Redline and Vidar Stealers Switch to Ransomware Delivery
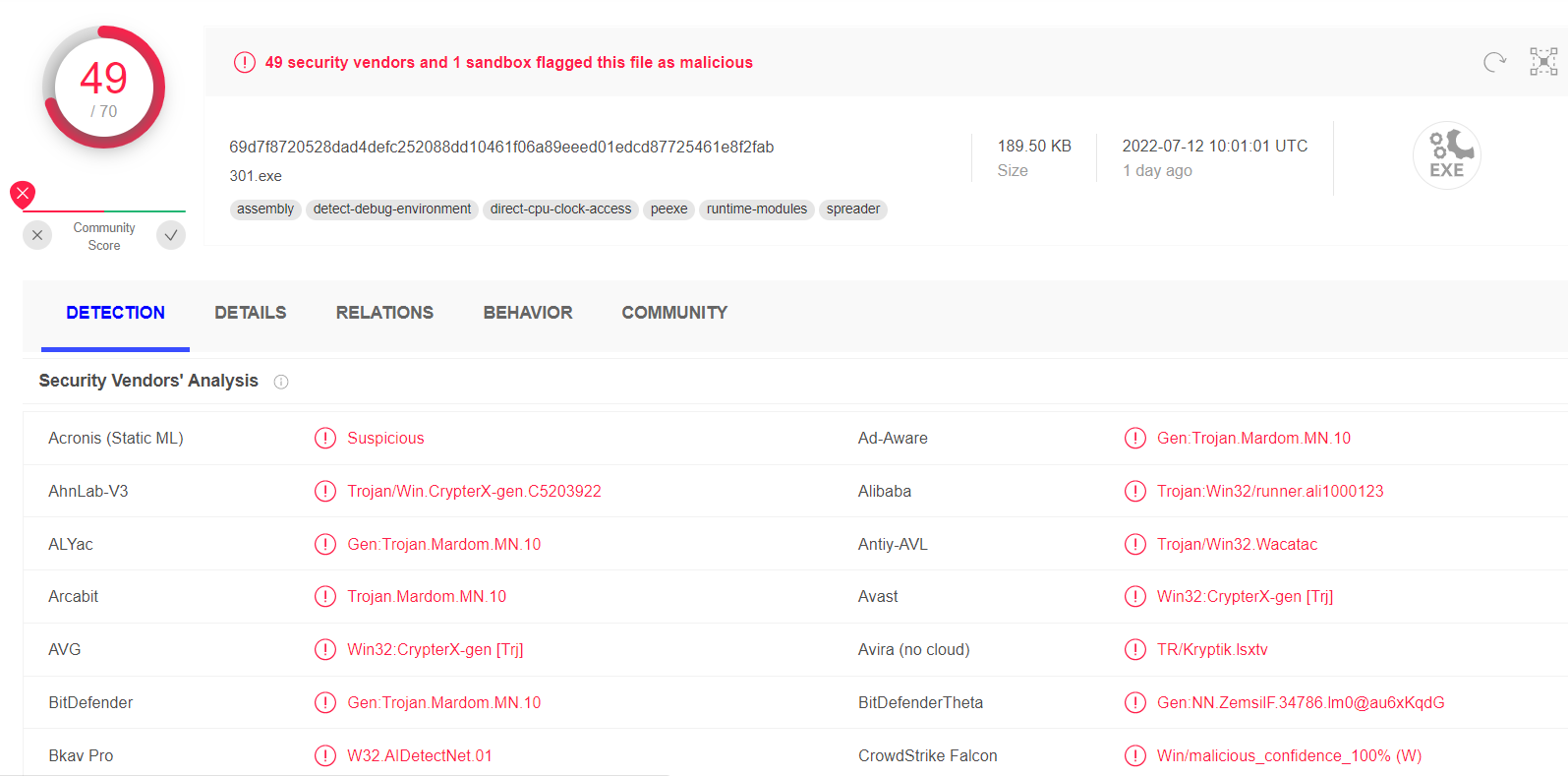
Cybercriminals who stand behind RedLine and Vidar stealers decided to diversify their…
Ransomware Attacks Decline in 2023 – Is It True?
According to ransomware attacks status statistics, the trend of incidents related to…
Huge Ransomware List by Gridinsoft Research – Part #2
We talked a lot about notorious ransomware examples in Part #1 of…
Huge Ransomware List by Gridinsoft Research – Part #1
Ransomware is rightfully considered one of the most dangerous types of malware.…
U2K Ransomware Strikes, Thousands Of Victims
U2K ransomware, probably the rising star on the ransomware arena, appeared on…
War in Ukraine triggered a Stream of amateurish ransomware
Russia has provoked hackers around the world to focus their attacks on…
20 Dangerous Types of Cybersecurity Threats
The cybersecurity threats in this year are more considerable than ever. Due…
TOP 9 Malware Attacks: Compilation 2022
The World Wide Web is not a hostile realm by itself, but…
Microsoft estimated that ransomware attacks take less than 45 minutes
Microsoft analysts have prepared a traditional Digital Defense report, in which they…
Ransomware attacks most often occur at night and on weekends
According to a report published by the American company FireEye, 76% of…