Experts have discovered a third Server Side Request Forgery (SSRF) vulnerability in Ivanti products. This is a serious security issue for corporate VPN devices. The new vulnerability allows unauthorized access to restricted resources that were available only after authentication.
Ivanti SSRF Vulnerability Exploited
Ivanti, a renowned corporate VPN appliance provider, has issued a warning regarding a new zero-day vulnerability under active exploitation. This announcement comes in the wake of two previously disclosed vulnerabilities, CVE-2023-46805 and CVE-2024-21887. These two have already been targeted by Chinese state-backed hackers since early December 2023. The latest vulnerability, identified as CVE-2024-21893, is a server-side issue allowing unauthorized access to restricted resources, and it looks like adversaries take advantage of it as well.
Shadowserver reported over 22,000 instances of Connect Secure and Policy Secure. To authenticate an Ivanti VPN, the doAuthCheck function in an HTTP web server binary located at /root/home/bin/web is used. It is important to note that the endpoint /dana-ws/saml20.ws does not require authentication.
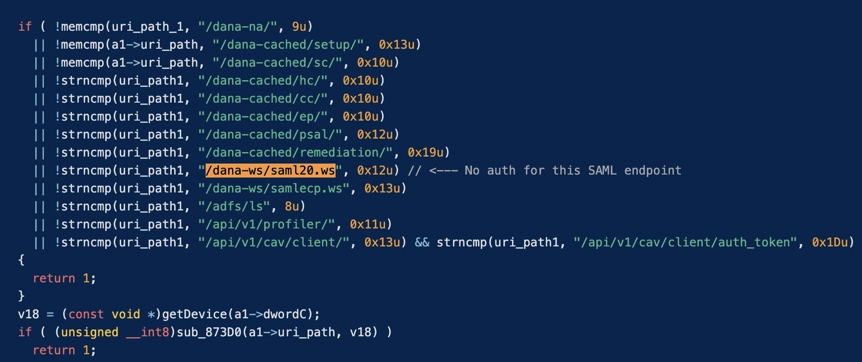
The flow CVE-2024-21893 involves server-side request forgery in the SAML component of Ivanti’s products, compromising authentication protocols. These vulnerabilities affect Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti Neurons for ZTA, with an estimated 1,700 devices already compromised worldwide, spanning various industries including aerospace, banking, defense, government, and telecommunications.
Impact of Ivanti VPN SSRF Vulnerability
VPN devices are highly attractive to cyber attackers who aim to penetrate deeply into organizational networks. These devices facilitate secure remote access for employees by encrypting their connections to company resources. Positioned at the network’s periphery, they handle incoming connections from any external device with the right settings. Once a hacker gains initial access through a VPN, they can maneuver to access more critical and sensitive areas within the network infrastructure.
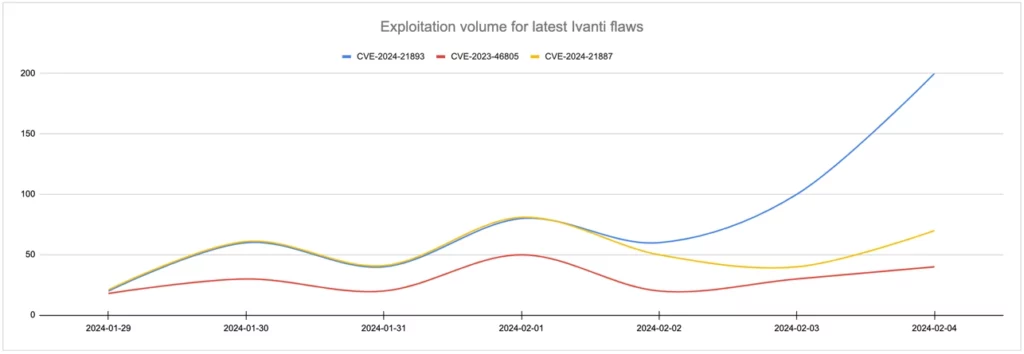
The situation was exacerbated by Ivanti’s delayed response in patching the vulnerabilities, missing their own set deadline by a week. This delay left organizations vulnerable for a longer period, challenging security professionals to mitigate the risks amid the ongoing attacks. Furthermore, the attackers’ ability to bypass Ivanti’s initially provided mitigations for the first two vulnerabilities added to the difficulties faced by security teams.
CISA Calls to Disable Ivanti VPN
CISA issued Emergency Directive 24-01, requiring Federal Civilian Executive Branch agencies to take immediate action to this zero-day vulnerability. These measures include implementing mitigations, reporting any signs of compromise, removing affected products from networks, applying Ivanti’s updates within 48 hours of release, and providing a detailed report of actions taken to CISA.
Additionally, CISA’s guidance includes performing a factory reset and rebuilding of the Ivanti appliances before bringing them back online, underscoring the need for a clean slate to ensure the devices are free from compromise.
All this looks like an ideal storm around Ivanti. It will be rather challenging to clean up the reputation of their software solution after all this mess. Vulnerabilities happen in any software, though this much of them in one software solution, in a short period of time, and lacking proper response from the vendor – that’s a proper nightmare.





