Binarly analysts have discovered 23 critical UEFI vulnerabilities from InsydeH2O, which is used by many major vendors, including HP, Lenovo, Fujitsu, Microsoft, Intel, Dell, Bull (Atos) and Siemens.
Together, the researchers say these bugs could affect millions of devices, including laptops, servers, routers, network equipment, ICS, and various peripherals. In total, the problems concern the products of more than 25 suppliers.
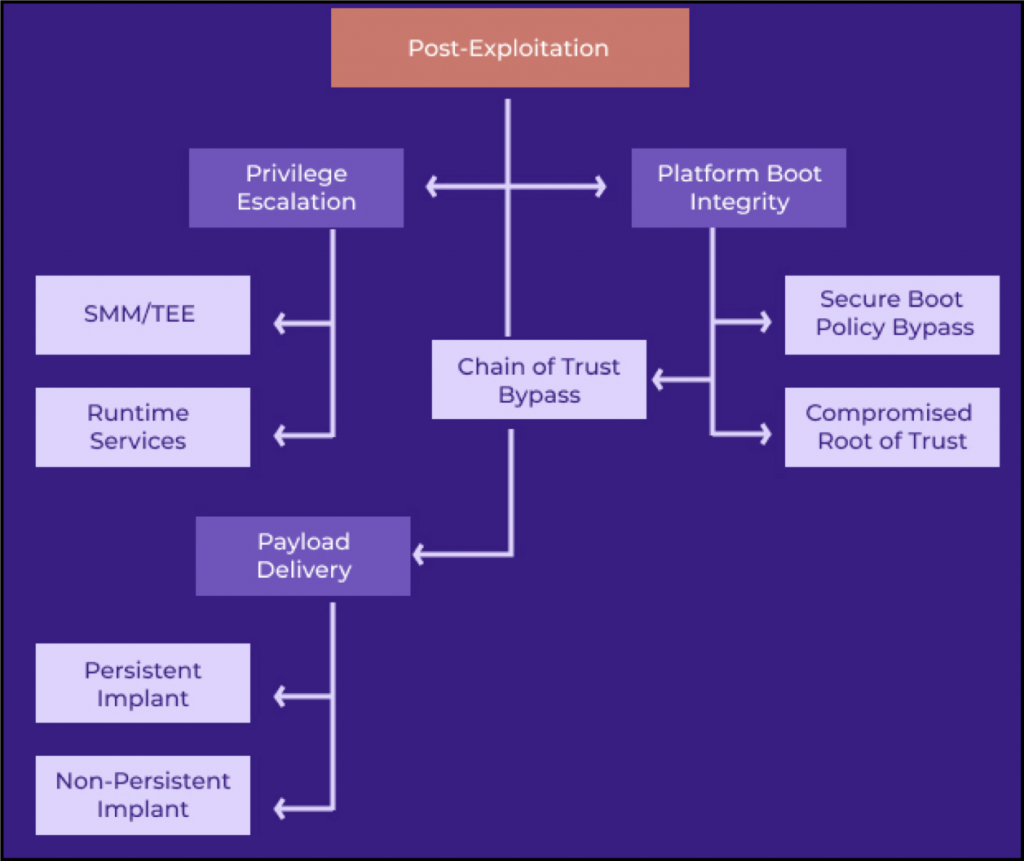
Most of the vulnerabilities were found in System Management Mode (SMM) code, which is responsible for system-wide functions such as power and hardware management.
Since SMM privileges exceed even the privileges of the OS kernel, any security issues in this space can have extremely serious consequences. In particular, a local or remote attacker with administrator rights will be able to perform the following actions:
- disable hardware security features (SecureBoot, Intel BootGuard);
- install software that will be firmly fixed in the system;
- create backdoors and hidden communication channels to steal confidential data.
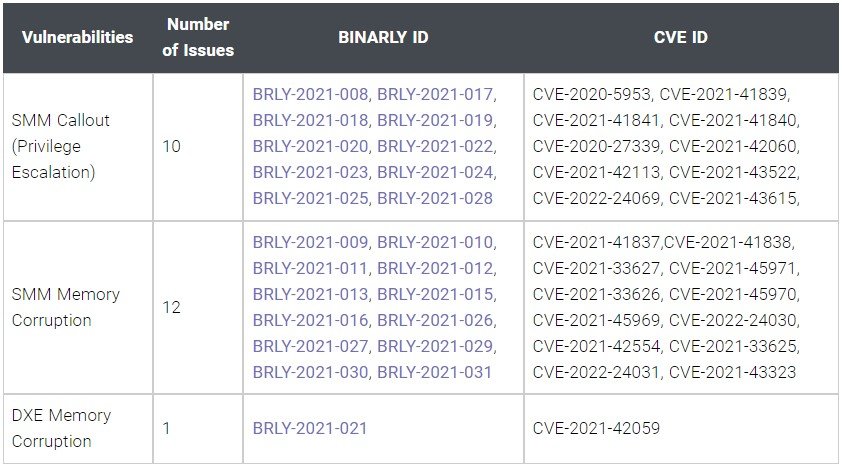
The most dangerous of all bugs found are CVE-2021-45969, CVE-2021-45970, and CVE-2021-45971, which scored 9.8 out of 10 on the CVSS vulnerability rating scale. Additional 10 vulnerabilities could be exploited for privilege escalation, 12 related to memory corruption in SMM, and another vulnerabilities related to memory corruption in the InsydeH2O Driver Execution Environment (DXE).
At the moment, the American CERT has confirmed the presence of vulnerabilities in the products of three product vendors: Fujitsu, Insyde Software Corporation and Intel (only bug CVE-2020-5953).
Let me remind you that we also wrote that Microsoft warns of dangerous vulnerability in Surface Pro 3 devices.
InsydeH2O developers from Insyde Software have already released patches that fix all the bugs found, and have also published security bulletins, where each problem is analysed in detail. Unfortunately, these updates must first be accepted by OEMs before being rolled out to affected products. This whole process will take a lot of time, that is, patches will reach end users for a long time.
You may also be interested in reading that due to Razer Synapse vulnerability, connecting a mouse to a Windows machine gives system privileges.