The modern Internet space is like an endless ocean, where every wave can hide a danger. If you think you know all the possible types of scams, viruses, and attacks, then get ready for some surprises. Fraudsters are constantly inventing new and unexpected methods for propagating their malware. I found 3 most unusual, yet pretty effective, malware-spreading ways, used over the last 3 years. Let’s have a peek.
Smart and brute force
This malware-spreading method is also known as “smart brute force”. Such an approach is generally used by malware that performs self-spreading. Trying to take over the device, it checks the prompt in the login window (if one is available) and adjusts the set of credentials to try. This significantly speeds up the selection process, as there is no need to process a large pack of possible passwords.
One of the clear examples is RapperBot. It checks the request and selects the appropriate credentials based on that. After that, such infections determine the architecture of the processor and infect the device. The malware itself is downloaded using various commands (such as wget, curl, tftp, and ftpget). If for some reason these methods don’t work, then the malware downloader loads onto the device using “echo” commands and still puts the device at risk.
Trusted advertisements with pitfalls
Online advertising platforms allow their clients to post short commercials to be displayed on search engines like Google or on websites, mobile apps, etc. In addition, such platforms may use search engines and websites to serve advertisements.
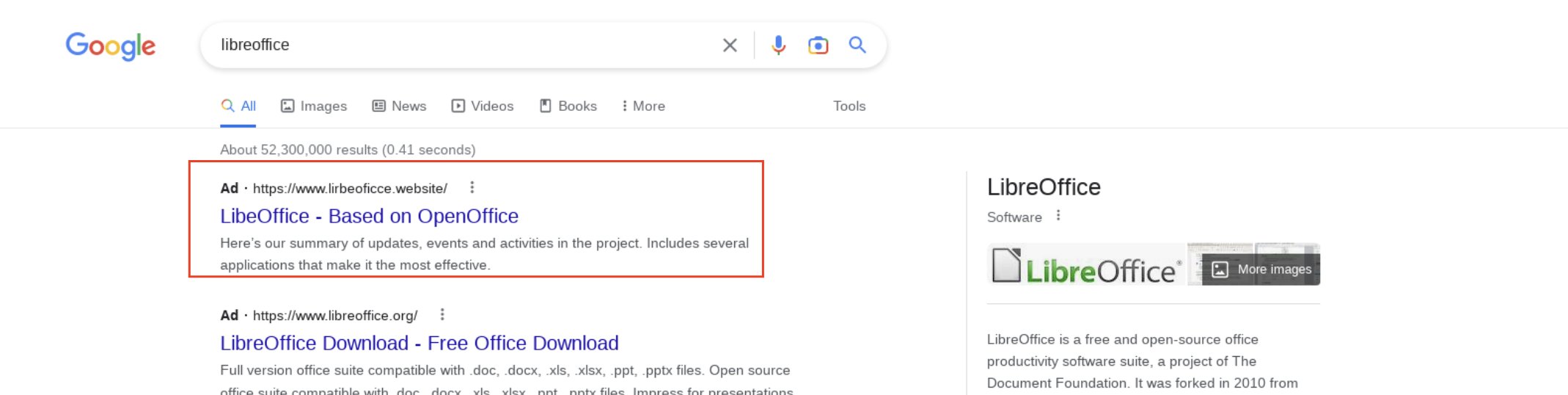
However, attackers use this opportunity to serve ads that appear to be legitimate applications, but link to phishing websites. These phishing sites contain fake installers that trick users into downloading and installing malware. It can be spyware, ransomware, coin mining – you name it. Such malware often goes unnoticed, including because nobody expects such a hidden threat. Such a form, however, has its requirements regarding the way malware is packed. The more usual form of payload – the DLL file – is not suitable, thus crooks are forced to use bloated file sections to imitate a genuine installer.
This particular method is often used by Rhadamanthys malware. Rhadamanthys, an information-stealing malware, was introduced as a MaaS platform on a Russian-speaking cybercriminal forum in September 2022. The malware is programmed using C/C++, while the C2 employs Golang. It can surreptitiously infect systems, collect data such as CPU information, screen resolution, supported wallets, and more, and circumvent EDR and anti-malware engines. Additionally, it employs encrypted communication with the C2. Despite being advertised in September 2022, the first instances of Rhadamanthys were only detected in early 2023. While the malware initially used phishing and spam as an infection vector, it now employs malvertising.
Infection by BitTorrent & OneDrive
We all know that every new thing is the forgotten old one. In this case, it’s rather an evolved old malware-spreading approach than a forgotten one. Hackers or unscrupulous companies are still tempted to lure users into installing useful software along with a hidden infection. Websites with pirated software offer numerous opportunities to play the new titles for free, the same as it was for years. But now hackers also apply cloud storage as a place to spread the crack – rather a new approach.
