An Italian university was hit by BlackCat this week. The hackers demand a $4.5 million ransom. BlackCat is a new, but very potent ransomware gang that carries several distinctive features that make it harder to detect and prevent.
About BlackCat ransomware
BlackCat ransomware is not a newbie on the ransomware scene, however, it is far from its old-timers – Conti or HiddenTear. Their first activity was in November 2021, and became known for using Rust programming language in the payload. That made their malware harder to detect, and can be run on different operating systems, including Windows, FreeBSD and Linux. The distributors they sell the ransomware to seem to be pretty professional, since there are no patterns in their actions and each attack is executed differently from the other. As it is usual for the majority of modern ransomware groups, double extortion is applied. ANOZR WAY reports about 12% of attacks accounted for that ransomware in 2022 – an enormous share for such a young group.
On Monday, June 13, 2022, Microsoft published a blog detailing the BlackCat grouping. The company reviewed successful attacks against Windows and Linux devices, as well as VMWare instances. Microsoft called BlackCat (a.k.a. ALPHV) a prime example of the “hacker gig economy” as it actively offers the ransomware-as-a-service model. The Rust programming language helps groupings avoid detection by conventional security tools and creates problems for security professionals by making it difficult to reverse engineer the payload or compare it with similar ransomware. Typically, hackers infiltrate systems using stolen victim credentials and remote desktop applications.
BlackCat attacked the Italian university
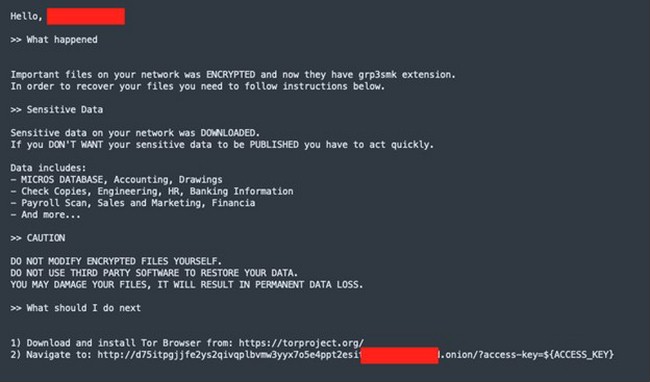
On June 11th, 2022 (Saturday), the University of Pisa reported about the ransomware attack. Typically, their files were encrypted, but there were no ransom notes for the case. The ransom note appeared several days later – on June 14. Cybercriminals asked for $4.5 million ransom to be paid until June 16, 2022. That is a pretty big sum for such a small period, still not the record one. A year ago, Kaseya received a $70 million ransom demand from REvil ransomware – and that did not end well for the ransomware group. It is still not clear how exactly hackers managed to get into the corporate network, as well as will the ransom be paid at all. Neither the gang nor university representatives did not give any comments on this situation.
The BlackCat group looks ridiculous at the current state of ransomware. Some analysts compare it with the LockBit ransomware group, which is either known for its superior software base. And in the absence of any restrictions for possible targets make it possible for the group to take over the market share of other actors. Microsoft also reported about DEV-0504 and DEV-0237, two ransomware gangs using the latest software from BlackCat. Payload modification is common among ransomware-as-a-service groups, the company says, as it generates a lot more money and makes ransomware more difficult to detect.