Security firm Volexity has warned that a previously unknown Chinese hack group is exploiting a 0-day vulnerability in Zimbra’s collaborative software.
According to official statistics, more than 200,000 enterprises in 140 countries around the world use Zimbra, including more than 1,000 government and financial institutions. The researchers write that using the 0-day vulnerability, attackers gain access to the mailboxes of European authorities and the media.
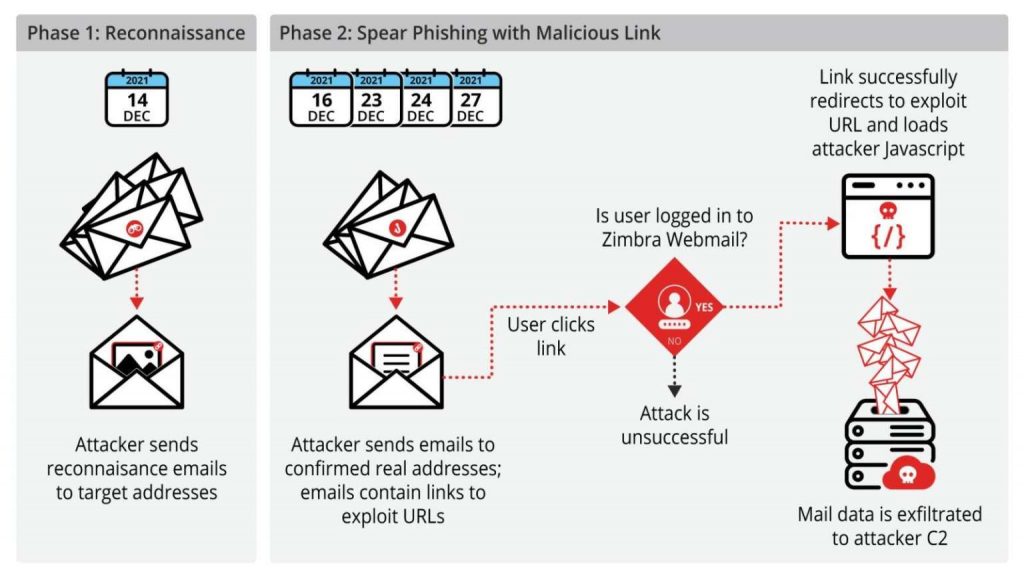
The attacks were discovered in mid-December, and although Volexity notified the Zimbra developers about the bug as early as December 16, the company has not yet released a patch.
The attacks were divided into two stages. Initially, the hackers sent a harmless email to victims to determine if the right accounts were active and whether users would open suspicious emails from unknown individuals.
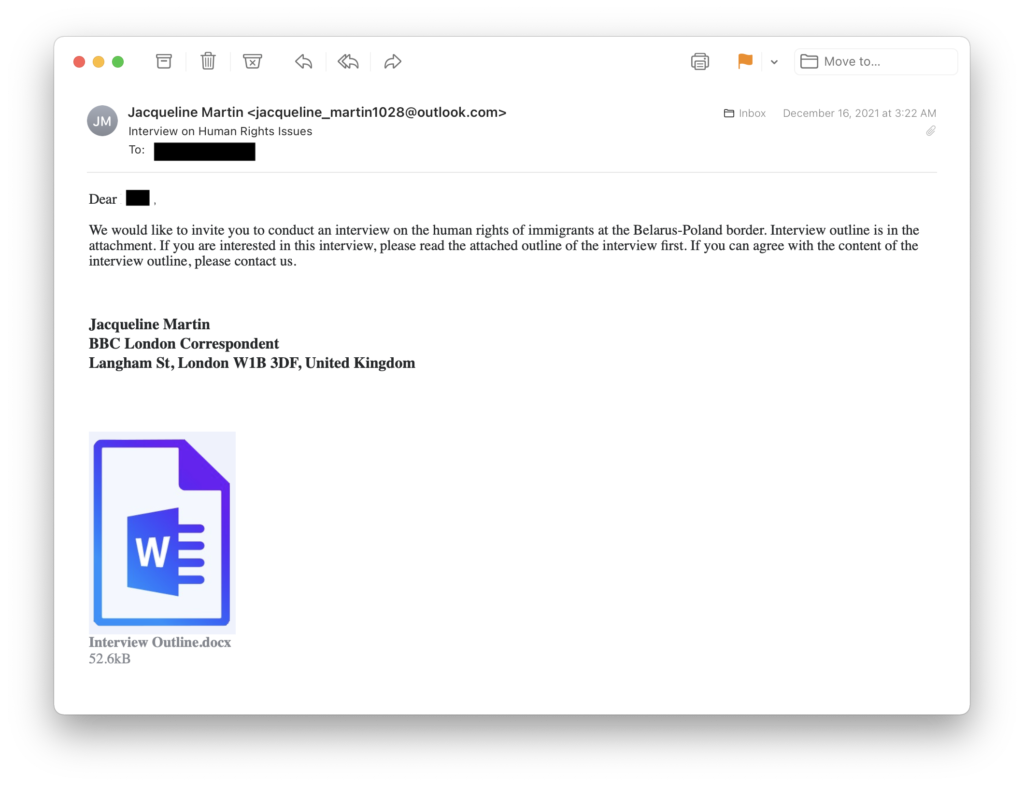
The actual attack only happened with a second email, in which the hackers included a link. If the user accessed this URL, they were taken to a hacker site where malicious JavaScript code performed an XSS attack on Zimbra webmail at the victim’s organization.
The vulnerability works against Zimbra webmail clients versions 8.8.15 P29 and P30 and allows stealштп Zimbra session cookies. These files allow hackers to connect to someone else’s Zimbra account, from where they gain access to email (they can view emails in victims’ mailboxes and steal their contents), after which they send additional phishing messages to the user’s contacts, and also offer targets to download malware.
While there are currently over 33,000 Zimbra servers on the web, Volexity says 0-day is thankfully safe for Zimbra 9.x (the most recent version of the platform).
Based on the attacker infrastructure used in these attacks, experts were unable to link what was happening to any previously known hack group. As a result, the grouping was given the name TEMP_Heretic. At the same time, experts report that “the attacker is probably of Chinese origin.”
Let me remind you that we reported that Chinese hackers attacked US organizations and exploit bugs in F5, Citrix and Microsoft Exchange and also that Hackers attacked Microsoft Exchange servers of the European Banking Authority.




