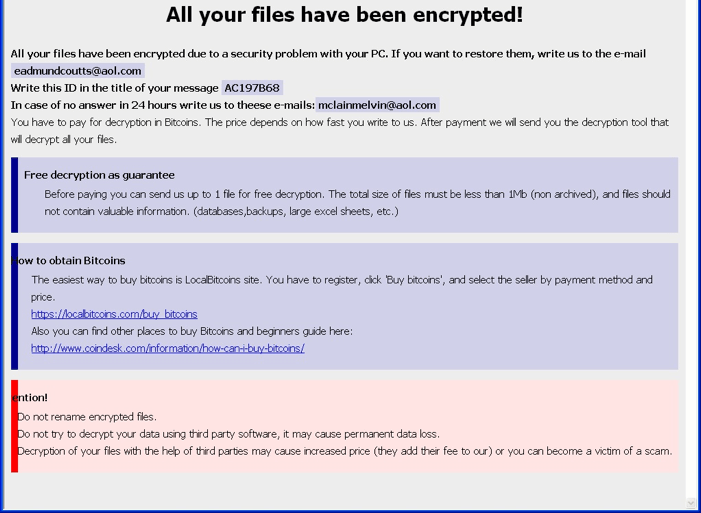
We talked a lot about notorious ransomware examples in Part #1 of this series. Still, it was not enough to reveal all noteworthy ransomware attacks. In Part #2, we will have a look at notorious attacks and ransomware families – several groups that use a single ransomware sample or its subspecies.
More Interesting Ransomware Attacks
Westrock ransomware attack
Active: January-February 2021
Damage: $269 million in idle losses
Ransom: $20 million for file recovery
Westrock, a US-based packaging producer that has leading positions in its market, was struck by a ransomware attack on January 25, 2021. The exact attack was uncovered on January 23, however, understanding what happened and giving the press release took two days. The consequences were solved by February 5, but the overall loss because of the two-week idle led to a sales loss of $189 million and operating losses of $80 million. While the corporate network was rendered defunct, the company failed to deliver 85 thousand tonnes of packaging.

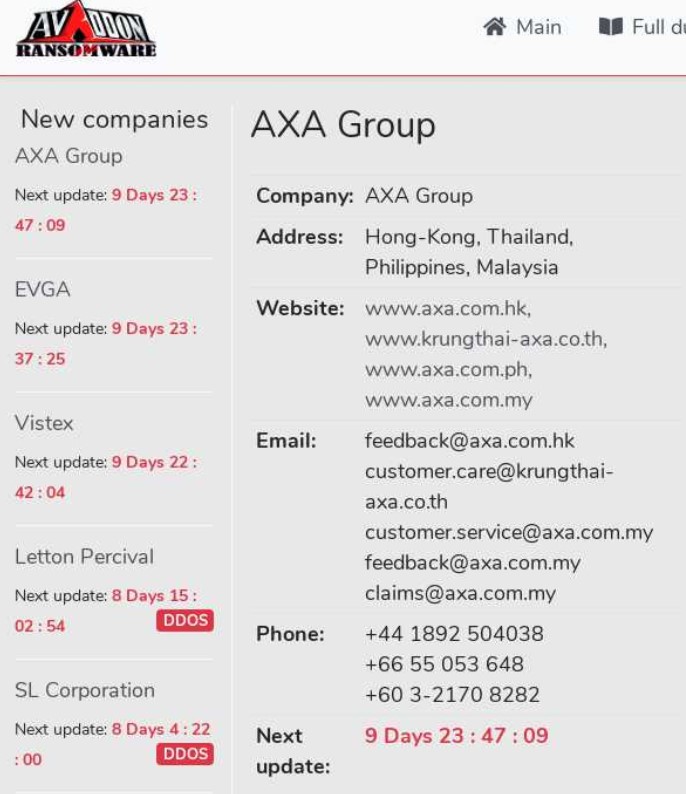
AXA ransomware attack
Active: May 2021
Damage: 3TB of confidential data leaked
Ransom: undisclosed
French insurance giant, actually, its branches in Malaysia, Hong Kong, Thailand and Philippines, were struck by Avaddon ransomware on May 4, 2021. Ironically, this happened days after the company’s note about the cancellation of any coverage of ransomware-related incidents. AXA seems to keep the information about the financial impact of that case secret. However, Avaddon’s leak site contained information about 3 terabytes of data they’ve got from a company.
