
HiddenTear Open-Source
Nowadays, more and more programs turn their development into open-source form. Some applications created in such a way are even better than their proprietary counterparts. Ransomware developers decided that this opportunity cannot be missed - and began using the open-source ransomware with the name HiddenTear. Created “for educational purposes” in 2015 by Turkish cybersecurity researcher Utku Sen, it was soon applied by real cybercriminals for money extortion. Is it better than its “closed” counterparts? Let’s take a look and figure it out.
How can open-source be better than proprietary?
The closed development of a program is still a standard and single possible way for the majority of companies. When you have some unique technology applied, the worst step is to allow everyone to see its internal details. In such a case, there is no problem to copy someone's valuable technology and then publish it as your own development. However, in the cases when a certain application or other software element must be fixed, and you have no idea how, it is better to offer the community to do it.
The encyclopedic example of such a case is the AMD video driver for the Linux platform. While it was closed for external users, its compatibility with Linux was pretty poor. The performance of AMD GPUs on Linux was much lower than on the same PC on Windows; users also complained of numerous errors during the trivial operations. In one moment, AMD decided to publish the source code of their video driver for Linux - and voila, in less than several months the problems with performance as well as the majority of critical bugs were fixed.
However, there is a thing that makes open source software development problematic for the corporations. It is quite hard to commercialize an open-source project. When everyone can access the source code, it is problematic to force someone to pay for your program. Sure, there are a lot of companies that are currently operating with the software-as-a-service model (SaaS), but their financial success is not as great as in the companies which develop proprietary software or even spread their "closed" apps through the SaaS model.
In the malware world, things are a bit different. No coders wish to risk for low payment, while threat actors constantly seek to increase their margin, i.e. paying less for malware and infrastructure. And here is where open-source projects started for cybersecurity studying purposes hove into view. HiddenTear is just another example of such malware – there are RATs and backdoors with the same story.
How is HiddenTear going?
The open-source nature of this ransomware means not only a big potential at fixing and development, but also gives the malware an enormous modification potential. Exactly, some other examples of ransomware have their own builders - IDE-like applications that makes the process of ransomware modification easier. But there, when any crook is able to interact with the whole code, it is expectedly to have a lot of completely different, at the first sight, viruses, which in fact belong to the same group - HiddenTear.
The ability to make changes to the whole codebase makes each distributor not just a part of the malware chain, but a full-sized developer. Such dividing makes the group almost immortal: while groups that use RaaS modify the ransomware with builders, or receive the new variants from the exact creators, HiddenTear distributors are free to make “the virus of their dream”. Chained distributors develop similar things, so the behavior of ransomware can easily be predicted. Meanwhile, it is pretty difficult to find anything in common in HiddenTear versions.
What is under the hood?
First appearing in 2016, HiddenTear ransomware keeps going even in 2021. Along with Xorist, this group is one of the most long-living in the ransomware world. Some of the modern ransomware groups shutting down their activity in one year, or even after 5-7 month, but these two are still rolling - after 5 years of successful money extortion. Such a long story is likely provided by the feature described above - the ability to be changed by literally everyone makes the ransomware almost impossible to stop.
Unique examples: HiddenTear screenlockers
At the first sight, Widia Screenlocker has no relation to HiddenTear group in particular and to ransomware world at all. However, the majority of factors that are uncovered only after checking the source code of that virus says clearly about its relations with HiddenTear ransomware group. It used the parts of HiddenTear code, but had the classic ransomware functions removed. Instead, the group who have developed it added the screen locking functions - with the scary banner at the end of the action.
