Information security experts warned of an increase in the number of infections with the new version of TrueBot, primarily targeting users from Mexico, Brazil, Pakistan and the United States.
According to Cisco Talos, malware operators have now moved from using malicious emails to alternative delivery methods, including exploiting an RCE vulnerability in Netwrix Auditor, as well as using the Raspberry Robin worm.
Let me remind you that experts attribute the authorship of TrueBot to the Russian-speaking hack group Silence, which is known due to the major robberies of financial institutions.
As reported now, the attackers not only switched to new methods of delivering malware, but also began to use the custom tool Teleport to steal data, and also distribute the Clop encryptor, which is usually used by hackers from the TA505 group associated with another Russian-speaking hack group – FIN11.
Cisco Talos researchers write that they discovered several new attack vectors back in August 2022. According to their observations, Silence participants introduced their malware into 1500 systems around the world, “bringing with them” shellcodes, Cobalt Strike beacons, Grace malware, Teleport data theft tool and Clop ransomware.
It is noted that in most of the attacks detected during the period from August to September, hackers infected the systems of victims of Truebot (Silence.Downloader) using the critical vulnerability of Netwrix Auditor servers, tracked as CVE-2022-31199.
In October 2022, hackers completely switched to using malicious USB drives and the Raspberry Robin worm, which delivered IcedID, Bumblebee, and Truebot payloads to victims’ machines.
Let me remind you that in the October Microsoft report, this worm was associated with the spread of the Clop ransomware and the DEV-0950 hack group, whose malicious activity is associated with the activity of the FIN11 and TA505 groups.
As Cisco Talos now notes, Truebot operators used Raspberry Robin to infect more than 1,000 hosts, many of which were not accessible via the Internet. Most of the victims of hackers are in Mexico, Brazil and Pakistan.
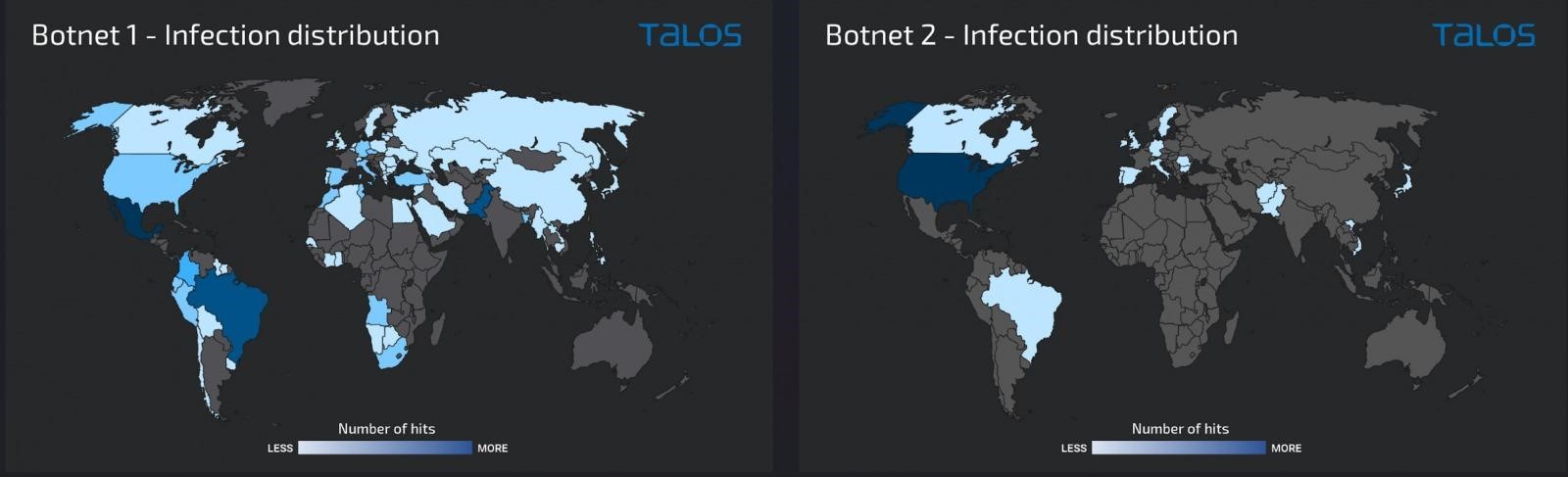
In November, hackers targeted Windows servers, whose SMB, RDP, and WinRM services can be found over the Internet. The researchers counted more than 500 cases of such infections, about 75% of them in the United States.
