You can say it has become much easier for various criminals to get to their victims and target them with different schemes. And all because of the ubiquitous internet these days.
You’ve probably heard the word ‘phishing‘. Today not only specialists from the cybersecurity field are actively talking about it but also ordinary users often are looking on the internet how to know if the email they received the other day could be a phishing attempt.
But before you jump right into research you should know exactly what type of online fraud you’ve encountered.
Because apart from phishing there are also smishing and vishing; what those are and how they different we’ll explain below.
What Is Smishing
Smishing is similar to the phishing technique of online fraud but instead of exploiting email fraud possibilities explores those of texts ( mainly via various message apps or SMS).
For example, user may receive a notification in WhatsApp messenger saying that they need to reschedule their package delivery.
To do this they need to follow the link given below. But what happens when the notification comes from fraudsters is that user can have some malware installed via that link.
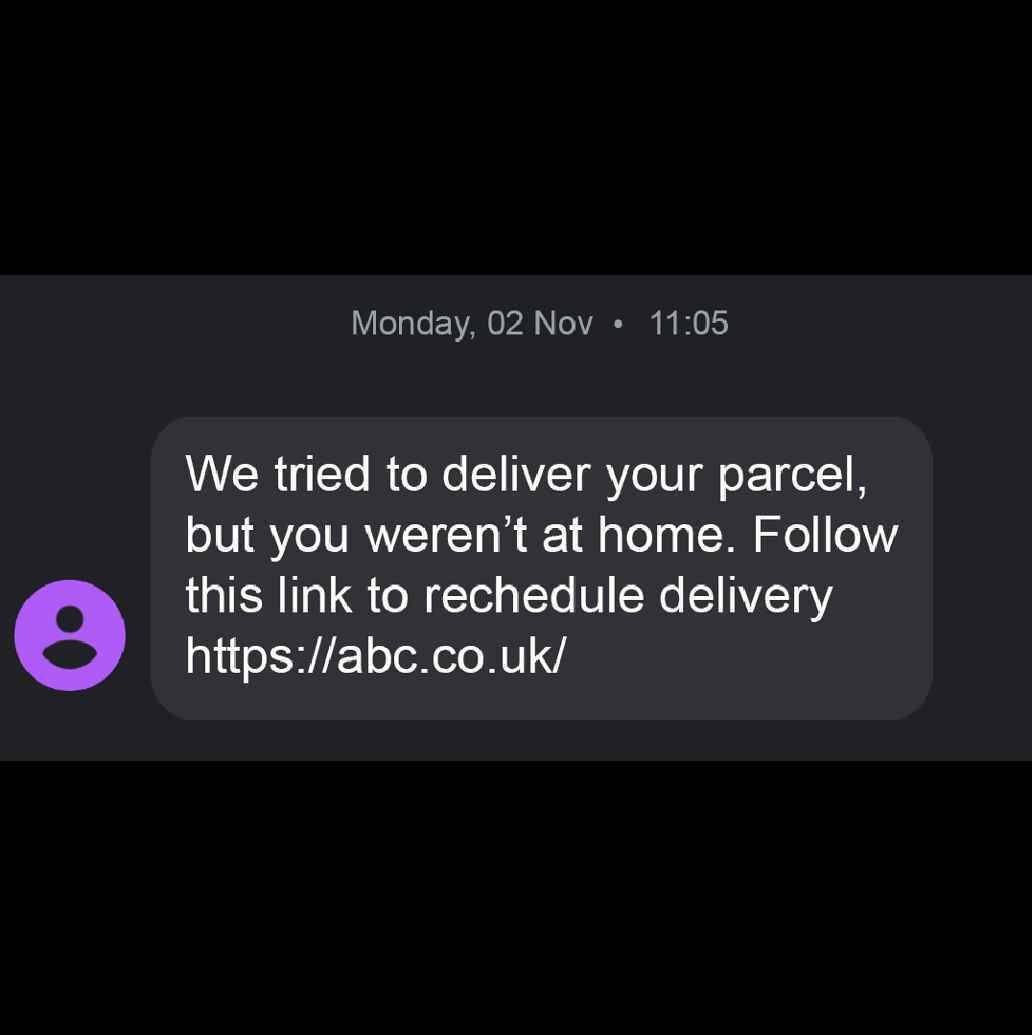
Another example is when thousands of people around United Kingdom received fraudulent text messages saying that the payment is needed to be made in order for a package to be delivered.