Cloudstar ransomware attack
Active: mid-July 2021
Damage: Over a month of idle, money losses undisclosed
Ransom: undisclosed
Cloudstar, the provider of cloud virtual desktops, was hacked on July 19, 2022. First notices of these attacks appeared on July 18, and the following day the company’s services were not available. Soon after, the company issued a press release saying about a “highly-sophisticated ransomware attack”. They did not say about any certain numbers, like money loss or ransom demanded. Even after a month of a shutdown, Cloudstar was not fully operational – as August reports on this case claim.
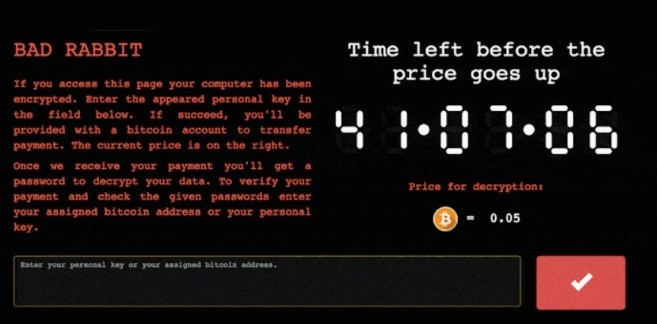
Bad Rabbit ransomware
Active: mid-2017 – late 2017
Damage: ~200 victims
Ransom: $280 (in Bitcoin)
Being an offspring of a noble family is always a risk to remain in the shadow of your parents. So happened to Bad Rabbit ransomware, which is based on Petya/NotPetya ransomware. First notice of this malware appeared shortly after the Petya ransomware attack we mentioned above. Possibly, the early reaction to that threat caused its low spreadness. Despite having a pretty unique spreading way – JS exploitation on the websites – it had only around 200 victims. Same as its predecessors, it was blocking access to the system, showing a ransom note instead. By the end of 2017, it completely ceased the activity.
REvil Ransomware group
Active: April 2019 – October, 2021
Damage: over 5000 victims over the globe
Ransom: ~$600,000 on average, peaking at $70 million
Along with Conti and LockBit, REvil (first known as Sodinokibi) is one of the most notorious ransomware gangs that was active during the last 3 years. Actually, its nominal shutdown in October 2021 only means disabling their Darknet infrastructure. Key actors, including Maksim Yakubets, their chief, remain free. The latter is also known for not shaming his cybercrime gains and riding different cars with a “BOP” (Russian for “thief”) number plate. Attacking companies, REvil mostly relies upon RDP vulnerabilities and network vulnerabilities. Most analysts tie codebase and threat actors to GandCrab ransomware – the group which ceased its activity in 2018. REvil group applies both double extortion tactics and RaaS operating methods. The latter makes its chiefs pretty hard to catch, despite their publicity.

HelloKitty ransomware
Active: January 2021 – now
Damage: uncalculated
Ransom: depending on the victims’ financials
It is a pretty rare case when malware receives its name for one of its elements. HelloKitty ransomware is called so for the mutex it creates in the attacked system. Still, that is not their main difference. Contrary to most cybercriminals who use well-known and trite ways like phishing or RDP breaches, they opt for a rather unpopular security violation. Their current option is Dell SonicWall firewall vulnerabilities, which allow them to break into the targeted network. Among the most famous victims of such an attack is Polish game developer CD Projekt Red. Another unusual detail about HelloKitty ransomware is adjusting their ransom sum depending on the company’s income. It may look like a good deed, but that also may be a sign that the gang analyses the leaked files in order to have detailed information about the company’s financials. Some gang members were captured in October 2021 in Ukraine, but that did not stop the gang activity.

MedusaLocker Ransomware group
Active: October 2019 – now
Damage: uncalculated
Ransom: $12,500 at average
MedusaLocker definitely refers to a Greek legend about Medusa, a female which could turn to stone anyone who meets its eyes. Such a dangerous association is complemented by a wide range of anti-detection and anti-removal methods that malware features in the infected system. Disabling security tools, modifying the registry, re-running the cryptor, scanning and encrypting connected directories – all this makes this malware even more dangerous. Spreading ways this group uses, however, cannot boast of originality – crooks use “classic” RDP breaches. Double extortion technique, pretty common for all groups, is used by MedusaLocker as well.
