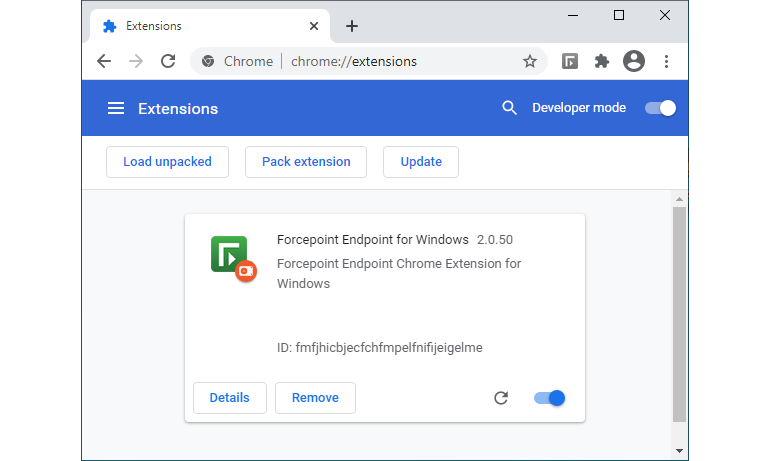
Croatian researcher Bojan Zdrnja discovered a malicious Chrome extension abusing Chrome Sync.
If you do not use Chrome, let me remind you that this function is applied to synchronize data between different user’s devices, and stores copies of all user bookmarks, browsing history, passwords, as well as browser settings and browser extensions on Google cloud servers.
However, as it turned out, synchronization can be used to send commands to infected browsers, as well as steal data from infected systems, bypassing firewalls and other means of protection.
Zdrnya writes that in the course of the incident he studied, the attacker gained access to the victim’s computer, but was unable to steal the data, since it was inside the employee portal. Then the hacker downloaded a malicious Chrome extension to the victim’s machine and launched it through Developer Mode.
The extension masked itself as a security product from Forcepoint and contained malicious code that abused the synchronization function, allowing an attacker to control the infected browser. In this case, the extension was used to manipulate data in an internal web application that the victim had access to.
The malicious code found in the extension allowed an attacker to create a special text field to store token keys, which were then synchronized with Google cloud servers.
According to the researcher, any data can be stored in such a field: it could be information collected by a malicious extension about an infected browser (for example, usernames, passwords, cryptographic keys, etc.), or, on the contrary, commands that the extension must execute on the infected host.
Thus, a malicious extension can be used to “drain” data from corporate networks into the attacker’s Chrome, and bypassing local protection tools. After all, stolen content or commands are transmitted through the Chrome infrastructure, and the Google browser is usually allowed to work and transfer data without hindrance, that is, the hacker’s activity will not raise suspicion and will not be blocked in most corporate networks.
Instead, the researcher advises using corporate Chrome features and group policies to block or tightly control extensions that can be installed in the browser.
As I mentioned, recently Google Chrome fixed two 0-day vulnerability in two week, that was under attacks.