Those who received these fake text messages were instructed to click on an attached link that will lead them to a fraudulent website where criminals would collect victims’ personal or financial information.
What Is Vishing
Unlike phishing and smishing where fraudsters use text as a medium of malicious action in the case of vishing it is voice. Criminals may pretend to call you from your bank or another trusted company and try to obtain from you your passwords, addresses, login credentials, etc. They will try very persuasively to make targeted person answer their calls’ questions. In such a case victim can feel like they have no other option than to answer the questions.
Sometimes to reinforce the successful fraud criminals will accompany their calls with emails asking person urgently to call them by the given phone number. The third vishing tactic by which fraudsters also go to leave threatening in tone voicemails like warning that the recipient should call immediately explaining that in other case they risk being arrested, have their bank account blocked or some worse things may happen.
What’s The Difference Between Vishing And Smishing
Both terms mean specifically designed social engineering attack where criminals pretend to be someone to exploit a victim’s trust in such a way. It’s because more than 96% of social engineering attacks happen via emails the term ‘Phishing’ is exclusively used only when speaking about email based fraud. But, of course, social engineering attacks also include other mediums of social engineering attacks like social media phishing, vishing and smishing.
Regardless of how the fraudulent message is delivered it appears to come from trusted sender and may ask a recipient to do the next:
- To do some explicitly stated action. Criminals may ask victim to buy vouchers or transfer because of some important matter different sums of funds;
- Give a reply to the message. Fraudsters may want you to reply to their message with some sensitive or personal kind of information;
- Click on a link. You will be asked either to download a file or submit via attached link your personal information.
How To Identify Vishing Attack
Vishing attacks in some way resemble smishing but there is one exceptional way we can identify that it’s specifically is vishing. Vishing fraudsters can pretend to be the next persons to defraud you:
- Tech support. You may receive a phone call from a person saying they are IT support and thus they notify you over virus infection that happened to your computer. Usually you will be asked to buy a ‘needed’ software ( which can be some malware or spyware) or give attacker a remote control over your computer to fix the issue;
- Government institutions. These fraudulent phone calls usually is accompanied with legal threat action if a recipient won’t respond. You may be notified that you are owed tax refund or you need to pay some fine;
- Banks. These bank phone frauds try to give an effect of some alarm like something’s happening with your bank account; possibly someone took an unauthorized control over it and the bank support noticed it and now they offer you their ‘urgent help’;
- Charities or businesses. Fraudsters inform you via phone that you have won some exclusive prize, offer you ‘lucrative’ business investment or ask you to make donations to some charity.
How To Identify Smishing Attack
Smishing attacks are similar to phishing emails but in a case of a smishing fraudsters need to rely on much less text space to get their victim hooked.
But nevertheless smishing fraudsters have also developed their own unique approuches to how create authentic looking catch text message. The sighns for smishing you should be looking for are the next:
- An urgent request. You received a message with an urgent call for action to verify your personal information, for example, that should be completed via attached link or automated phone number;
- Text message from your bank or other institution you are familiar with. A victim of smishing may receive text message that appear to have been sent from companies or organizations victim may be familiar with;
- Congratulations on winning some contest. It can be message that congratulates you on having won in some contest wnd as a result notifiyng you that now the winner can claim the prize;
- Money help. Someone asking you for help via text message should definitely be a red flag for smishing. Most likely you don’t know who the person is and out of nowhere they ask you for money;
- Unexpected links and downloads. Sometimes messages with some downloads and links can be accompanied by text but on the whole the task is to make you click on it.