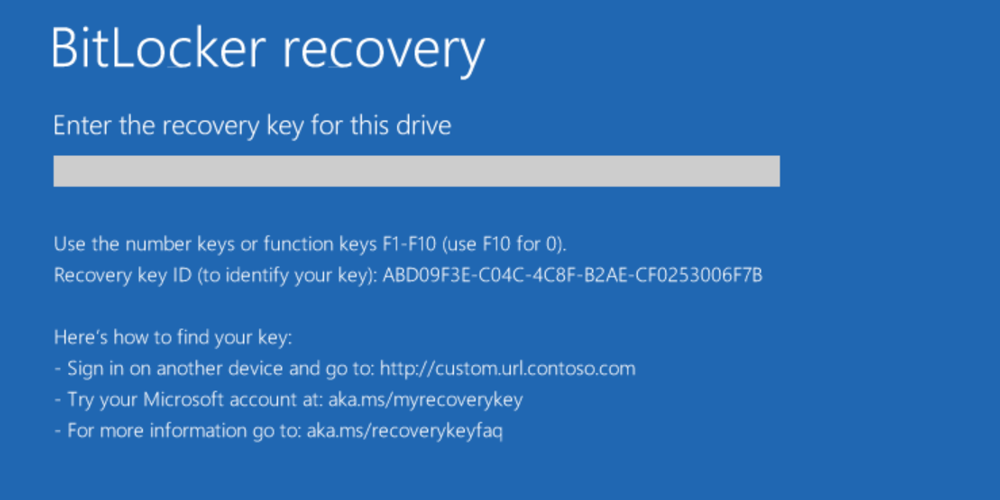
BitLocker Ransomware
Active: Late 2021 – now
Damage: uncalculated
Ransom: $300 – $100,000
The name of this ransomware may look familiar to users who apply some enhanced data security measures in Windows. Yes, it goes from BitLocker – the default Windows utility for disk encryption. Actually, this malware does not feature any ransomware code – it uses the BitLocker functionality to restrict users from accessing data. Such attacks are proven pretty hard to mirror, as almost no malicious code is used. Still, crooks who used this technique also managed to exploit MS Exchange vulnerabilities. This attack approach was used by different cybercrime groups, despite it was not a massive application.
BlackByte Ransomware gang
Active: July 2021 – now
Damage: ~700 companies hacked
Ransom: $200,000 – $6.5 million
BlackByte is yet another example of ransomware that tries to be the best at everything. Constant updates to both ransomware and auxiliary software made it really dangerous and prolific. In particular, this gang practices archiving the files from the attacked network before sending them to cloud storage. Another interesting thing is their switch to Golang from C#, which happened in early 2022. Still, similar to other gangs, they do not invent anything new when it comes to distribution. Typical ways for BlackByte are phishing emails and network security breaches.
Avaddon Ransomware gang
Active: February 2020 – June 11, 2021
Damage: 2934 companies hacked
Ransom: $40,000-$600,000
Only a few ransomware groups go offline because of their success. Most of the time, they’re forced to, by law enforcements or white hat hackers. Avaddon is an example of the former – they voluntarily shut down their operations after over a year of successful hacks. The biggest gem of their victims’ collection is the French insurance company AXA. The key way of spreading that this group used was email spam that contained a malicious archive. Further, they also adopted exploiting vulnerabilities in RDP and VPN connections. As a motivation for their victims to pay, they used to set a payment deadline of 10 days. Once a victim fails to pay, Avaddon operators publish the leaked data on their Darknet website.
Makop ransomware
Active: January 2020 – now
Damage: uncalculated
Ransom: $31,382 (haggling is possible)
Some ransomware developers, after acknowledging that their brainchild’s cipher is vulnerable, try to upgrade it and fix the issue. That is not the case with Makop ransomware – which uses multiple encryption techniques in a random order. Such an approach makes it nearly impossible to create a centralised solution that could possibly decipher the files. Makop, exactly, has a flaw in the way it generates the encryption keys, so there is a possibility to find a key with brute force. Could have been, actually. Another interesting detail is its ability to use several CPU threads to encrypt the files on each specific drive. Spreading ways, however, are pretty trivial – RDP vulnerabilities exploitation and email phishing became the alpha and omega of the vast majority of cyberattacks.
