
Makop Ransomware
Is Makop ransomware so really tough?
Just like a lot of other ransomware variants, Makop makes use of the AES-256 encryption algorithm. In some cases, this algo is complemented with RSA-2048, or even the RSA is used solitary. In summary, ransomware creates a very tough cipher, which is likely impossible to decrypt with a brute force, for example. If the key generation is created properly, AES encryption leaves no chance for the decryption, having 2^256 possible keys.
But why do other families have the decryption tool, using the same AES encryption? The majority of ones for which decryption tools are available use only a single type of encryption. Meanwhile, Makop doesn’t stay on a single encryption algorithm, constantly changing it on AES+RSA, or clear RSA, or RSA-4096, which is even harder to decrypt. Thus, the work of analysts is just useless - a new version of Makop can easily use another algorithm, and all efforts will have no effect.
Another thing which is not so widespread among ransomware is the file ciphering method. Files that are smaller than 1.5MB are encrypted completely. But when the file is bigger than this limit, malware takes 3 blocks from this file, with the size of 256 KB each, and ciphers them. Such behaviour compromises the attempts to use some large files: in the case of STOP/Djvu ransomware, for example, you can easily open the ciphered song/video - that ransomware encrypts only 150KB of each file, regardless of its size. Makop prevents such a hack, since even big files will have several parts encrypted.
Distribution and activities: are there some unusual elements, too?
The ways of spreading for Makop ransomware, however, are not so unusual and rapidly-changing. Just like almost all ransomware groups that attack companies, Makop uses the RDP vulnerabilities to penetrate the company’s network and inject the payload. Less often spreading is email spamming - also used by different ransomware groups. But as practise shows, in targeted attacks it is better to control the whole process of injection and encryption. Exactly, that’s why email spamming faded into the background and became rather a tool against individual users than a method to infect companies.
After being deployed, Makop ransomware encrypts the files in a pretty strange model: it does not divide the keys on online/offline. For all cases it uses a single key, and by analyzing the way this ransomware variant generates and manages this key it is closer to an offline one. Just like with offline keys, all things depend on the victim’s ID, not on a group of files ransomware have found. The same encryption key is applied to all files that are present in the infected system. It even has some sort of multi-threading: for each logical drive present in a system, Makop ransomware applies a single thread of the victim’s CPU. Since there are almost no single-thread CPUs left in use, this virus will barely struggle at this point.
Just like the majority of ransomware variants, Makop disables the Volume Shadow Copies and attempts to block all other recovery methods. The list of backup variants that can be disabled by that virus is unknown, but it surely can block not only VSC, but also the integrated backup method that is present on Windows. Another typical action is stopping everything that can somehow hinder the encryption - all antiviruses or any other things that can possibly block the ransomware activity will likely be disabled. Sometimes, those actions can even lead to system failures.
After the encryption, Makop ransomware keeps running in an idle mode, waiting for the new files to cipher them, too. That’s why it is better to remove the virus from your system before you start any actions. Moreover, it is also able to obstruct the installation of new anti-malware software. It is not clear how it does this, but you will still fail at the stage of malware removal. So to remove it successfully, you must boot the system into Safe Mode - fortunately, this virus is not able to block it.
Another element that is obligatory to talk about is data theft. The practise of double extortion - one ransom for files decryption and the second - to keep the internal files unpublished - is not a new thing. People already know about ransomware to have the habit to download personal data from the victim’s PC. And Makop meets these expectations - it steals the files of almost all widely-used formats. Pictures, videos, Excel tables, databases, Photoshop projects - all those things are not just ciphered, but also uploaded on the cloud storage. Regardless of the fact if this data is important or not, you will get a note to pay another sum to avoid publishing it.
Is Makop recognizable?
Being active since January 2020, Makop ransomware committed only several serious attacks. The commonly-chosen targets are small companies, and this thesis is partially confirmed by the average ransom of $40,000. Here is the list of the extensions used by that ransomware family. Extensions are sorted by their chronological order:
- .makop
- .CARLOS
- .shootlock
- .shootlock2
- .origami
- .tomas
As you can see, this family does not breed entities. The majority of its attacks was committed under the .makop extension, and .CARLOS is in second place. All other extensions were used not more than 2-3 times, and the reason for such a situation is not obvious. Makop group, in contrast to LockBit, for example, does not have such an oddity on their image, so using the same extension at least gives the analysts the ability to predict the further steps of this virus.
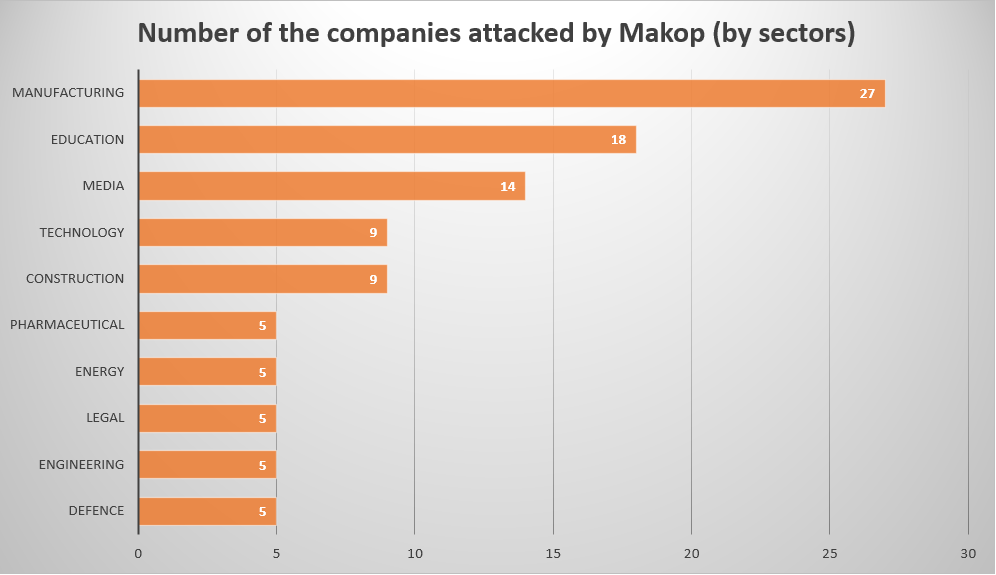
The orientation of this ransomware is quite typical for any other ransomware group that aims at corporations. Makop generally aims at companies that belong to manufacturing industries, but these corporations are not the single target. Aiming at educational, media and pharmaceutical organizations says clearly about the opinion of Makop group at “ethical hacking” - they just ignore it. A lot of ransomware groups agreed to avoid attacking the aforementioned sectors, since they are vital for national security - but Makop thinks otherwise.
The average ransom amount for this ransomware group is about $15,000. This sum is pretty small compared to their rivals - for example, LockBit asks for about $85,000, and the average ask of Conti group is almost $1 million (~$950,000). Sure, the ransom amount depends on the size of the attacked corporation - small clearing firms will not be able to pay $100,000, for example, since their turnover is too small. But it still does not make the activity of Makop group something normal - burglars must be imprisoned.
