PaperCut, a software solution used for print management, appears to be vulnerable to remote code execution (RCE). Another security violation that popped out along with the former allows extracting user data from the profiles created in the program. The RCE vulnerability is already used in cyberattacks.
What is PaperCut?
PaperCut is a print management solution, which allows fine-tuning printer usage. It provides features such as print job tracking, print quota management, cost allocation, and secure printing, among others. The latter is exceptionally needed to prevent possible data leaks within the company. The software supports a wide range of different printers, scanners, and other devices of that purpose. It is a pretty popular solution – the latest data says about 100+ million users around the world. It can be very, very unfortunate if something that popular is unsafe.
Two Vulnerabilities Found in PaperCut Software
Recent research shows that PaperCut has two vulnerabilities – one is bad, and the other is horrifying. Let’s start with the most worrying one. CVE-2023-27350 allows remote code execution (RCE) without any authentication. RCE/ACE vulnerabilities are extremely dangerous, and seeing a 9+ CVSS rate for them is a common thing. This one received 9.8 points – equalling the recently-discovered MSMQ vulnerability.
Even more unpleasant is the fact that crooks already succeeded in using this vulnerability for cyberattacks. TrendMicro reported about hackers using the RCE vulnerability to execute a PowerShell script. The latter have downloaded a ransomware payload, circumnavigating passive security solutions present in the network. Threat actors did this trick using Windows Network Shell (netsh) utility. Another interesting feature of that attack is the use of temporary data hosting for payload delivery. In 60 minutes, the file is removed automatically from the hosting, leaving 0 evidence.
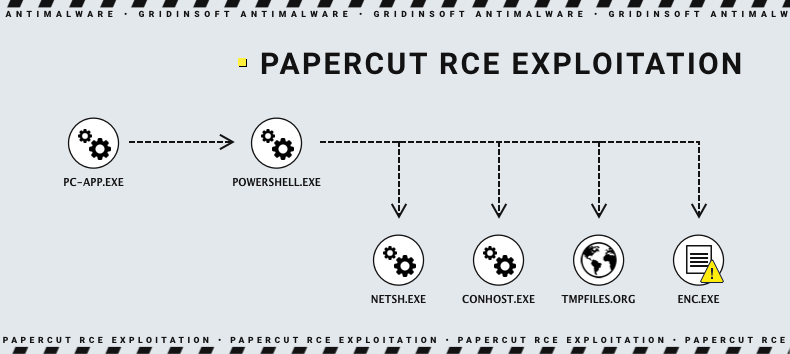
CVE-2023-27351 is less severe, yet still unpleasant. It also allows unauthorised access, but this time users’ information is under attack. Hackers can extract things like full names of the users, usernames, emails and even card numbers. All this information is available from user profiles created in PaperCut MF servers. It can potentially allow attackers to extract credentials to the PaperCut accounts.
List of PaperCut software vulnerable to mentioned exploits:
| CVE-2023-27350 | CVE-2023-27351 |
| Site servers | PaperCut MF/NG v.15.0 or later |
| Application servers | Application servers |
| PaperCut MF/NG v.8.0 or later |
How to Protect Against PaperCut Vulnerability?
Fortunately for all corporations that use the program, the developer already acknowledged that issue and released a security update. They recommend installing the latest updates available for vulnerable software as soon as possible. Such a rapid reaction is greatly appreciated, but companies generally tend to delay updates. This may be caused by numerous factors, some of which are hard to deal with. For that reason, preventive measures may be a more convenient option.
Most effective solution against exploitation is anti-malware software with a zero-trust policy. It supposes that no software is trusted, and each action must be checked. Modern EDR/XDR solutions generally opt for this exact policy, as it provides way higher protection rates against modern threats. Certainly, it has its downsides – but they are dim compared to the consequences of ransomware attack or APT activity.
Additional solution there is using active network protection. As I mentioned above, hackers used netsh to trick the firewall restrictions and reach the file hosting. More advanced network security solutions, like Network Detection and Response systems, are invulnerable to this. They will also make it much easier to analyse the cyberattacks (or their attempts), and implement urgent reactive measures.




