Behavior:Win32/Fynloski.gen!A is a heuristic detection of Microsoft Defender that flags activities of Fynloski malware. This malicious program allows attackers to control the infected system and install other malware remotely. Such malware usually spreads through email attachments and software from low-trust sources.
Behavior:Win32/Fynloski.gen!A Overview
Behavior:Win32/Fynloski.gen!A is a detection name used by Microsoft Defender to identify a specific type of malicious behavior associated with the Fynloski malware family. This malware group is not a stand-alone family, but rather a group of malicious programs that share code similarities. It’s a heuristic detection, meaning it detects Fynloski-like malware based on its actions rather than a specific signature.
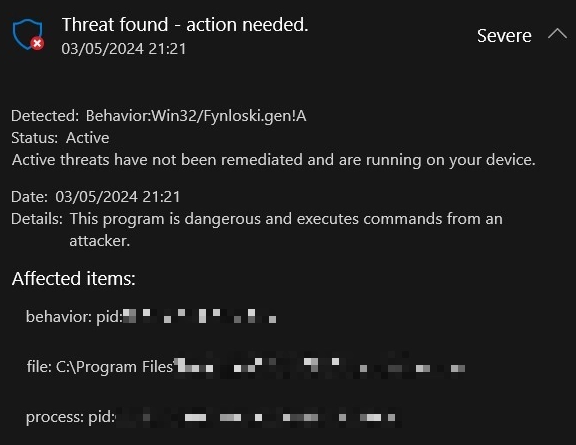
Fynloski malware typically allows attackers to control the infected system remotely, a normal function for a backdoor. It can steal sensitive information such as passwords, personal data, and banking details, capture screenshots, record keystrokes, monitor user activities – overall, act as spyware. It can also download and install other malicious software onto the infected system. Win32/Fynloski spreads through email attachments, downloads from compromised websites, and software from untrusted sources.
Technical Analysis
Let’s look at how this works using a specific example. After infiltrating the system, it performs checks typical of most malware to detect the presence of a virtual environment or debugger. The malware checks the following locations:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager\SafeProcessSearchMode
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\GRE_Initialize
HKEY_LOCAL_MACHINE\Software\Microsoft\PolicyManager\default\System\ConfigureTelemetryOptInSettingsUx
These files and keys can contain information about configurations used for security and telemetry collection in virtual environments. The malware quits further execution shall it find any traces of the virtualization here.
After finishing the initial checks, Fynloski collects system information. This information does not include confidential data; its purpose is to create a digital fingerprint of the system for future identification. The malware collects information from the following locations:
C:\Windows\AppCompat\Programs\Amcache.hve
C:\Windows\System32\drivers
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\DataCollection
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Windows Error Reporting
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Lsa\FipsAlgorithmPolicy
The first file contains information about recently launched programs and installed software, which can provide insight into the system configuration and installed applications. The subsequent registry keys contain information about the user and OS settings.
To avoid detection, the reviewed sample uses standard encoding algorithms. This, however, differs from one sample to another: some of the more sophisticated samples may use deep sample encryption that is lifted only in the runtime. Also, considering that the original detection comes from the heuristic engine, there are high chances that the samples use unique packing or rebuilding, which additionally enhances detection evasion.
Execution
After performing all checks and gathering the necessary information, the malware establishes persistence in the system. It executes the following shell command:
REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "Support GFX" /t REG_SZ /d "%APPDATA%\Xpers\Gpers.exe" /f
This command adds an entry into the current user’s autoloader section to run a specific program when the user logs in.
Next, Fynloski connects to its Command and Control (C2) server to transmit information to the attackers and receive further commands. The following addresses are used for this purpose:
tcp://betclock.zapto.org:35000
UDP a83f:8110:0:0:4b8e:21:0:0:53
TCP 23.216.147.64:443
TCP 192.229.211.108:80
TCP 20.99.185.48:443
How To Remove Behavior:Win32/Fynloski.gen!A
To remove Behavior:Win32/Fynloski.gen!A, I recommend using advanced anti-malware software. GridinSoft Anti-Malware is an excellent option as it can neutralize the threat even during the early attack stages. Download it, run a Full scan and remove all the threats that it has detected.