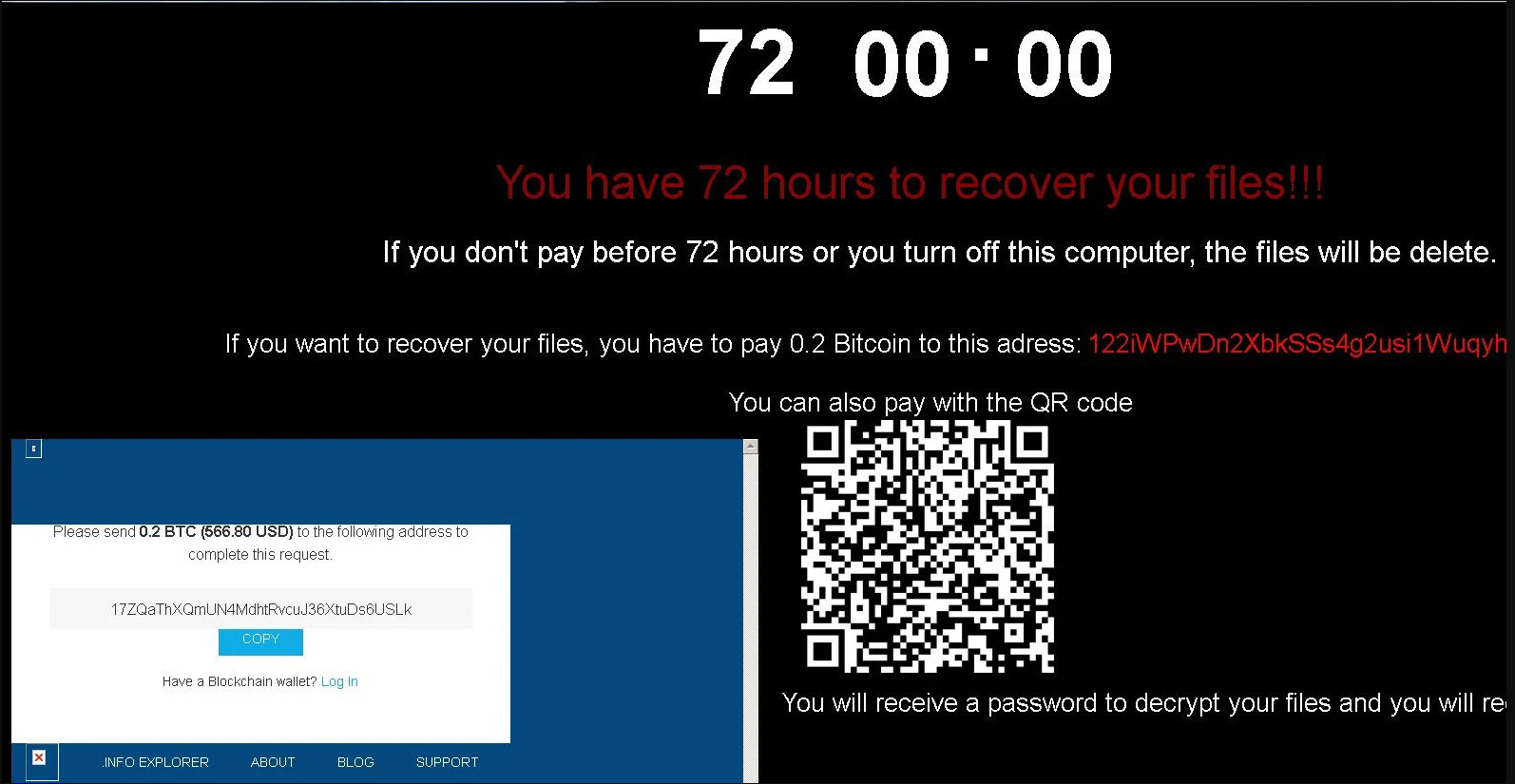
Such viruses were designed as a typical screenlocker, which had been widespread in 2008-2014 and squeezed out of the malware market by ransomware. However, examples like FBI Lock or Widia Screenlocker still appear. Moreover - Widia is not a single example of a locker based on HiddenTear code: BlueHowl ransomware appeared slightly earlier and had almost the same functionality. It was also a screenlocker, but with a typical ransom payment way - in Bitcoins. Widia used an uncommon payment method - transfer to a bank card, which is pretty easy to track, compared to Bitcoin transfers.
How do screenlockers work?
Screenlockers, also known as winlockers/maclockers (depending on the operating system they are created for), are the viruses which block the desktop and extort money from their victims. During their main era, in 2008-2014, they generally asked to top-up the phone number or to send money to the payment system account, like Qiwi or PayPal.Nowadays, these viruses extort the ransom sum in Bitcoins, just like their successors - ransomware.
Screenlocker ability to lock the desktop is related to registry modifications. It specifies the wrong way to system files for certain keys. For example, explorer.exe (the process that handles the interaction between user and OS) became substituted with a similarly-named process, which is related to the virus. Each time when Windows tries to run the explorer.exe, it runs malware instead. That’s why you will see the scary banner even in Safe Mode.
Some of the screenlocker variations are able to infect the BIOS. Such a hazardous situation is possible when the virus is granted with driver-level access to the operating system. In that case, you cannot even access the OS - the scary banner will appear almost immediately after pressing the power button.