STOP/Djvu Ransomware family
Active: February 2018 – now
Damage: uncalculated
Ransom: $490-$980
Favourite, main threat, key threat actor upon the entire market – all these words are about STOP/Djvu ransomware. Despite having a kind of activity drop over the last 6 months, STOP ransomware did not give anyone the first place, retaining over 50% of all infections. It attacks mostly individuals and thus bears on automated spreading methods. Email spam, fake programs cracks, hacktools – they act as the most popular source for this malware. Currently, Djvu ransomware features over 600 variants – they differ by the extensions they add to the files during the encryption. This ransomware features a pretty unique anti-detection tactic: each new sample is repacked in a specific way, so it is not possible to detect it with signature-based mechanisms.
Matrix Ransomware group
Active: December 2016 – now
Damage: uncalculated
Ransom: $120,000 at average
Matrix is yet another old-timer, which has been running since late 2016. That’s an immensely long time for ransomware to run without any interruption, rebranding or restructuring. Group can boast of such a term only because of their flexibility in the rapid-changing environment. Through these 6 years, they’ve changed the spreading ways multiple times, and adjusted the exact ransomware as well. First, they managed to get into the system and expand their activity via Windows shortcuts vulnerabilities, RIG exploit kit and phishing. Currently, their option is pretty much classic – RDP vulnerabilities exploitation. The distinctive feature of this malware is its readme banners – scary and funny simultaneously.
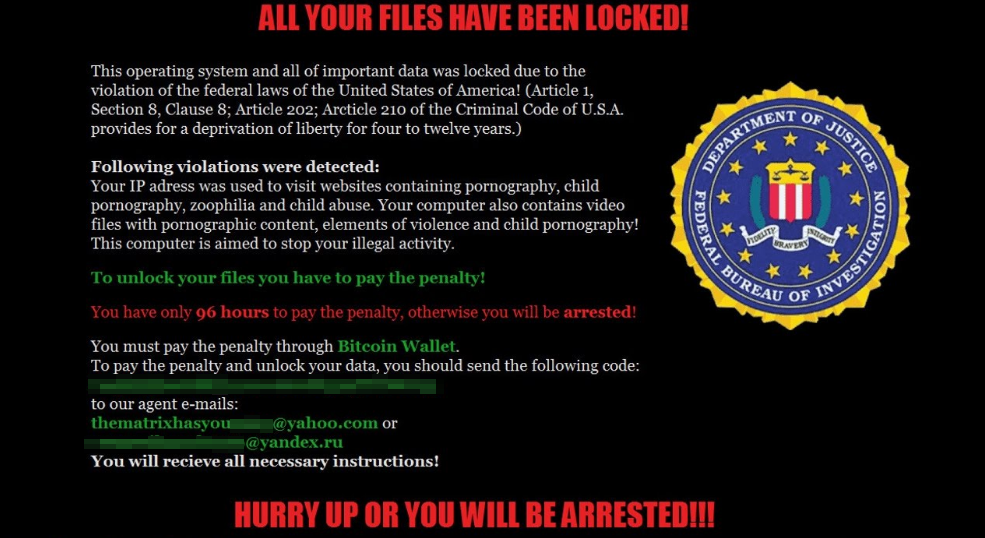
Snatch Ransomware group
Active: late 2018 – now
Damage: over 200 companies hacked
Ransom: $2,000 – $35,000
Using references to popular movies is not typical for ransomware. But that did not stop this gang from naming themselves after Guy Ritchie’s Snatch (2000). One of their members uses the nickname BulletToothTony, and their contact email is [email protected]. They’ve claimed about themselves openly on Darknet forums, along with searching for new affiliates there. Last time the gang became less public, preferring attacking companies to spare talks. Ransomware the Snatch group uses is written on Golang – not a very common feature that makes it harder to detect. Spreading generally relies upon RDP brute forcing, rarely – email phishing.
VoidCrypt Ransomware
Active: April 2020 – now
Damage: >800 companies attacked
Ransom: heavily depends on a victim
Some ransomware are dangerous because of their consistency and high-quality software. That’s not a story about VoidCrypt – which is dangerous because of its unpredictability. First of all, their malware is often modified, making it both hard to detect and impossible to predict its effects. Meanwhile, contacting them by email quite often gives no effect – you may receive no response at all. And in the exact message, you receive threats to increase the sum if you fail to contact them in time. Such a behaviour is embarrassing, especially because VoidCrypt generally attacks sole users. The codebase of this malware seems to see usage in numerous other ransomware samples, despite the fact that they don’t claim any relations.
