Fortinet specialists have discovered a new GoTrim malware written in Go that scans the Internet for WordPress sites and brute-forces them by guessing the administrator password.
Such attacks can lead to the deployment of malware, the introduction of scripts on websites to steal bank cards, the placement of phishing pages, and other attack scenarios that potentially affect millions of users (depending on the popularity of the hacked resources).
Let me remind you that we also wrote that New Version of Truebot Exploits Vulnerabilities In Netwrix Auditor And Raspberry Robin Worm, and also that Ukraine Was Hit by DDoS Attacks from Hacked WordPress Sites.
Experts write that GoTrim is still in development, but already has powerful features. Botnet attacks began at the end of September 2022 and are still ongoing.
Malware operators provide their bots with a long list of target resources and a list of credentials, after which the malware connects to each site and tries to brute force administrator accounts using logins and passwords from the existing list.
If successful, GoTrim logs in to the hacked site and sends information about the new infection to the command and control server (including the bot ID in the form of an MD5 hash). The malware then uses PHP scripts to extract the GoTrim bot client from a hard-coded URL, and then removes both the script and the brute force component from the infected system.
Actually, GoTrim can work in two modes: “client” and “server”. In client mode, the malware initiates a connection to the botnet’s control server, while in server mode it launches an HTTP server and waits for incoming requests. For example, if a hacked endpoint is directly connected to the Internet, the malware uses server mode by default.
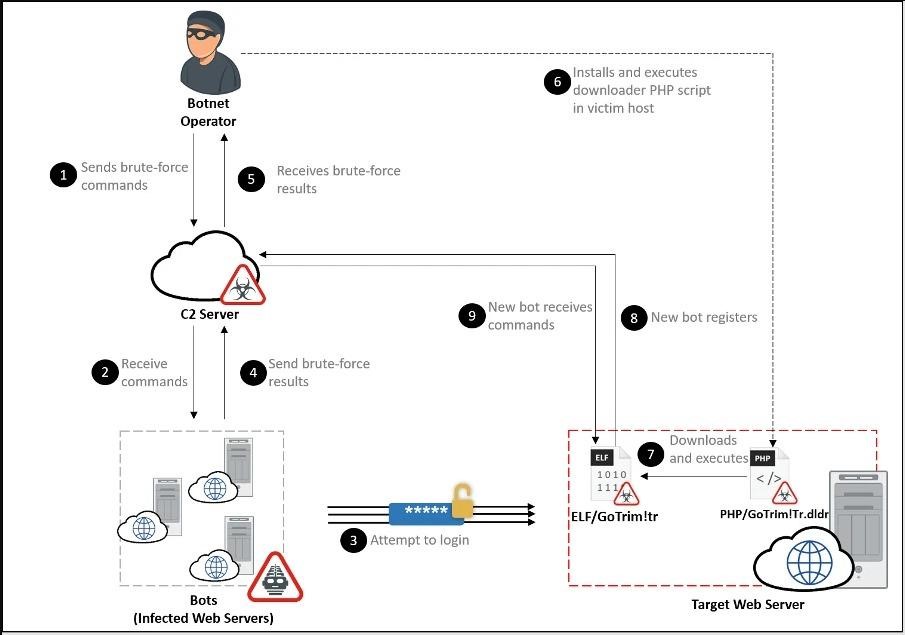
GoTrim sends requests to the attacker’s server every few minutes, and if the bot does not receive a response after 100 attempts, it will stop working.
The C&C server can send the following encrypted commands to GoTrim:
- check provided credentials for WordPress domains;
- check provided credentials for Joomla! (not yet implemented);
- check provided credentials for OpenCart domains;
- verify provided credentials for Data Life Engine domains (not yet implemented);
- detect installations of CMS WordPress, Joomla!, OpenCart or Data Life Engine in the domain;
- eliminate malware.
Interestingly, the botnet tried to avoid the attention of the WordPress security team and did not attack sites hosted on WordPress.com, only targeting sites with their own servers. This is implemented by checking the Referer HTTP header for “wordpress.com”.
It is also noted that if the target site uses a CAPTCHA plugin to fight bots, the malware will detect it and download the appropriate solver. GoTrim currently supports seven popular CAPTCHA plugins.
In addition, experts noticed that the botnet avoids attacking sites hosted on 1gb.ru, but the exact reasons for this behavior have not been established, although it is very possible that the hackers who created the malware are simply in Russia, but are looking for an opportunity to launder money.
To protect against GoTrim and other similar threats, experts recommend that site administrators use strong passwords, do not reuse passwords, and always use two-factor authentication, if possible.




