Cybercriminals who stand behind RedLine and Vidar stealers decided to diversify their activity. Now, crooks deploy ransomware, using the same spreading techniques as they used to deliver their spyware. Meanwhile, the process of ransomware enrollment is rather unusual and is full of advanced evasion techniques.
What are Redline and Vidar Stealers?
RedLine is an infostealer malware that appeared back in 2020, offered under Malware-as-a-service model. It is appreciated by cybercriminals for its wide functionality, that includes not only automated data gathering, but also manual commands for scanning the directories. And, typically for any stealers, it relies on stealthiness, that is additionally enhanced by a crypter software that comes as a side to the malware.
Vidar is similar but different. Aiming at a similar list of desktop apps, browsers and crypto wallets, it is closer to the definitive stealer. Once it finishes collecting information, all the gathered info is packed into the archive and sent to the command server. When this transfer is over, Vidar performs “melting” – or deletes itself, simply.
RedLine and Vidar Ransomware Delivery
In late summer 2023, the developers of RedLine and Vidar stealers started spreading ransomware under their own rule. The methods of gaining initial access remained the same – crooks send to victims an email with awaited or unpleasant information and an attachment. This attachment – you guessed it right, is a payload. The use of double extensions (pdf.htm, in one of the cases noticed by analysts) is quite typical for such attacks. As Microsoft disabled macros from running when they have come from the Web, the new, and quite old ways of spreading were put into use.
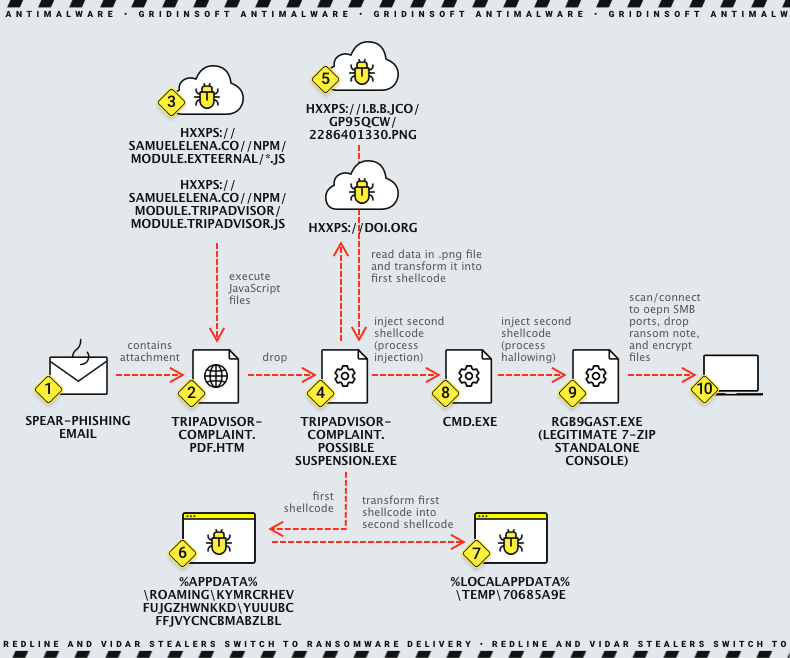
Once the victim runs the file, the chain of executions starts. First, the JScript applet connects to the intermediary server, downloads and executes the .exe file. This file, in turn, initiates the downloading of a PNG picture, which appears to be a bitmap image. Further, the image decodes into a shellcode, which transforms into yet another shellcode, saved to the Temp folder.
The second shellcode is getting launched in a Command Prompt instance spawned by the aforementioned .exe file. This way, the final payload comes into view – an infected console instance of 7-Zip utility. Upon execution, it launches the ransomware attack.
RedLine Uses EV Certificates to Conceal Itself
Another interesting, though not novel tactic used by hackers, is embedding EV certificates into malware. RedLine started using this practice in June 2023, starting with its stealers. Extended Validation (EV) code signing certs appeared as a shortcut for large companies for signing their software. Instead of thorough checks that prime the issue of a regular code certificate, this one needs only the request from a company. To get the right of EV requesting, the co should undergo a 16-stage checkup that verifies all edges of its identity. But, as it commonly happens, cybercriminals found a way to use it for their benefit.
