Ransomware is rightfully considered one of the most dangerous types of malware. It attacks individuals and companies, creating a mess in their files and paralysing their work. And even being such a devastating malware, it manages to have its own favourites. Let’s have a look at the most notorious ransomware attacks that ever happened.
What is ransomware?
If you are not completely familiar with this malware type, let me remind you about it. Ransomware is malicious software that aims at ciphering the files within the attacked system. Once finished its job, it notifies the user about what happened with numerous ransom notes, pop-up windows or the like. These notes also contain information about the ways to pay the ransom. A common way for that is paying in cryptocurrency by sending it to a designated wallet. Sums vary depending on the target: individuals usually pay $500-1000, while the average ransom for corporations is around $150,000.
Ransomware does not appear out of the blue; it is created by skilled hackers who do their best by making the cipher unbreakable, and the exact malware – undetectable. Under those conditions, the ones who create ransomware rarely do the dirty job – exactly, distributing it to the victims. They grant this task to other cybercriminals, who purchase the malignant thing and manage it as they wish. Besides paying for the “product”, affiliates commit pay-offs for each successful attack – a share of the ransom they receive. This form is called “ransomware-as-a-service”, or RaaS. Needless to say that most of the risks related to possible accusations and detaining also lay upon the affiliates’ heads. Ransomware seems to give birth to a perfectly-organised cybercrime, where millions of dollars circulate each month.
Notorious Ransomware Attacks You Should Know About
What can be named an attention-worthy ransomware attack? From the perspective of an attacked victim or a company, their cases are as important as any other. But get a look from a bigger scale – and most of the cases will be pretty much the same. Here, we will review ransomware attacks that became a worldwide phenomenon and hit the headlines of newspapers.
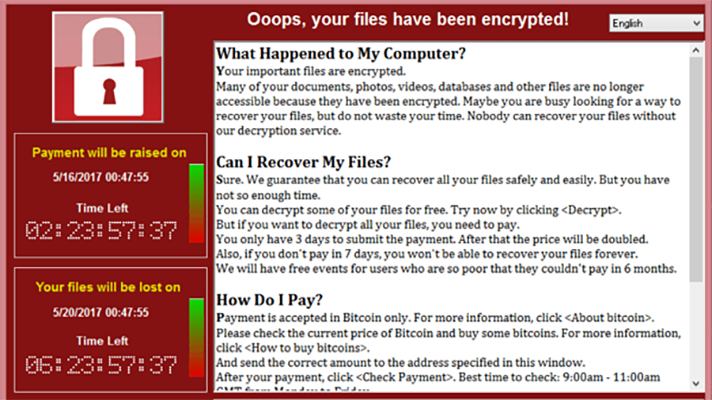
WannaCry Ransomware attack
Active: 12-15th May 2017.
Damage: ~200,000 computers over the world; billion-dollar idle losses
Ransom: Total of $130,634 (327 payments)
WannaCry is possibly the most-known attack among the ones that have ever happened. Some say it was the first attack that rendered ransomware a real danger in the eyes of ones who learn of it. An outbreak that happened in May 2017 touched 150,000 machines on the first day. It generally targeted corporations in Russia, Ukraine, India and Taiwan. On the second day, security analysts found a way to suspend the malware execution and make it self-destruct. That seriously restricted the further spreading and fixed the victims counter at the number of around 200,000. The investigation following the attack shows that key threat actors are two North Korean citizens. They used the EternalBlue exploit to deploy ransomware. North Korean cybercrime group Lazarus – the only one in this country – did not claim responsibility.
