it develops its identical structure of actions. For example, below we have a rule present in all Internet protocols:
All data that is transmitted between computer networks is divided into packets. Each package have its IP headers, which include the source IP address and the destination IP address.
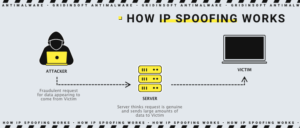
What’s a cybercriminal doing with all this? It starts to change the IP addresses it compiles so that the recipient will think the sending is coming from a reliable source. These operations take place on a network level, so there are no signs on the surface. The spoofing process falsifies the sender’s address to convince the remote system that it receives the address from an objective source.
Types of IP spoofing
To understand how to prevent your data from IP spoofing attacks, you need to know and understand the types of these attacks, how they manifest or not, and their purpose. There are several variants of attacks that successfully use this trick.
-
Masking Botnet devices
Sometimes IP spoofing can penetrate the computer by using botnets. Botnets are a network of hacked computers that the attacker controls remotely. Unfortunately, tracking the bot is not as easy as you would like. So instead, disguise it under a fake IP address. -
Distributed Denial of Service (DDoS) attacks
IP spoofing is used in one of the most complex attacks for protection – «denial in maintenance» or DDoS. Because hackers deal only with bandwidth and resource consumption, they do not need to worry about the correct completion of transactions. Instead, they want to flood the victim with as many packets as possible in a short period. It is almost impossible to quickly block it when involved in an attack by several hacked “hosts” accepting all sent fake traffic.
READ ALSODDoS:Win32/Nitol!rfn (Nitol DDoS) – Virus Removal Guide.
-
Man in the middle Attacks
They are also known as the attack type «man in the middle» (MITM). In these attacks, the attacker intercepts communication between two users. The cybercriminal then manages the traffic and can eliminate or modify the information sent by one of the original IP addresses without knowing the original sender or the recipient. Thus, the attacker can deceive the victim by revealing confidential information by «substitution» of the identity of the original sender, whom the recipient supposedly trusts.
How to Detect IP spoofing
It is almost impossible to notice a submenu IP address because the submenu occurs on a network level and connections often look like legitimate requests. So there are no external signs. But not all are unsuccessful! Network monitoring tools make it possible to do traffic analysis at endpoints. It would also be appropriate for such attacks to do packet filtering; what would it do? These package systems located in the firewall and routers find a discrepancy between the required IP address and the IP addresses of the packets specified in the ACL (access control list), so it is possible to find an attacker on the network.
Package filters control:
- Physical interface from where the package came;
- IP and (IP – source addresses);
- IP and (IP – destination addresses);
- Transport level type (TCP, UDP, ICMP);
- Transport ports of origin and destination.
Let’s look at two types of packet filtering:
- Egress filtering – reviews outgoing packets for source addresses that do not match organizations’ IP addresses in the network. This type of filtering prevents the launch of IP address substitution attacks by insiders.
- Ingress filtering. This type of filtering monitors whether the outgoing IP address of the header corresponds to the allowed IP address and rejects all non-conforming packets.
How to Protect Against IP Address Spoofing Attack?
The main measures that minimize the possibility of such attacks include:
- Router filtering;
- Encryption and authentication (will reduce the likelihood of spoofing);
- Robust verification methods;
- Network monitoring;
- Using firewall (protects your network, filters traffic with fake IP addresses, blocks access of unauthorized strangers);
If you follow the precautions mentioned above and understand why spoofing attacks are used, you can protect your network from malicious hacking and data theft.

❗❗ You know that protecting against spoofing attacks and other online threats is an important mandatory step for users. Protect yourself from spoofing attacks. Take back control of your privacy with Gridinsoft Anti-Malware, the best antivirus software available. Definitely the best scanner, detector and removal of spoofing attacks. There are enough reasons to choose Gridinsoft Anti-Malware as the solution to your PC problems right now.