Information security researcher Ryan Pickren told how he received a large reward from Apple for hacking the camera and microphone in macOS. He also discovered vulnerabilities in Safari and macOS that could be used to hack into a user’s online accounts.
Back in 2020, Ryan Pickren received a $75,000 bug bounty from Apple because he found several vulnerabilities in Safari at once that could be used to access someone else’s camera and microphone (on devices running iOS and macOS). To exploit those bugs, it was necessary to trick the user into visiting a malicious site.
After receiving the award, the expert continued his research in this area and last year identified another chain of exploits related to iCloud Sharing and Safari 15, the use of which could have even more nasty consequences. As Pickren now reveals on his blog, the new attack combines four vulnerabilities, two of which have been given CVE IDs: CVE-2021-30861 and CVE-2021-30975. Two more bugs were recognized as “design” flaws, and not full-fledged vulnerabilities.
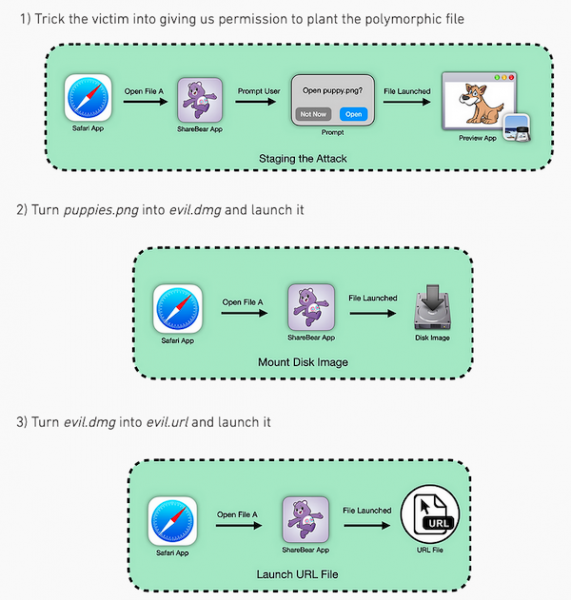
To exploit the new chain of bugs, it was necessary to lure the victim to a malicious site and force them to click on the “Open” button there. If the exploit was successful, the attacker gained access not only to the victim’s webcam and microphone, but also to all accounts on all sites that the victim had ever visited using Safari (including, for example, Gmail, iCloud, Facebook and PayPal).
The exploit chain included a UXSS vulnerability in Safari, abuse of iCloud’s default sharing feature (ShareBear), and bypassing Gatekeeper.
The fact is that when ShareBear is used to share files, the user needs to click on the “Open” button only once. Such a file can then be run remotely at any time without re-permissions.
The researcher writes that the problems were found in the summer of 2021, but Apple managed to finally eliminate them only recently, in January 2022. As a result, Pikren “earned” $100,500 from these bugs, receiving a large reward as part of the bug bounty program.
Let me remind you that recently MI also wrote that Zerodium offers up to $400,000 for exploits for Microsoft Outlook.