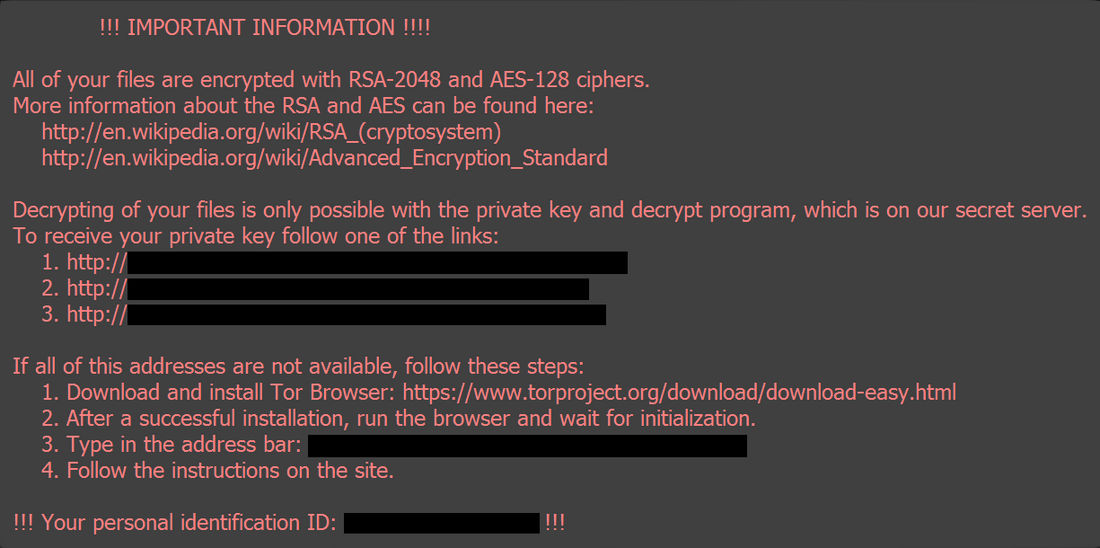
Locky Ransomware attack
Active: 2016-2017
Damage: up to 1 million computers
Ransom: 0,5-1 Bitcoin ($275-450)
The outbreak of Locky ransomware had an extended time. Since the beginning of 2016, it has been delivering its first version, using the Necurs botnet. This network resided in both single-user computers and ones placed in corporations. Originally, malware was spread through classic email spam – with an Office document that contains malicious macros attached. Around June 2016, the botnet was shut down due to a glitch in the command centre. But soon after everything came back to normal – with even more intensive spamming. Besides almost ceased activity by the end of 2017, it still appears here and there, without any system.
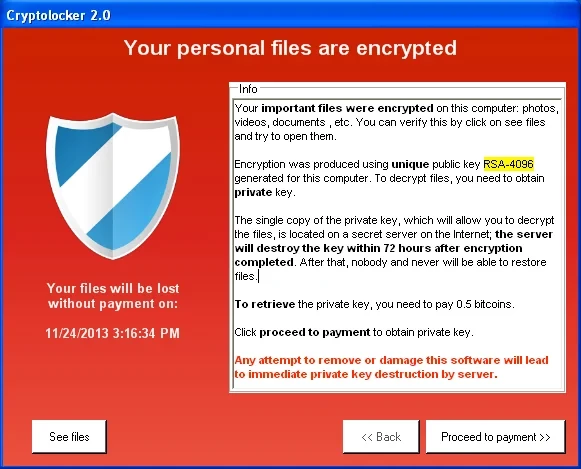
Cryptolocker malware attack
Active: September 2013 – May 2014
Damage: around 70,000 machines, 42,928 BTC paid
Ransom: $400 (in Bitcoin)
Cryptolocker appears to be one of the earliest cases of a large-scale ransomware attack. After the mess created by amendments to bank regulation laws, hackers were forced to seek another way of payment, and cryptocurrencies were the best option. The distribution of this malware generally relied on malicious email attachments and extensions doubling. Victims were receiving a ZIP file, which contained what looked like a PDF file. In fact, it was an executive file with a .pdf.exe extension, and a PDF file icon attached to it. Cryptolocker ransomware is also notable for ransom sum increase if victims fail to pay within 72 hours. In 2014, a free decryption tool appeared, making this malware useless.