Xorist Ransomware family
Active: December 2010 – now
Damage: uncalculated
Ransom: 0.05-2 BTC
This, apparently, is the oldest ransomware family that runs these days. Sure, modern variants share only a few details with the original, released in 2010. But the numerous offsprings it made during this 12-year history makes it quite hard to calculate the number of victims. The first versions of Xorist featured contacting the extorters not through email, but via SMS. It also uses a weaker cipher – AES-128 instead of the 256-bit version. Still, that didn’t bother this ransomware to be effective. The builder for this ransomware was leaked to the public, and it looks like a poorly-designed tool for skiddies. Apparently, that builder is a key for such a big number of offshoots.
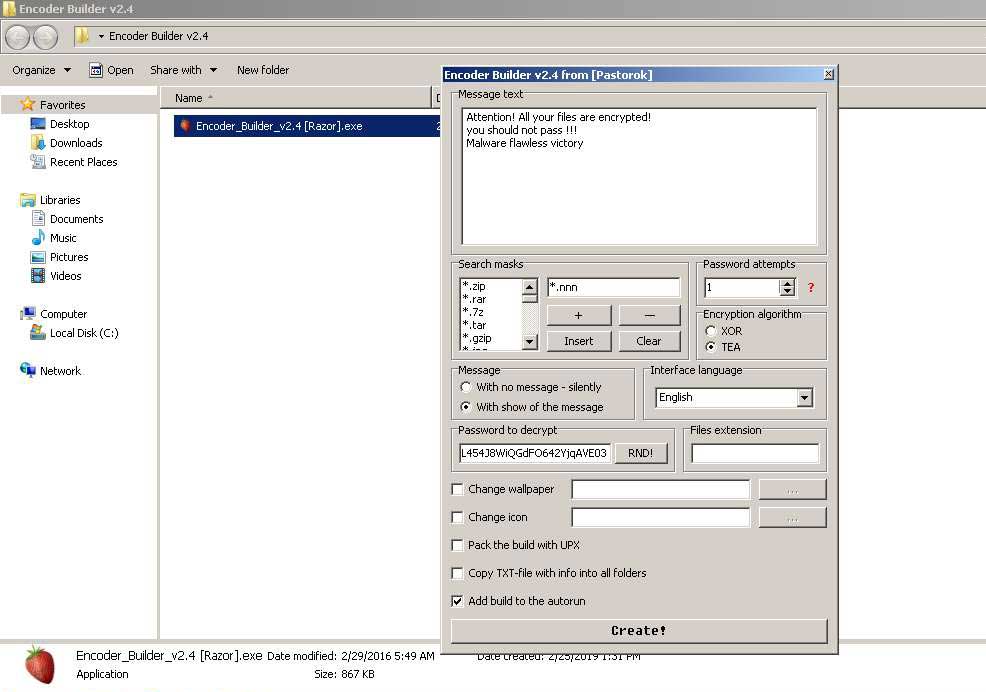
HiddenTear Ransomware family
Active: August 2015 – now
Damage: uncalculated
Ransom: depends on the variant
Maybe, the oddest thing you can imagine is open-source ransomware. And here it is – HiddenTear. This malware was initially designed for educational purposes, by Turkish researcher Utku Sen. However, once its source code appeared on GitHub, crooks began using it after slight adjustments. The original variant featured the encryption of only 1 folder and used a cipher with a flaw that made it possible to brute force the key. Fixing these issues is not a hard task, thus after certain “advancement”, it was as good as full-fledged ransomware. It is used by multiple cybercrime gangs around the globe.
Dharma Ransomware family
Active: February 2016
Damage: around 1000
Ransom: average $8,620, peaking at $15,000
The first name for this ransomware was CrySiS – and it was actual until early 2017. Only then did the Dharma name come into view, that’s why you can sometimes see that it is called Dharma/CrySiS. In pretty much the same shape, it exists nowadays, in 2022, attacking primarily companies. Dharma is known for hiring inexperienced hackers – they post a lot of messages on forums regarding their recruiting program. Still, besides dealing with amateurs, they mastered RDP breaching. Typically, they get through by phishing credentials for remote connection or a simple brute force.