Reuters reports that the recent shutdown of the REvil hack group was due to hack of hacker’s sites by law enforcement agencies.
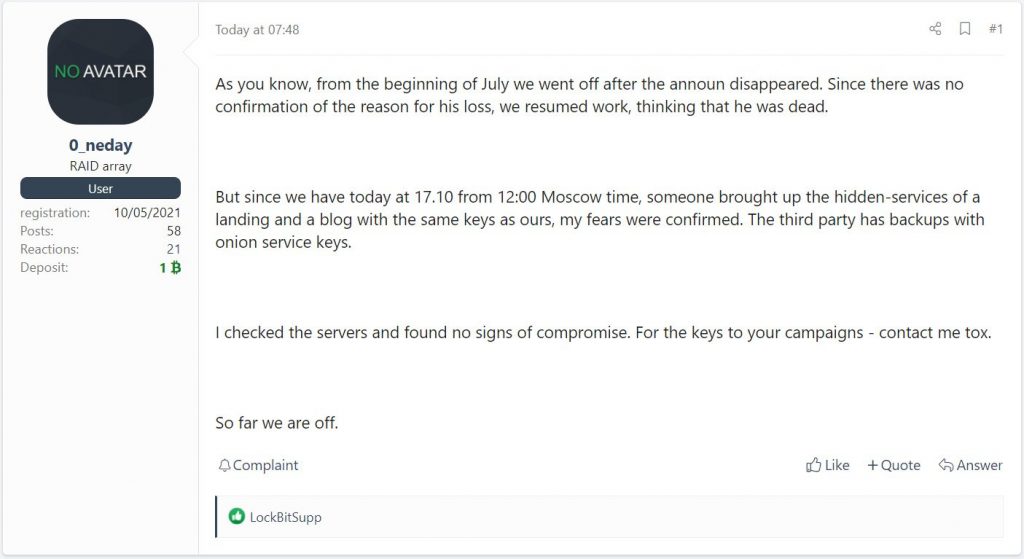
Let me remind you that earlier this week the operations of the ransomware REvil were again suspended, as an unknown person hacked the group’s website, through which hackers accepted payments from victims and “leaked” data stolen from companies. A REvil spokesman known as 0_neday posted a message on the XSS hacker forum that someone had hijacked the attacker’s domains.
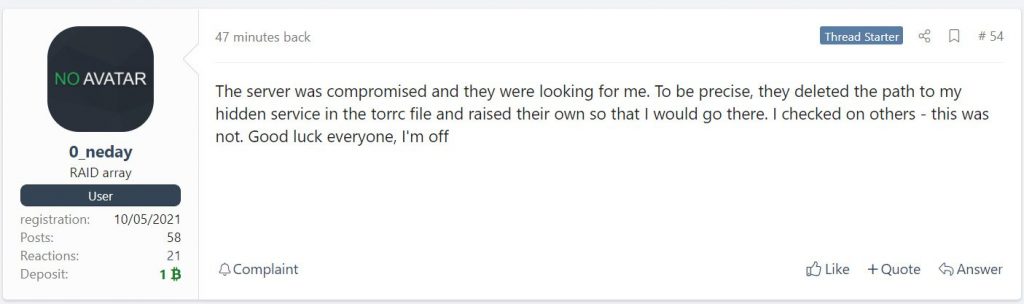
It was also reported that an unknown person hijacked the hacker’s onion domains using the same private keys as the REvil sites. At the same time, the unknown person seemed to have access to the backup copies of the hack group’s websites, and 0_neday stated that the grouping server had been compromised, and the unknown attacker was targeting REvil.
Now, Reuters’ own sources (three cybersecurity experts from the private sector and a former official) say that the group’s infrastructure was turned off as a result of a law enforcement operation carried out in several countries around the world. In particular, a person familiar with the events told the news agency that a foreign partner of the US government had carried out a hacking operation to infiltrate REvil’s infrastructure. A former US official who spoke to reporters on condition of anonymity said the operation is still ongoing.
The head of cybersecurity strategy at VMWare, Tom Kellerman, who is also a cybercrime advisor to the US Secret Service, told the media the following:
Many believe that this time REvil has ceased its work completely. The fact is that recently the ransomware has already “disappeared from the radar” after scandalous attacks on clients of the well-known MSP solutions provider Kaseya and JBS, the world’s largest supplier of beef and poultry, as well as the second largest pork producer.
Although REvil eventually returned a few months later, some cybercriminals and information security experts believed that the FBI or other law enforcement agencies had gained access to the group’s servers and controlled them since the restart. After all, while REvil was inactive, Kaseya somehow obtained a universal key to decrypt its customers’ data. Then, many believed that Russian law enforcement officers received the decryption key from the attackers themselves and handed it over to the FBI as a gesture of goodwill.
In addition, in the past, a member of the group known as Unknown or UNKN has posted advertisements or the latest news about REvil operations on hacker forums. After restarting the operations of the ransomware, he disappeared, and the hackers themselves wrote that Unknown was probably arrested. What happened to him is still not known for certain.