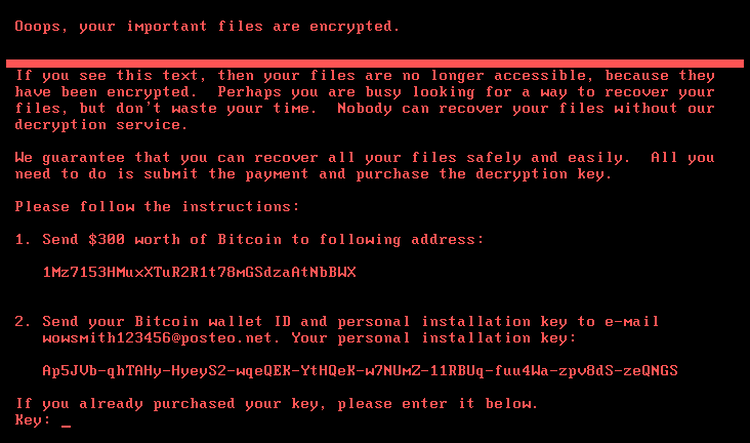
Petya/NotPetya
Active: June 2017
Damage: $10 billion losses
Ransom: $300
Analysts detected the first samples of this ransomware in March 2016, but its premiere happened in June of the next year. This attack is considered to be politically motivated, as the hackers who managed the attack are from Russia, and the country that suffered the most was Ukraine (over 80% of total submissions). Moreover, the attack happened at the end of Ukrainian Constitution day – a typical Russian “spoil-the-celebration” act. Still, several European countries reported the attack as well. Malware deployment was performed through the backdoor in the tax preparation software M.E.Doc, widely used in Ukrainian companies. The attack was reportedly prepared by the Russian hacking group Sandworm, however, they deny all the blames.
Conti Ransomware group
Active: Late 2019 – March 2022
Damage: over 1000 companies hacked
Ransom: average 110,000$, peaking at $25 million
Conti is yet another cybercrime gang that is tied to Russia. Contrary to numerous others who are tagged as Russian, they never deny their origins. The group started their activity in November 2019, and quickly gained the image of principleless rascals. Striking any kind of company and organisation, Conti group earned huge capital as well. At some point, their average ransom peaked at ~$1 million. Key malware spreading ways this group opted for is email spamming and RDP brute force. They actively used double extortion – when the victims should pay not only for file decryption but also for keeping the leaked data in secret. As CISA researchers say, Conti also applies pretty unique way of RaaS implementation. Instead of collecting commission payments for each successful attack, the administration gets the entire cash flow and pays a “salary” to its hackers-for-hire.
Ryuk Ransomware gang
Active: Since 2019
Damage: total ransom amount exceeds $150 million
Ransom: $100,000 – $500,000, peaking at $5.3 millions
Its name comes from the Death Note manga character. Ryuk ransomware is believed to be operated by Russian cybercrime gangs, but there is no straightforward evidence for it. Another study describes that Ryuk may probably be operated by the aforementioned Lazarus Group. This malware bears upon TrickBot dropper in its spreading; still, crooks don’t disdain using RDP vulnerabilities. Contrary to most other groups that attack companies, it does not use double extortion technique. There are no facts of using the RaaS model either.
DarkSide Ransomware
Active: August 2020 – June 2021
Damage: 90 known victims
Ransom: $200,000 – $2 million
DarkSide gang is a representation of taking French leave. This cybercrime gang is most known for its attack upon Colonial Pipeline, which led to massive fuel supply disruptions along the entire U.S. East Coast. After that case, the FBI started an investigation of the case, and DarkSide admins hastened to claim their shutdown. Aside from that, hackers often claimed that they’re apolitical, despite researchers detecting their origins in Russia. Studies also believe that group is a spin-off from the other gang – REvil.
