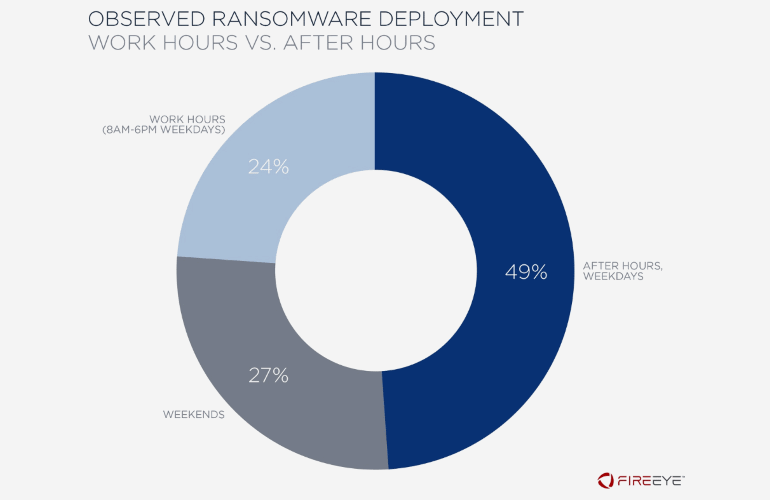
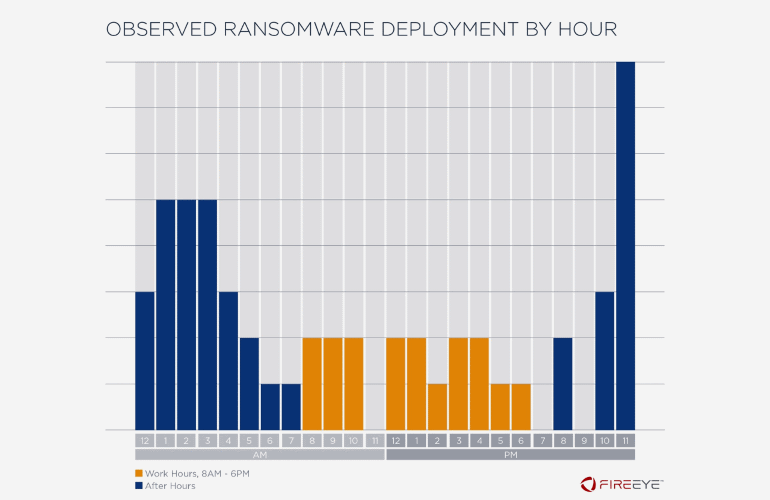
According to a report published by the American company FireEye, 76% of all ransomware attacks in the corporate sector occur in the off-hours: 49% of them are recorded at night on weekdays, and another 27% at weekends.
This data is based on dozens of ransomware incident investigations from 2017 to 2019.
“In 76% of incidents we reviewed, ransomware was executed in victim environments after hours, that is, on a weekend or before 8:00 a.m. or after 6:00 p.m. on a weekday, using the time zone and customary work week of the victim organization. This observation underscores that threat actors continue working even when most employees may not be”, — said FireEye specialists.
Such statistic is easily explainable, and in most companies there is simply no IT staff who would be on duty at night and on weekends. So, if there is no one to quickly respond to the attack, then attackers have good chances that the encryption process will have time to finish seamlessly on machines throughout the company’s network.
Researchers write that, as a rule, ransomware operators penetrate company networks in advance (as, for example, in the case of an attack on Epiq Global), then spend time on side movements to gain access to the maximum number of workstations, and only then manually install malware on all systems and start the encryption process.
“In other cases, attackers linked ransomware deployment to user actions. For example, in 2019 incidents at retail and professional services firms, attackers created an Active Directory Group Policy Object to trigger ransomware execution based on user log on and log off”, — explain FireEye specialists.
According to FireEye, the time from the initial compromise to the actual attack is on average three days.
As mentioned above, today ransomware attacks are started manually by attackers, but not automatically: most hackers carefully control their malware, and carefully choose when the most suitable time to attack and disable the network.
According to FireEye estimates, since 2017 the number of such people-driven ransomware attacks has increased by a huge 860%, that is, now such incidents affect all sectors and all geographical areas, and not just companies from North America.
The most popular vectors of such attacks, according to the report, were brute force attacks on open RDP ports aimed at phishing employees, pirated software, drive-by attacks, as well as using one infected host to spread the malware to others.
The good news is that particularly with post-compromise infections, there is often a window of time between the first malicious action and ransomware deployment. If network defenders can detect and remediate the initial compromise quickly, it is possible to avoid the significant damage and cost of a ransomware infection.




