Austrian researcher Martin Herfurt has demonstrated a new way to steal a Tesla – for this attacker can abuse the function of adding a new NFC key, doing it unnoticed by the car owner, in just 130 seconds.
We love Tesla security news and have already covered that Information Security Specialist Showed How to Steal a Tesla Car and that Teen Gets Remote Access to 25 Tesla Cars.
The root of the problem is that Tesla released an update last year that made it easier to start cars after unlocking with NFC key cards. Previously, drivers who used a card key to unlock their cars had to place it on the center console to start driving.
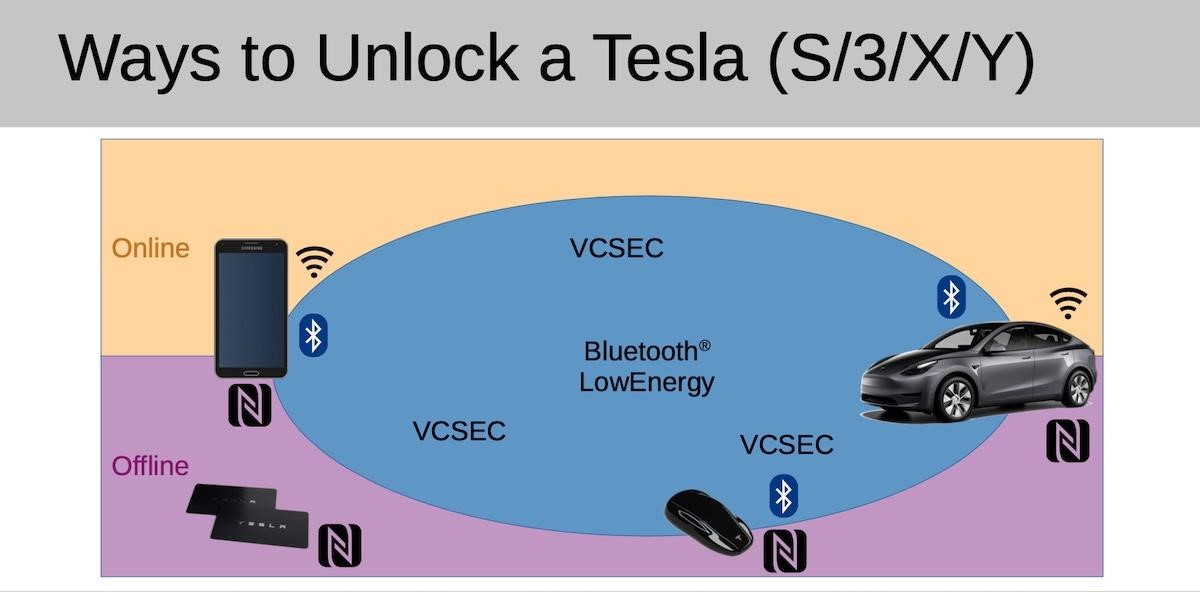
But since the update last August, Tesla owners have been able to drive their cars immediately after unlocking with a key card, which is one of three ways to unlock a car (the other two are a key fob and a mobile app).
Herfurt found that the new feature has a strange feature: it does not only allow the car to auto-start within 130 seconds of unlocking, it also puts it into a state that allows it to accept brand new keys, without the need for authentication and without any indication on the car’s display.
The official Tesla app doesn’t allow new keys to be registered unless it’s connected to the owner’s account, but Herfurt found the car willingly messaging with any other Bluetooth Low Energy (BLE) device in the vicinity. As a result, the expert created his own application called Teslakee, which uses VCSec, just like the official Tesla application.

Teslakee demonstrates how easy it is for thieves to add their own key to a car. You just need to be near the car during the 130-second window after unlocking the NFC key card. The thief can then use his key to unlock, start and shut down the car at any time. Neither the car’s display nor the real Tesla app will show any messages about what happened.
If the owner of the vehicle uses an app to unlock the car (and this is the most common Tesla unlock method), the attacker can force the victim to use the key card. To do this, it will suffice to just bring a jammer and block the BLE frequency necessary for the application to work.
Herfurth successfully tried his attack on the Tesla Models 3 and Y. He did not test this method on the new Model S and X, but suggests that they are also vulnerable, because they use the same technologies. A demonstration of the attack can be seen in the video below.
It should be noted that Herfurt created TeslaKee and conducted his research as part of Project Tempa, which “provides tools and information about the VCSEC protocol used by Tesla’s Bluetooth LE vehicle control accessories and app.” Herfurth is also a member of the Trifinite Group, a research and hacking team focused on BLE issues.
The researcher released data about the problem, because, according to him, Tesla is unlikely to fix it. Herfurth writes that he never received any response from the company about the vulnerabilities he discovered in 2019 and 2021, and doubts that anything will change now.
Since Tesla representatives do not comment on Herfurt’s conclusions, car owners, unfortunately, can do little to protect themselves. One way to protect against such attacks is to configure Pin2Drive so that the thief cannot start the car, although this does not prevent the attacker from getting into the car. You can also regularly check the list of keys that are allowed to be used to unlock and start the car.