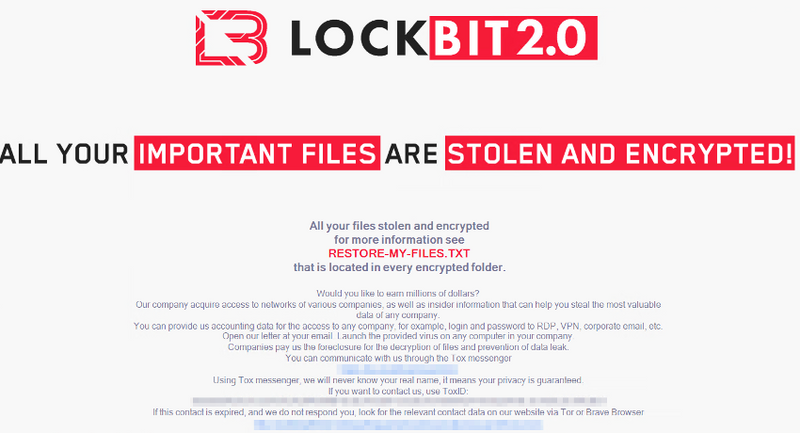
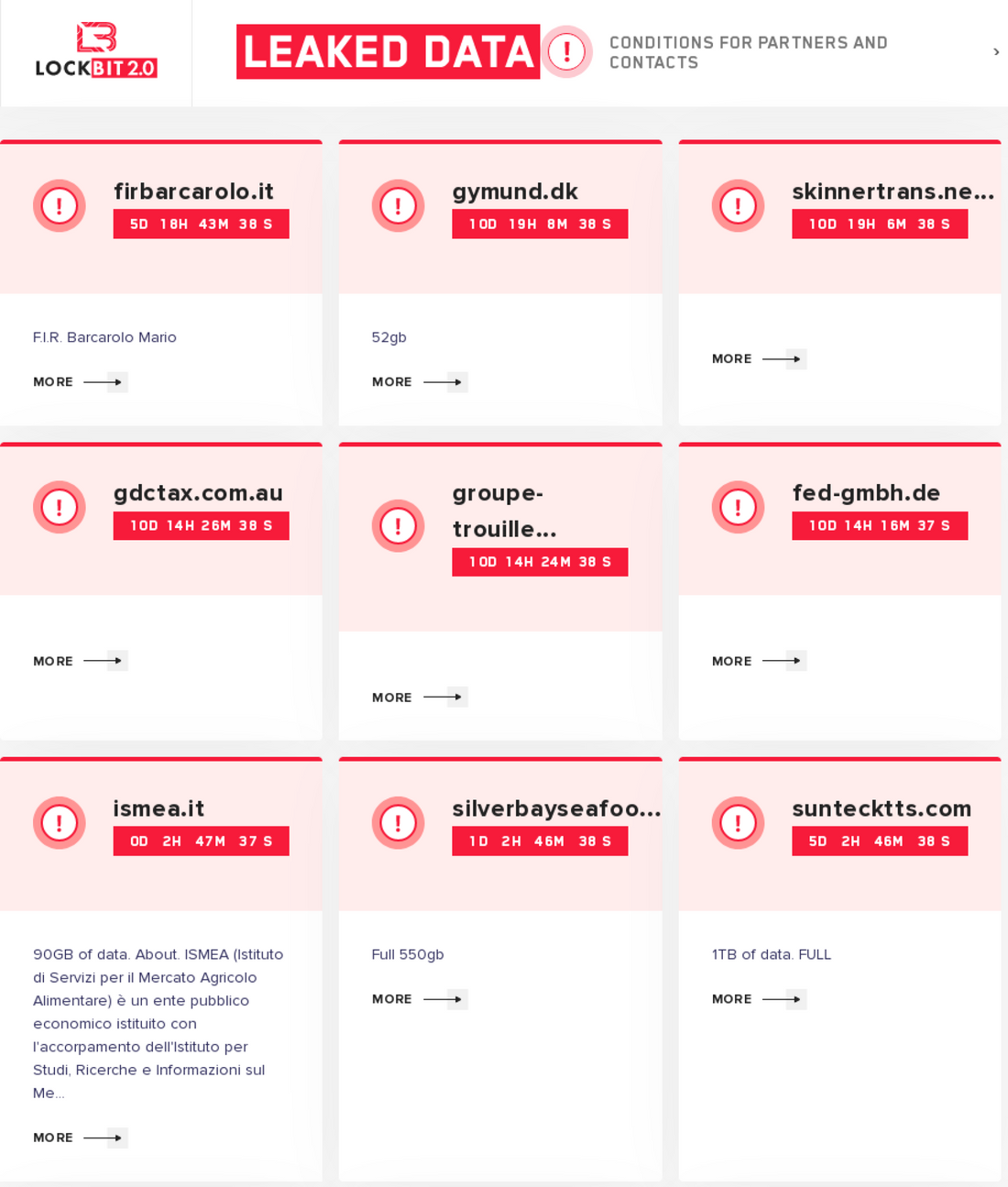
LockBit group
Active: September 2019 – now
Damage: 850 companies ransomed
Ransom: ~$85,000 at average
LockBit is an example of a next-generation ransomware gang. This group applies a thorough candidate pick and watches for affiliates to follow the “codex”. They declared about avoiding the attacks on critical infrastructure, government, non-profit and educational institutions. And they really do so – even if such an attack happens, they quickly retreat, giving out a decryption key for free. Gang administrators proved to be pretty talkative, giving interviews here and there, although remaining anonymous. LockBit group is also famous for its software, which provides one of the fastest file encryption and data extraction capabilities. They jokingly name themselves “postpaid pentesters”.
