SapphireStealer is one such new information stealer to steal various browser credential databases and files containing users’ sensitive information. The codebase for SapphireStealer was made public on GitHub on December 25th, 2022.
According to the research, SapphireStealer can steal a wide range of information from the target system, and be flexible in setup and evasion methods. Attackers can use the stolen information to launch attacks such as espionage or demand ransom payments through extortion.
How does SapphireStealer work?
Like many other malware that have recently emerged on the dark web, SapphireStealer is designed to collect information about the host, including browser data, files, and screenshots. The stolen data then exfiltrated as a ZIP file via a Simple Mail Transfer Protocol (SMTP).
What sets SapphireStealer apart is that its source code was made public in December 2022, making it easier for attackers to experiment with the malware and evade detection. They have even added new data exfiltration methods like using a Discord webhook or Telegram API.
SapphireStealer is written in .NET and offers straightforward but effective functionality. The information it can steal includes host information, screenshots, cached browser credentials, and files that match a predefined list of file extensions stored on the system.
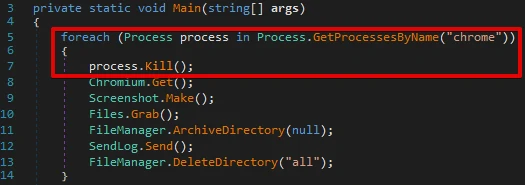
Upon execution, the malware checks if any browser processes are currently running on the system. Then it scans the list of running processes for names that match the following:
- Chrome
- Yandex
- MS Edge
- Opera
If it detects any matches, the malware terminates the processes using Process.Kill(). Here is an example code snippet that shows how to accomplish this task specifically for Google Chrome.
A .NET malware downloader called FUD-Loader has been made public by the malware author. This downloader works as an add-on to the SapphireStealer module, making it capable of delivering other malware. It also allows you to receive additional binary payloads from servers controlled by intruders. The malware downloader has been used to deliver remote administration tools like DCRat, njRAT, DarkComet, and Agent Tesla.
How to avoid attacks from SapphireStealer ?
Here are some tips to reduce the risk attacks from SapphireStealer and similar stealers:
Install updates
It is crucial to promptly update the operating system, browser, and other applications to minimize the risk of infostealers being distributed via known browser vulnerabilities.
Use multi-factor authentication
Having Multi-factor authentication (MFA) enabled is an effective security measure in safeguarding accounts, tools, systems, and data repositories from unauthorized access. If an intruder manages to steal your login credentials, MFA will prompt a secondary layer of authentication, making it more challenging for them to enter the compromised account. Additionally, secure password storage can be a useful supplementary option to ensure utmost protection.
Avoid pirated software
Using pirated software can be dangerous as it often contains malware. Pirates do this to make money. It is always better to use legitimate applications. Nowadays, there are many free, freemium, and open-source alternatives available that remove the need to take the risk of using pirated software.