Technical details about HiddenTear ransomware
HiddenTear ransomware can logically be divided on 2 variants – v1.0 and v2.0. First version was, exactly, the original ransomware sample published by Utku Sen. Since that sample was created for educational purposes, is it pretty obvious that it was much softer than a regular ransomware. The original version aimed only at the C:/Program Files/Internet Explorer folder, and a lot of early variants of HiddenTear started their encryption from this folder. Moreover, it has a lot of encryption flaw (which are done intendedly by its developer) that moved in all HiddenTear variants.
The last feature is interesting enough to be revised more precisely. Almost all ransomware uses the RNGCryptoServiceProvider – a secure random number generator. Meanwhile, the basic variant of HiddenTear along with the early versions of its malicious copies used the Random class. That class creates the predictable sequence of numbers that decreases the strength of any cipher used by the variants.
Another vulnerability in the encryption mechanism is related to the Rfc2898DeriveBytes class. That function returns the unsecure sequence of bytes, but supposes the use of randomized salt value and same randomized number of iterations. In fact, Utku Sen (the developer) set the fixed number of iterations and salt values, making the key cryptographically unsecure.
This ransomware dictates the AES algorithm the fixed list of bytes, graphic symbols and letters that can be used for the encryption, while normally ransomware uses each byte it can encrypt. Hence, the decryption key may look like a strange mix – for example, ☻gTYAHF◘ca♫gewoyAFU¶aA.
The final thing that makes the decryption key extremely easy to receive is the fact that the key is sent to the servers as a plain text file, without any encryption or obfuscation. Things like ransomware use asymmetric ciphering for the key it sends, that makes it impossible to intercept the key. If you have a network sniffer, it is very easy to get the key by checking the sniffer logs.
Once again – all of the security flaws mentioned above are about all variants of HiddenTear. They are embedded too deep into the malware code, so it is possible only to correct some of them (like the key sent as a .txt file), but not to fix them all.
Here are all version of HiddenTear ransomware that can be decrypted with a special decryption tool:
| TearDr0p | Bansomqare Wanna | Random6 2 | Rootabx | Executioner3 | WhiteRose2 |
| Sorry | Symbiom | TheZone | Shrug | Blank | MTC |
| Executioner | VideoBelle | Data_Locker | dotRansom | MoonCrypter | Nobug |
| tlar | J-Ransomware | Lime-HT | Poolezoor | ZenCrypt | Horros |
| Diamond | MireWare | FlatChestWare | ShutUpAndDance | Random6 | Karmen |
| Gendarmerie | PGPSnippet | J-Want-To-Cry | 8lock8 | Matroska | AnonCrack |
| Paul | Pransomware | RansomMine | BloodJaws | Zorro | onion3cry |
| Kraken 2.0 | Explerer | Assembly Balbaz | TotalWipeOut | CryptoKill | Saramat |
| ZeroRansom | Zenis | Technicy | Luv | Domino | CryptConsole2 |
| The Brotherhood | OpsVenezuela | Randion | Zalupaid | Qwerty | PayOrDie |
| CerberTear | Pedo | Kratos | Donut | CyberResearcher | LanRan |
| Executioner2 | JobCrypter | Boris | Jodis | TQV | Predator |
| WhiteRose | Lime | Ton | Frog Fuck_You |
Almost 80 different variants of HiddenTear ransomware of the list you can see above is far from displaying all variants. A lot of versions keep being unavailable for decryption, because their developers fixed the aforementioned vulnerabilities. Another reason for absence in this list is that analysts could just miss some because of their low spreadness.
The majority of the examples from the list above use AES-256 encryption. This cipher supposes that there are 2^256 decryption keys (78-digit number). It is likely impossible to decrypt it with brute force, if it is generated without the flaws that are typical for HiddenTear. There are two ways of getting the decryption key - by paying the ransom or by examining the files ransomware drops during the execution. If you are lucky, and ransomware fails to connect to the command server, your files will be encrypted with an offline key. The key can be found somehow in the aforementioned temporary files that are used by this virus during the encryption. It has the same AES algorithm, but the number of keys is limited. Hence, there is a chance that another victim will have a key in common with you.
However, some examples use more complicated encryption algos, and their encryption is almost impossible. For example, May ransomware, a HiddenTear variant that appeared in early 2017, uses AES-256+RSA-4096 encryption. The amount of possible keys for this thing is so big that even quantum computers of our future will find it difficult to decrypt it in the appropriate time period.