Magniber Ransomware
Active: Late 2017 – now
Damage: ~250 users attacked
Ransom: 0.35–0.7 BTC
Ransomware that strikes individuals rarely opts for such a sophisticated spreading way as vulnerability exploitation. Social engineering is easier and cheaper – thus way more proficient. Magniber ransomware is an exclusion that proves that fact. Despite being an old-timer – it was first seen around December 2017 – this malware barely scored a hundred victims by the beginning of 2022. Its activity is inconsistent, with numerous idle periods which may last more than 1 year. Analysts pay attention to Magniber because of its unique behaviour and attacking almost exclusively South Korean folks. In early 2022, it saw another activity spike – possibly, the biggest in its entire history. Using security breaches in the Chrome browser, it got over a hundred victims.
Cl0p ransomware
Active: September 2019 – now
Damage: >1000 victims/~$500 million in ransoms
Ransom: $80,000 – $220,000
Cl0p is an example of a sole ransomware sample used by multiple different cybercrime groups. Being the further development of CryptoMix ransomware, it has seen active usage in attacks of TA505, FIN11, UNCA2546 and UNCA2582 groups. All of them originate from Russia or Russian-speaking countries. Key method used to spread Cl0p is spear phishing that contains a malicious attachment. For a better disguise, the attached file has a certificate that legitimates it for protection systems. Along with the ransomware, the payload commonly contains an SDBOT worm that acts as stealer malware.
Egregor Ransomware gang
Active: early 2020 – February 2022.
Damage: 71 companies hacked
Ransom: averages at $700,000
Egregor made a brief, but bright show at the edge of 2021. Some analysts believe that its key actors were recruited from the Maze gang, which dissolved in October 2020. Exploiting RDP vulnerabilities, it was breaking into the networks of pretty large companies. Among their victims are K-mart retail chain and Randstad – a recruiting platform. Despite being formally shut down, the group never claimed that directly. Their last attack happened in December 2020. In February 2021, some of the group members were captured in a joint action of Ukrainian and French cyberpolice. After that, the entire gang went offline. In February 2022, one of Egregor members published the decryption keys for Maze, Sekhmet and Egregor ransomware victims. That may be not that straightforward, but a pretty clear claim about the shutdown.
Babuk Ransomware
Active: December 2020 – July 2021
Damage: ~12 companies hacked
Ransom: $100,000
Similarly to the prior gang, Babuk had a pretty short lifetime of less than a year. Still, ransomware samples that use Babuk codebase keep appearing in the wild even in 2022. The first versions that can be attributed to Babuk appeared in October 2020, but they had no name. Vasa locker was the first name for that ransomware, appearing around November 2020. Babuk name was seen in usage in December of the same year. Group was attacking primarily the companies with gross profits of over $4 million. It is notable for attacking Washington’s Metropolitan Police Department, asking for a ransom of over $4 million. Key penetration ways this group used are RDP vulnerabilities and email phishing. Its end was pretty notorious – a 17-year-old gang member leaked the administrative panel credentials and a source code, claiming he was suffering from terminal cancer and wants to “live as a human”.
Phobos Ransomware
Active: early 2019 – now
Damage: not calculated
Ransom: averaged at ~$37,000
Phobos appears to be a unique malware by different factors. It is a rare example of malware that targets both companies and individuals. Although companies they usually attack are small, they compensate for that with a number of attacks. Key spreading ways Phobos applies is email phishing and RDP exploitation for individuals and companies correspondingly. The peculiar moment about Phobos is that the same group seems to be spreading Dharma ransomware as well.