It is not uncommon for certificates to leak, but the trust level is critical this time. Common certs require less authentication to issue, and consequently have less trust. Meanwhile, EV certificates rarely fall under suspicion, and frequent recalls may turn into a problem for the company. There is also no clear info on how EV certificates leaked. In the case of RedLine, such application turns exceptionally threatening due to the number of its samples that appear every day.
How to protect against ransomware?
Surely, modern ransomware amazes with the diversity of evasion techniques and damage done to the system. However, the spreading methods remain more or less the same for most families and samples. Email spam, questionable software downloaded from third-party sources – they have no reason to change a well-working scheme. And your best counteraction to this is your attention with spreading methods.
Do not interact with questionable emails. Hackers commonly use buzzwords that induce urgency of required actions. That is what drastically differs genuine messages from spam ones – companies never do that. Even though some of the messages are styled so they look legit and repeat what you’re waiting for, avoid haste and check the details of the message. Aside from the text style, the email address in spam messages is typically wrong from a normal one. Fortunately, there is no way to hide the sender’s address.
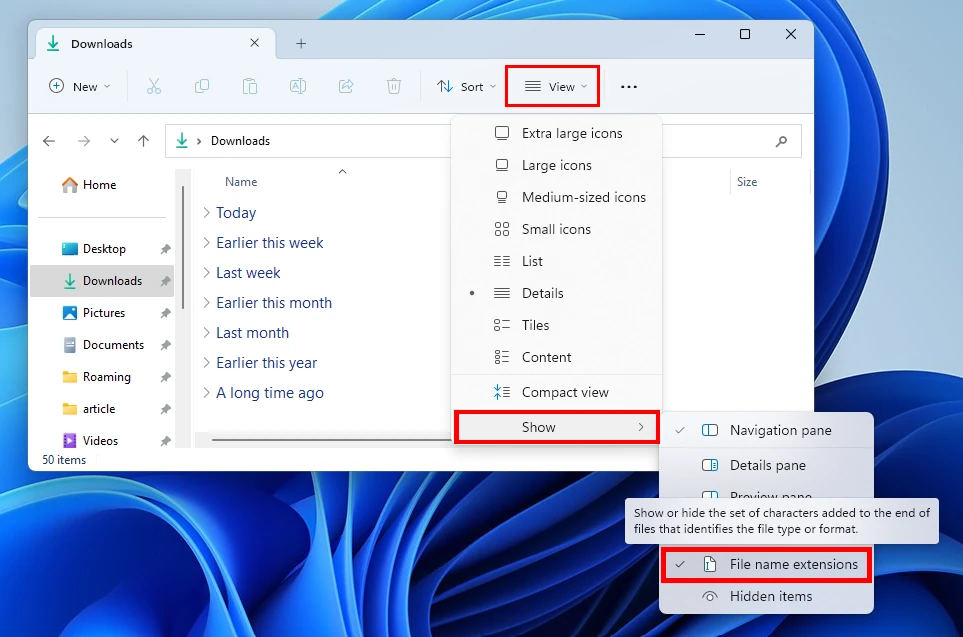
Be diligent to the files from the Internet you are going to run. The trick with double extensions (like .pdf.exe) exists over two decades, and hackers never shy away from using it. Since Windows does not show you the extensions of your files, it is extremely easy to get fooled in such a way. In your File Explorer settings, you can make it showing the extensions. Go to the View button on the upper panel, then click Show → File Name Extensions option in the drop-down list. This will make it much easier to detect such tricky files.
Use a reliable anti-malware software with advanced heuristic features. As you could have guessed, it is quite hard to detect the ransomware from RedLine developers statically. It disguises as deeply encoded files that are hard to identify in any way. Even the final payload masquerades as a legit console utility. In such a sophisticated case, only a heuristic detection method can help. GridinSoft Anti-Malware has multi-stage heuristic analysis with a neural scanning engine on hand. This can effectively detect such threats – try it out!