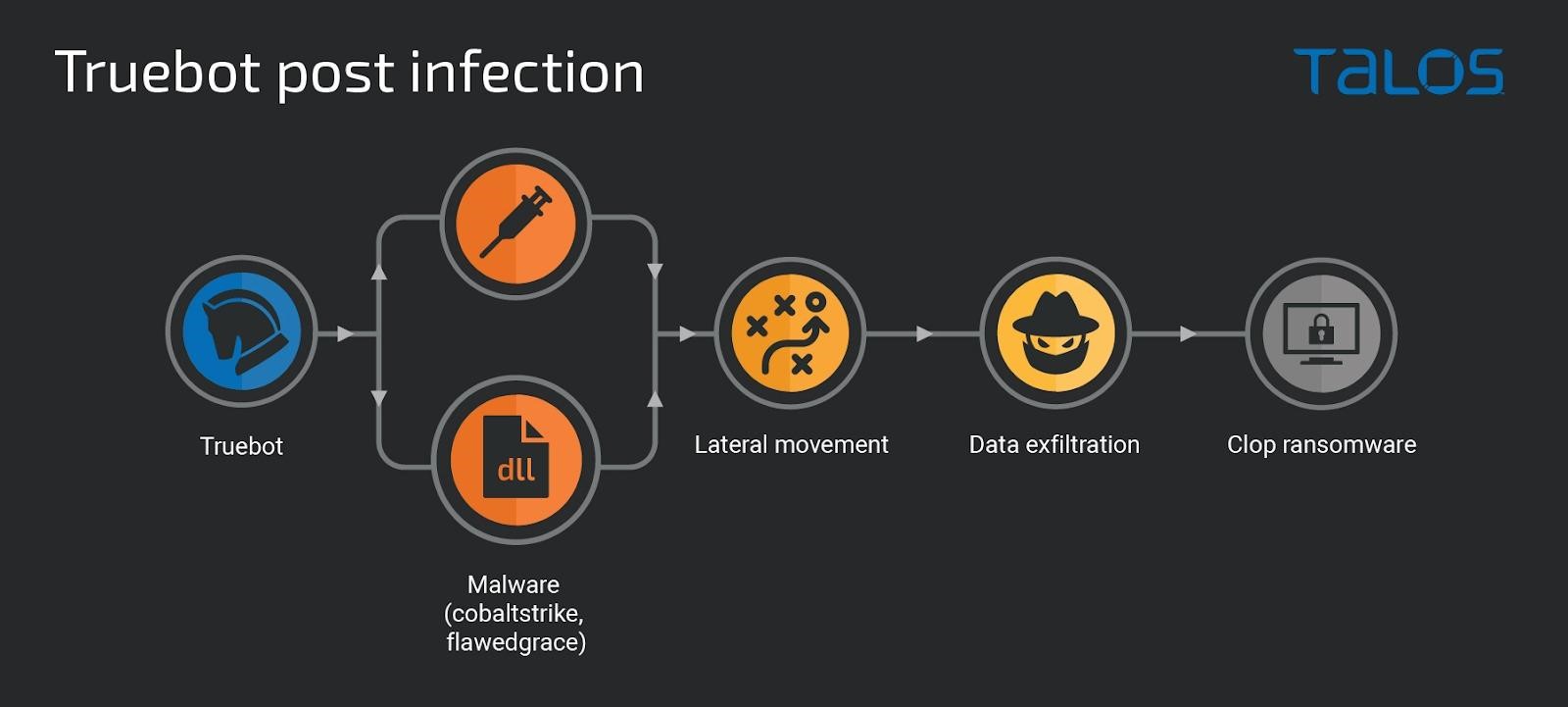
Analysts remind that in fact Truebot is a first-level module that collects basic information about the victim’s system and takes screenshots. It also extracts information about Active Directory, which helps hackers plan their next steps after an infection.
