Password security remains a point of heavy discussions among the numerous other cybersecurity topics. It happens to see one’s saying following password security is a must, as well as people who say all this is pointless and malware will grab credentials anyways. But why is there such a desperate need for password security? And what is the safest way to store passwords? Let’s find the answer.
Password Security Dangers
Today, one user on average has about 100 accounts, including social media, banking, and personal accounts. Despite looking as something of a lesser value, they in total give a tremendous amount of information about the user. Moreover, possessing someone’s online account opens gates to impersonation attacks – a type of phishing that is considered one of the most effective.
Cybercriminals may use gazillion different tools to get their hands on user information. However, the majority of them bear on only a few mistakes and weaknesses of how people usually treat passwords. This, in combination with more proactive approaches, puts quite a lot of people in danger of password leaks and identity compromise. I’ve gathered the most common password security dangers:
| Weak or default passwords | Common examples include «123456», «password», «qwerty». Attackers often use lists of these common passwords in dictionary attacks, where they systematically try each word in a precompiled list. |
| Password reusage | Short passwords are vulnerable to brute-force attacks, where attackers try every possible combination of characters. For example, a 6-character password consisting of lowercase letters has 26^6 (308,915,776) combinations, which can be quickly cracked by modern computers. |
| Phishing attacks | Attackers create fake websites or emails that appear legitimate to trick users into entering their passwords. It’s the most popular method of compromise today. |
| Data breaches | Attackers use the exposed credentials to try logging into other sites, exploiting users’ tendency to reuse passwords. Even hashed passwords can be cracked if weak hashing algorithms were used or if the attackers have sufficient computing resources. |
| Brute Force Attacks | Usually, attackers use automated tools to try every possible password combination until they find the correct one. The effectiveness of brute force attacks depends on password complexity, rate limiting, and allowed attempt count. |
| Social engineering | Attackers exploit human psychology to trick users into revealing their passwords. |
| Keylogging and malware | Keyloggers can capturing keystrokes and sending them to the attacker. |
| Insufficient protection measures | Insufficient protection measures includes lack of multi-factor futhentication, poor password storage. |
| Password sharing | Sharing passwords can lead to unintended access and compromises. Risks include accidental sharing and security breaches. |
How to Store Passwords Securely?
There are two main methods for securely storing passwords today. The most reliable method is using a password manager. Compared to other methods, which I will discuss shortly, password managers have significant advantages. These programs allow you to securely store passwords in an encrypted form, generate complex passwords, and automatically fill them in on websites.
Another relatively safe method for storing passwords is the standard password-saving feature in browsers. Previously, this was not a very secure place to store passwords, as they were stored in plain text and could easily be stolen by attackers. However, today, all popular browsers store passwords in an encrypted form, adding an additional layer of security. Nonetheless, despite these browsers taking extra precautions to ensure the safety of saved passwords, this method is still not the most secure option for storing your credentials.
Keeping in a Web Browser
All modern web browsers offer built-in password storage, which many people readily use. But is it really secure? In the past, web browsers stored passwords locally on the user’s disk in plain text. This meant that attackers could easily gain access by copying the password file or dumping its contents. Today, the situation has improved – most popular web browsers store passwords in encrypted form. These are the following:
- Google Chrome
- Microsoft Edge
- Mozilla Firefox
- Safari
These browsers use two-factor authentication, AES encryption (with Apple Safari using Keychain for storing passwords on Apple devices), and allow password synchronization through user accounts.
In addition to the browsers listed above, there are others such as Opera, Brave, and Vivaldi. While Opera uses encryption to store passwords, it doesn’t develop as actively as the aforementioned browsers. For other Chromium-based browsers, security depends on the specific browser and its update and protection policies.
Password Keeping Applications
Password managers are applications designed to create secure passwords and store them in an encrypted vault. They allow you to store hundreds of encrypted passwords. The only password you need to remember is the master password. I recommend using this method for storing passwords because it is perfectly suited for the task.
Since password storage is a big responsibility, I recommend using an open-source password manager. This ensures security because anyone can review the source code and verify its safety. One such option is Bitwarden, which is fully open-source, regularly undergoes security audits, and has never been involved in data breaches. In terms of functionality, Bitwarden offers features like multi-device support and offline access. Another excellent open-source password manager is KeePass, which is also free.
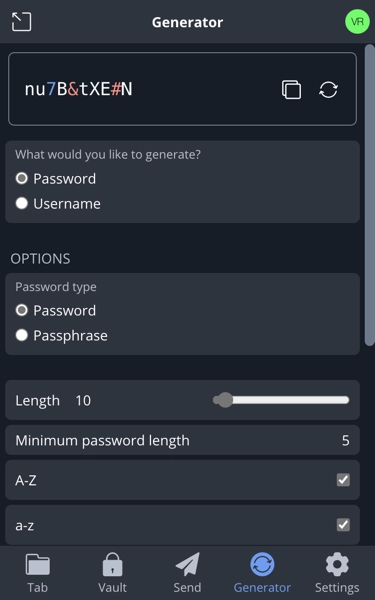
Another useful feature of these password managers is the built-in password generator. Whenever a user registers on a website, the password manager can generate a strong, unique password and save it immediately. Users can customize the password length and the characters used. This significantly reduces the chance of passwords being cracked through brute-force attacks.
However, not all password managers are secure. For instance, the once-popular password manager LastPass, which was considered the best at one time, has had multiple security issues. Despite not being an open-source manager, it has been hacked several times, with attackers managing to steal users’ saved passwords. Therefore, for security reasons, I do not recommend using LastPass.
Worst Ways to Store Passwords
We’ve discussed how to properly store passwords; now let’s look at how not to store them. The general rule is to never store your passwords in a visible place, especially if that place can be accessed by others. Here are some of the worst places to store passwords:
Sticky Notes
While it may seem convenient and easily accessible, this is also highly insecure, especially if the note is stuck to your computer monitor or desk. In such cases, passwords meant to protect your accounts are easily visible to anyone who enters your workspace.
Notebook or Journal
Like sticky notes, writing down passwords in a personal journal or notebook is not a great idea. Although it can be hidden, there is no guarantee that someone won’t come across it. If your notebook falls into the wrong hands, nothing stops that person from reading it and finding your passwords.
Screenshots in the phone gallery
Sometimes, when a user registers somewhere and needs to quickly save their data, they take a screenshot. This is undoubtedly the fastest and easiest way to save information. However, it is also an insecure method because sensitive information is stored in plain view. Anyone with access to the gallery can access the data.
Email or Messaging Apps
As messaging apps evolve, many users save important information in chats with themselves. This can be fine for documents, files, or memes, but it’s a bad idea for passwords and sensitive information. If the messenger uses encryption, reinstalling the app can result in losing this information. On the other hand, if the messenger doesn’t use end-to-end encryption, your password ends up on the messenger’s servers.
Text Files
This is a very simple and convenient way to store information. However, it’s not reliable because a text document is not encrypted, and anyone who opens it can see or copy your password.