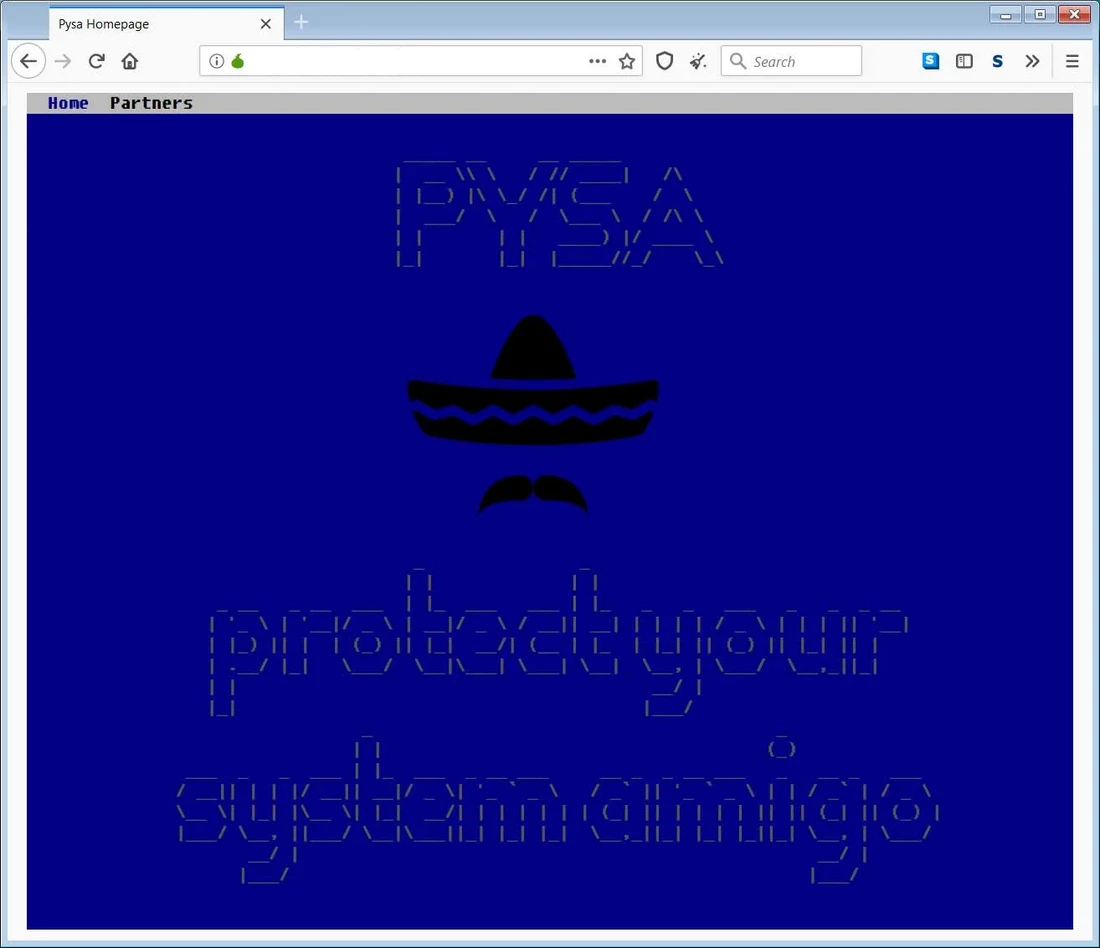
PYSA Ransomware group
Active: October 2019 – now
Damage: up to 800 companies hacked
Ransom: $347,000 at average
PYSA is an acronym that stands for “Protect your system amigo”. This, and the use of a sombrero and moustache pic on their logo on the Darknet leak site definitely refers to Mexican origins. Aiming at corporations, it uses a whole bunch of tools in order to create as a convenient environment for ransomware deployment as possible. To get into the network, crooks generally use email phishing. Because of a massive amount of manual work to do after gaining the initial access, this ransomware works in a full-manual mode.
That is roughly a half of all attacks I am willing to talk about. Consider checking out the second part of this list to be aware of even more noteworthy ransomware attacks!