Cybersecurity researchers have discovered a new family of ransomware called 3AM. Attackers attempted to use it as an alternative attack method during the failed LockBit deployment.
3AM Ransomware – The Fallback Variant of LockBit
According to a recent report, cybersecurity experts have discovered a new type of ransomware known as 3AM. Since this ransomware has not been used before and its use is still limited, experts agree that this is a relatively new malware. The attackers used 3AM as a backup to LockBit, as the attempt to infect a LockBit victim was blocked. By the way, although the attacker installed the ransomware on three machines on the organization’s network, it was blocked on two.
What is LockBit Ransomware?
In a nutshell, LockBit is a type of ransomware that was first seen in September 2021. It is a modular ransomware, meaning attackers can customize it with different components. It makes it a versatile and powerful tool to target many victims. LockBit encrypts files on the victim’s computer and then demands a ransom payment to get the files back. The ransom amount is typically $1 million or more, based on the victim.
In addition to requiring payment, LockBit threatens to sell the victim’s data on the Dark web if the ransom is unpaid. LockBit has been used to attack various organizations, including healthcare providers, government agencies, and businesses, causing significant disruptions in some cases. In fact, is it one of predominant ransomware gangs active in 2023. After the Conti shutdown, it quickly gained the vacated market share, and became #1 threat for companies.
3AM Ransomware Overview
3AM is written in Rust, and once infected, it tries to stop several services on the infected computer before it starts encrypting. The attackers also use Cobalt Strike to try to escalate privileges and then number other servers for further horizontal movement. The attackers also created a new user to save and transfer the victim’s files to their FTP server.
The program then scans the entire disk, encrypts files matching the pre-defined criteria, and deletes the original files. Ultimately, the encrypted files have the extension *.threeamtime. In addition, the malware attempts to delete shadow copies of volumes. In each folder with encrypted files, the program leaves a text file called “RECOVER-FILES.txt,” a ransom note.
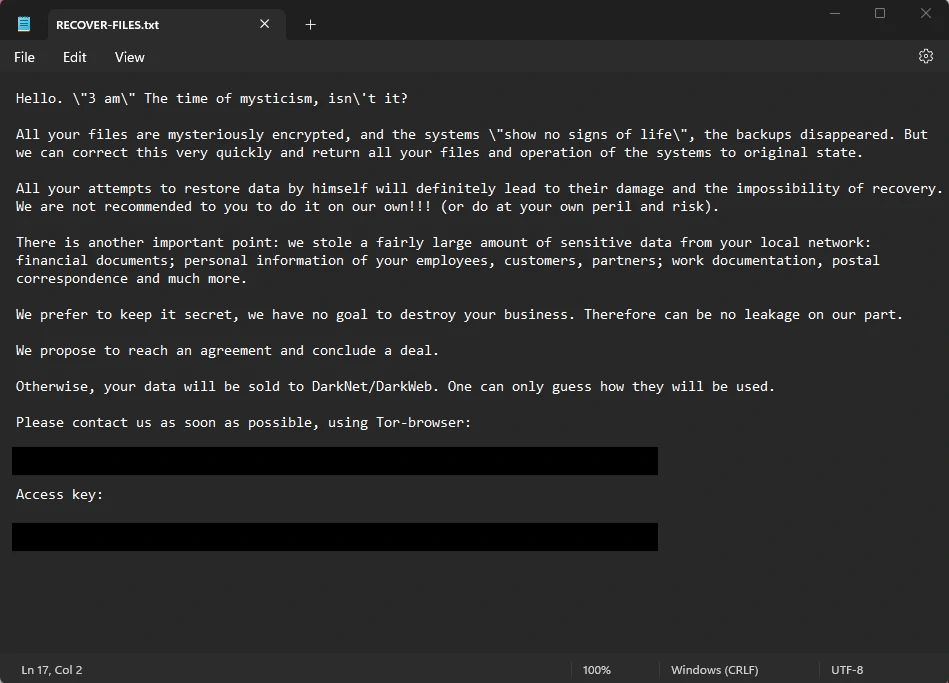
Although the emergence of new families of ransomware programs is frequent, most of them never gain significant popularity, and some disappear just as quickly. However, since 3AM was used by a LockBit affiliate as an alternative, experts suggest that it may be of interest to attackers and could be seen again in the future.
How to protect against ransomware?
Ransomware is a severe threat to companies of all sizes. Unfortunately, there is no ultimate protection against it. However, there are preventative measures organizations can take to mitigate the risk:
- Keep your software up to date. Software updates include essential security patches that protect against ransomware attacks. Most software programs have an option for automatic updates. This will ensure your software is always updated with the latest security patches.
- Back up your data regularly. The best way to protect data` is an offline backup of data stored on hard disks. An offline backup is a backup located on a device not connected to your computer or network. This means the ransomware cannot encrypt the backup files, so you can restore them without paying the ransom.
- Cloud-based backup solutions will be superior to classic ones. This method can also protect data from encryption as an alternative to the traditional way of storing data backups. It also makes it easier to restore your data if it is encrypted by ransomware.
- Educate your employees. It’s no secret that the weakest link in the line of defense is the human factor. Educating employees on the basics of cyber hygiene and conducting hands-on training to identify red flags is critical. For example, you can show them examples of phishing emails and ask them to determine what is wrong with them.
- Use a managed security service provider. An MSSP can help you to implement and maintain security measures to protect your company from ransomware attacks. In addition, you can free up your internal IT staff to focus on their tasks and be confident that experts are handling your security.
In addition to the above, there are some universal recommendations to help prevent a ransomware infection. These include using strong passwords, multi-factor authentication, and a firewall.