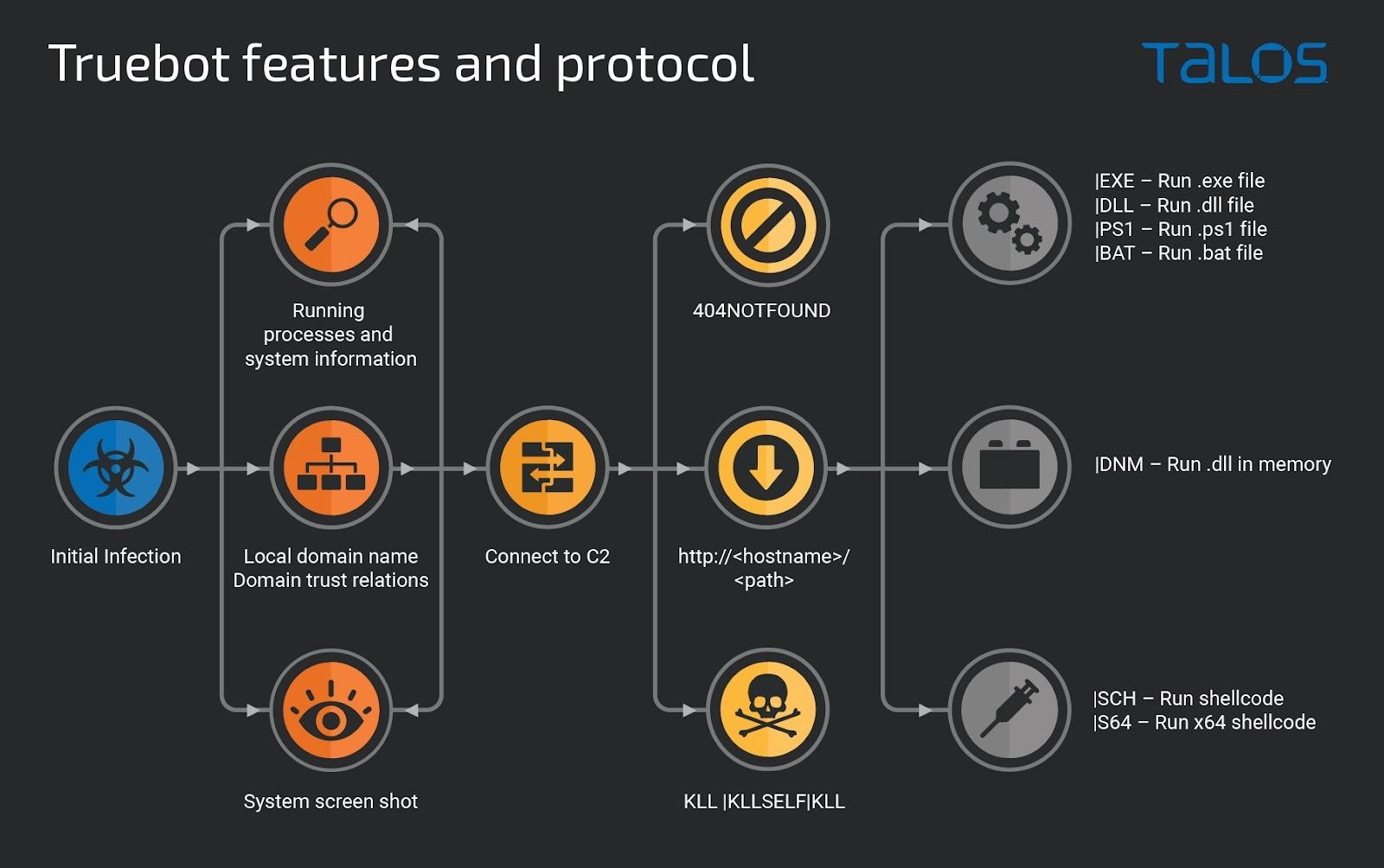
The attacker’s command and control server can then instruct Truebot to load shellcode or DLLs into memory, execute additional modules, remove itself, or load DLLs, EXEs, BATs, and PS1 files.
Also, after being compromised, hackers use Truebot to inject Cobalt Strike beacons or Grace malware (FlawedGrace, GraceWire) into victim systems. The attackers then deploy Teleport, which Cisco describes as a new custom tool written in C++ that helps to steal data silently.
The communication channel between Teleport and the C&C server is encrypted. Operators can limit download speeds, filter files by size (to steal more), or remove payloads. Teleport is also capable of stealing files from OneDrive folders, collecting victim mail from Outlook, and looking for specific file extensions.
It is noted that after lateral movement, infection of the maximum number of systems using Cobalt Strike and data theft, in some cases hackers deploy the Clop ransomware already mentioned above in the systems of victims.