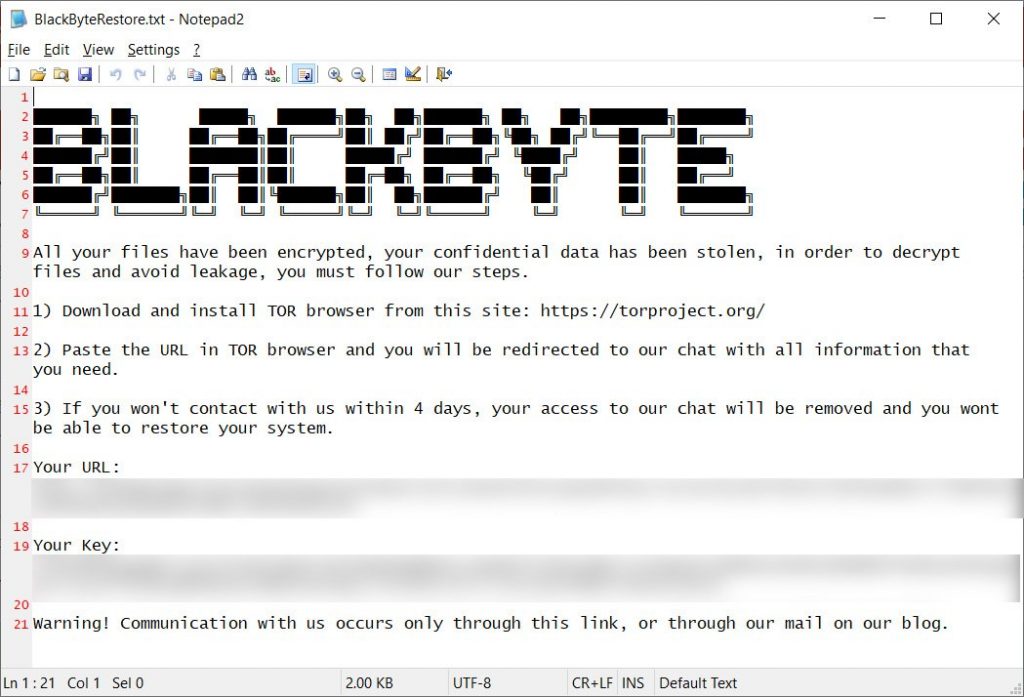
Experts from Trustwave have released a free decryptor utility for victims of the BlackByte ransomware that they can use to recover damaged files. The decryptor already available on GitHub works thanks to the exploitation of a bug in the ransomware code.
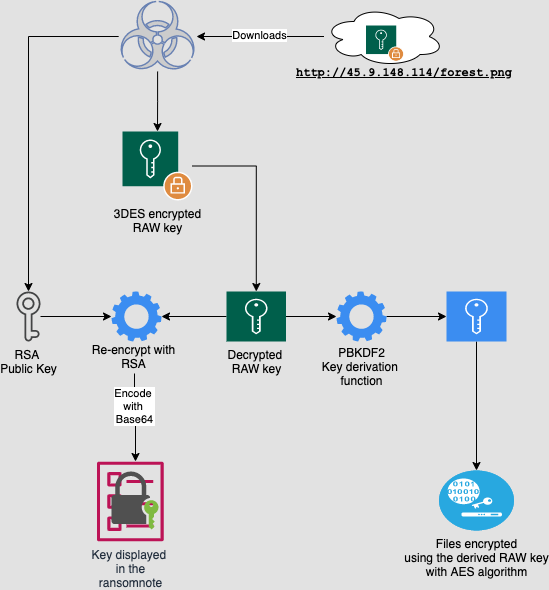
The researchers published a detailed technical analysis of the malware in two parts, in which they say that the BlackByte encryption procedure begins with the fact that hackers download a fake forest.png image file to the victim’s machine.
In fact, this file contains a cryptographic key that the malware uses to obtain encryption keys for the victim’s files, and then generates an access key that will give the victim access to a darknet site through which hackers negotiate and receive ransoms. The researchers write that this process can be called quite simple compared to other ransomware.
The decryptor provided by Trustwave automates the process of reading the key from the forest.png file and then calculates the decryption key needed to restore the victim’s files. The forest.png file is already included in the decoder, and victims are advised to replace it with a file from their own systems.
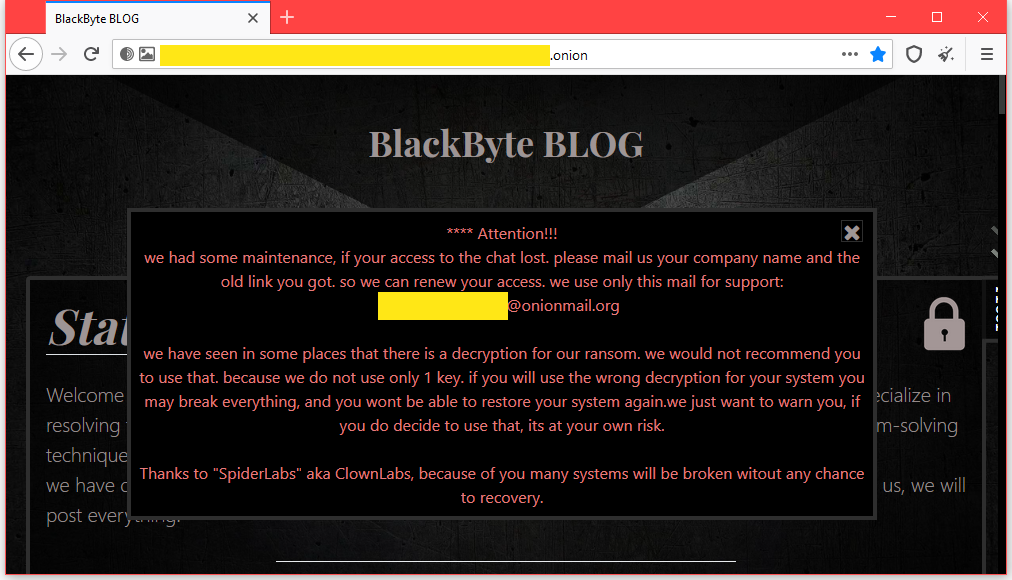
Interestingly, the BlackByte developers did not like the release of the decoder. Earlier this week, the hack group published a message on its website and tried to scare away the victims of the use of the decryptor. The hackers claim that they have used more than one key and that using the tool with the wrong key (forest.png file) may cause irreparable damage to the victims’ files. Attackers call Trustwave SpiderLabs experts “clowns”.
The BlackByte ransomware appeared in the summer of 2021, and reports of the first attacks began to arrive from users at the end of September.
The ransomware written in C# tries to terminate numerous security processes on the infected machine, as well as mail server and database processes, in order to successfully encrypt the device. The ransomware also tries to disable Microsoft Defender on target devices before attempting encryption.
On the group’s darknet site, where hackers list their victims who refused to pay the ransom, only eight entries have been posted so far.
Let me remind you that we also reported that Cybersecurity specialists released a free decryptor for Lorenz ransomware, as well as that Added utility for decrypting data after REvil attacks.