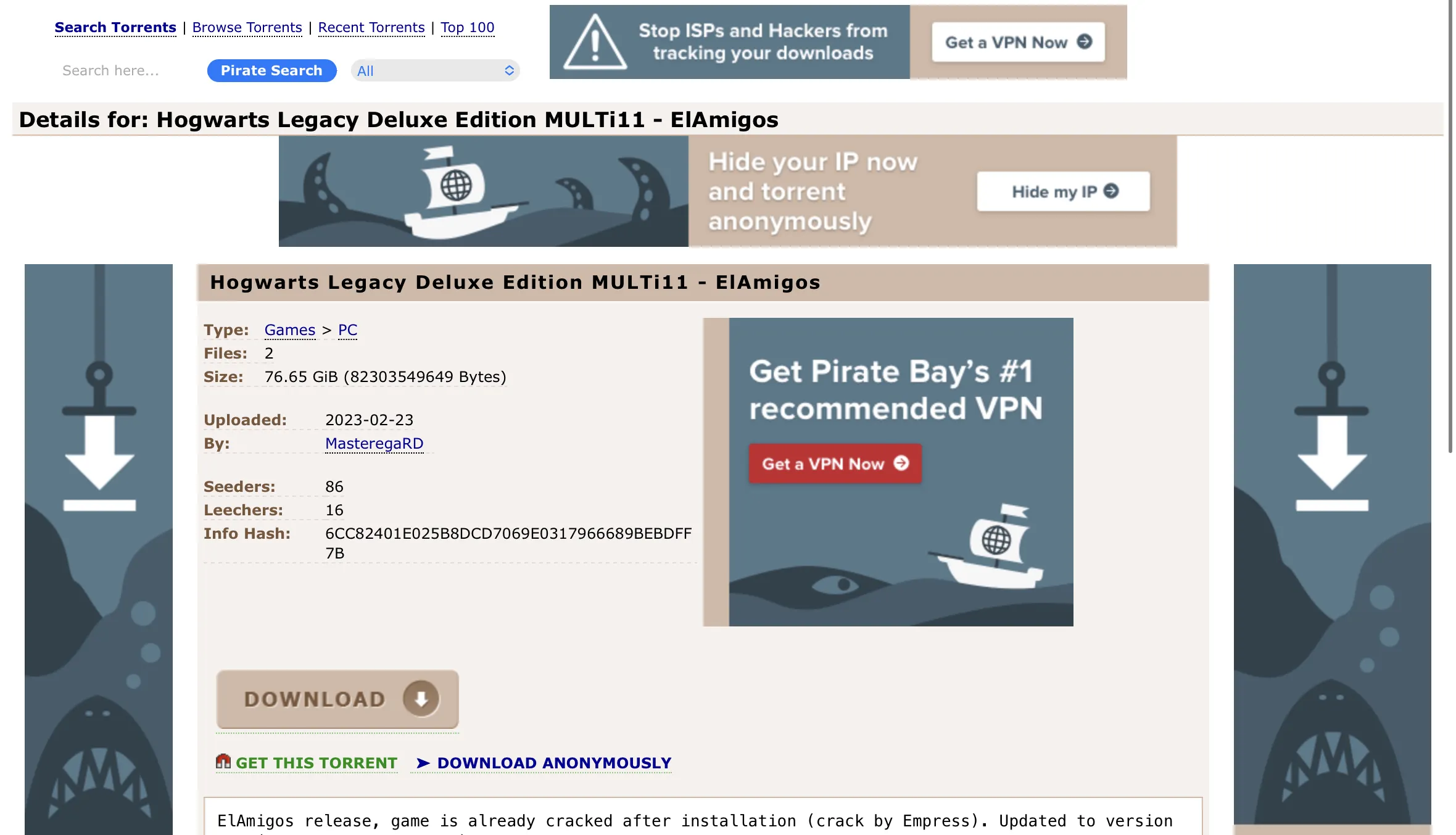
Contrary to torrent trackers, cloud storage does not rely on the number of seeds present in the network. They also have no moderation – only the file publisher can apply changes to the file. And the latter is pretty often related to malware. On torrents, the so-called “public moderation” allows to quickly locate and terminate malicious seeding . Cloud-based piracy, meanwhile, will be able to spread malware until the storage moderators do not ban the crook. Still, this may take weeks or even months.
Lately, it has become noticeable that users unwittingly download not only the desired software but also a miner and observer onto their computers. The observer checks for system overload, monitors processes that consume excessive energy (such as games), and activates the miner in their absence. However, if the owner decides to launch a game, the observer detects it and the miner stops and goes into hiding. This is done to keep the miner unnoticed within the system. As a result, the device owner remains unaware of the prolonged clandestine activities taking place.
How to stay protected?
- Update and fix your system. Malicious software often exploits vulnerabilities in outdated software to gain access to your device. It is also recommended to track cybersecurity news – they will help you to see modern malware trends and get useful advice regarding system security.
- When downloading and installing software, it’s important to exercise caution, particularly if you’re using free resources like BitTorrent and OneDrive. To ensure the safety of your device, only download programs from trusted sources. Cracked software and pirated films are not only illegal but also expose you to a significant risk.
- Be careful with online advertisements that appear to be legitimate programs or offer something too good to be true. Do not click on suspicious links and do not download unknown software. To enhance your system security, make sure to keep your software updated and patched, as malicious software often exploits vulnerabilities in outdated software.
- It’s crucial to use strong and unique passwords for all your online accounts to ensure their security. One way to generate and securely store your passwords is by using a password manager. Keeping your passwords safe and secure can help prevent unauthorized access to your accounts. It’s also important to regularly update and patch your system to address potential vulnerabilities that malicious software could exploit.
- Use trusted antivirus software and keep it up to date. Having a proper security tool in your system will make your life much, much easier. To be sure about the efficiency, it is recommended to choose ones with proactive protection and network security. Gridinsoft Anti-Malware can help detect malicious software and prevent your device from getting infected.