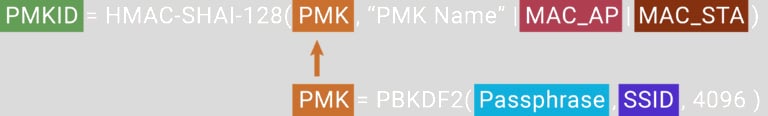CyberArk specialist Ido Hoorvitch hacked 70% of Wi-Fi networks in his native Tel Aviv, seeking to prove that home networks are poorly secured and easily compromised.
To conduct the experiment, Horwich walked around town with sniffing equipment and collected data from 5,000 network hashes. Next, he exploited a vulnerability to obtain the PMKID hash normally generated for roaming. The PMKID hash consists of the network SSID, passphrase, MAC address, and a static integer.
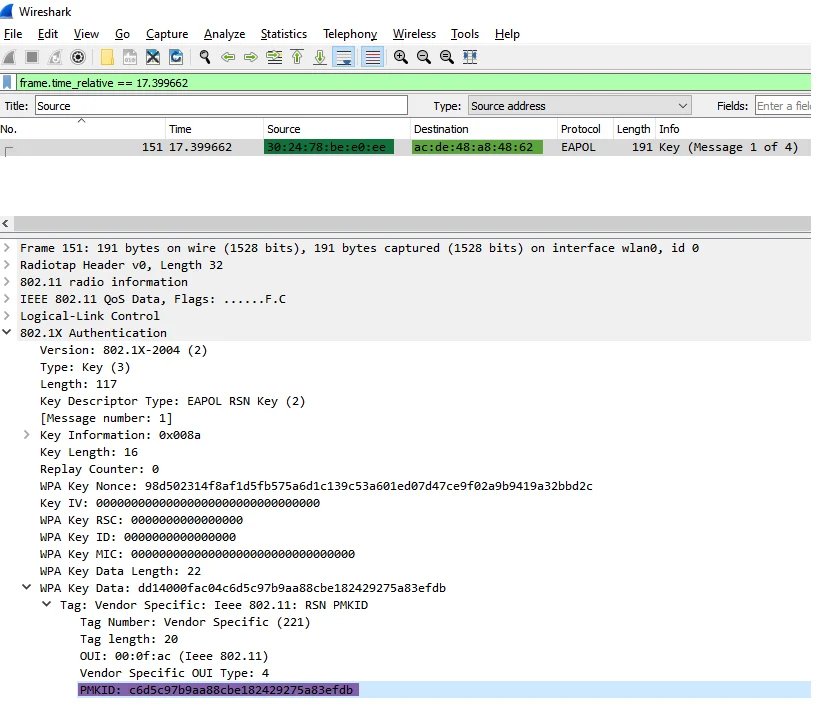
To get the PMKID hashes, he used a $ 50 AWUS036ACH ALFA NIC, which could act as both a monitor and a packet injection tool, and then analyzed them using WireShark in Ubuntu.
Using the method of Jens “atom” Steub (lead developer of Hashcat), Horwich collected PMKIDs, which were then cracked to obtain passwords.
So Horwich started with mask attacks to identify people using their mobile phone number as a password for Wi-Fi (a common occurrence in Israel). To crack such passwords, it is necessary to calculate all variants of Israeli phone numbers, and these are ten digits, always starting with 05, which leaves only eight digits.
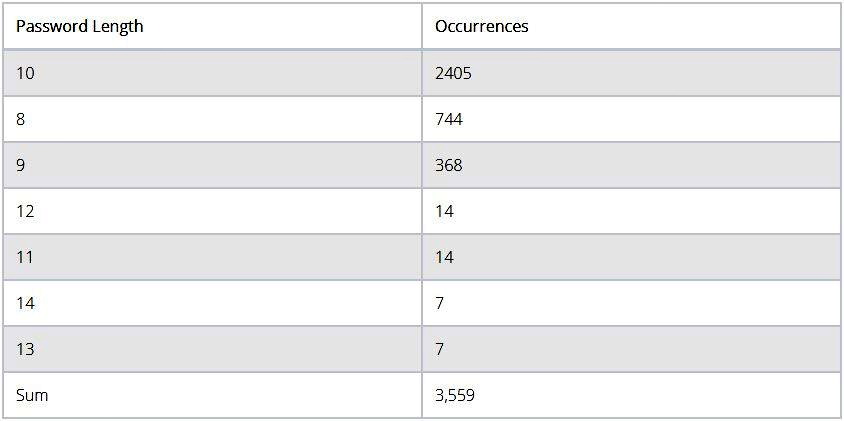
Using a regular laptop and this technique, the researcher successfully compromised 2,200 passwords at an average rate of nine minutes per password. In the next step, he switched to a dictionary attack using Rockyou.txt. This led to the rapid cracking of an additional 1,359 passwords, most of which used only lowercase characters.
As a result, Horwich successfully compromised about 70% of the passwords for the selected Wi-Fi networks and confirmed all his guesses about the poor security of Wi-Fi networks.
The specialist summarizes that users should not enable the roaming function on routers intended for personal use (WPA2-personal), because there is no need for roaming in such networks. He also notes that passwords longer than 10 letters/numbers are more resistant to cracking.
Let me remind you that Any Wi-Fi enabled devices are vulnerable to Frag Attacks issues.