Microsoft engineers have published a security bulletin on a new vulnerability affecting Surface Pro 3 tablets. The bug could be used by an attacker to inject malicious devices into corporate networks and bypass the Device Health Attestation.
Other Surface devices, including Surface Pro 4 and Surface Book, are not considered affected by this issue. Although the Surface Pro 3 was released in June 2014 and discontinued in November 2016, the manufacturer claims that third-party machines using a similar BIOS may also be vulnerable.
Fortunately, an attacker would need either access to the device owner’s credentials or physical access to the tablet to successfully exploit the new bug.
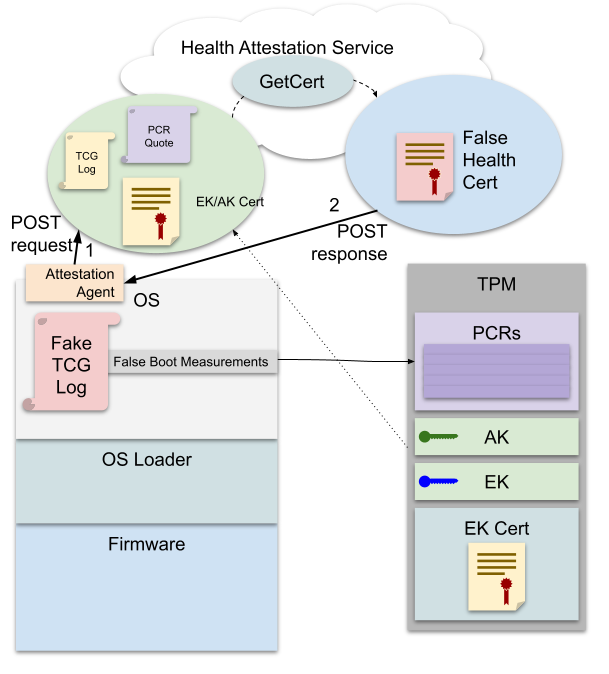
The problem is identified as CVE-2021-42299 (5.6 CVSS) and Google Software Engineer Chris Fenner who discovered the bug, gave a bug name TPM Carte Blanche.
Device Health Attestation is a cloud-based and on-premises service that checks TPM and PCR logs and informs Mobile Device Management (MDM) whether Secure Boot, BitLocker, Early Launch Antimalware (ELAM) protection is enabled, Trusted Boot signed correctly, and so on.
Thanks to CVE-2021-42299, an attacker can tweak the TPM and PCR logs to obtain false attestation, which will ultimately disrupt the entire Device Health Attestation validation process.
A Google expert has already released a PoC exploit demonstrating how this vulnerability can be exploited.
Let me remind you that we also said that Microsoft warned of a critical vulnerability in Cosmos DB.