Recent research uncovers a significant portion of SonicWall firewall instances being susceptible to attacks. In particular, two vulnerabilities are able to cause remote code execution (RCE) and DoS attacks. Unfortunately, no official patches are available at the moment, forcing clients to seek a workaround.
Uncovering the Flaws
The vulnerabilities in question are primarily two stack-based buffer overflow issues identified as CVE-2022-22274 and CVE-2023-0656. These vulnerabilities were discovered in SonicWall’s series 6 and 7 next-generation firewall (NGFW) devices. The first was disclosed in March 2022, while the latter came to light a year later, in March 2023. The critical nature of these vulnerabilities, especially CVE-2022-22274 with a CVSS score of 9.4, cannot be understated.
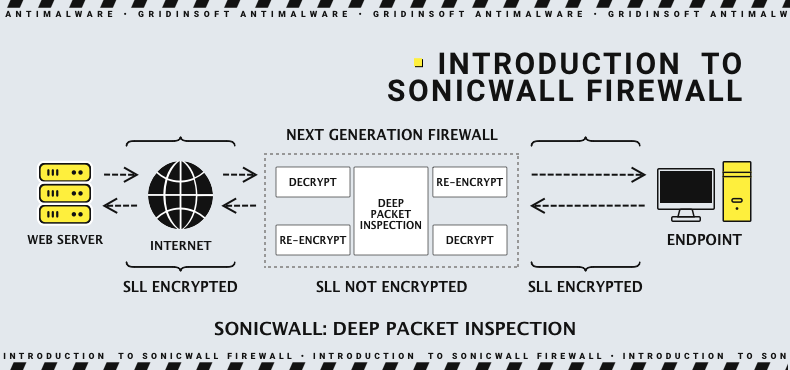
In both cases, the vulnerabilities arise due to inadequate input validation for HTTP requests received by the firewall. This lack of validation allows attackers to send malicious requests that the firewall is not equipped to handle, leading to buffer overflow. Also, the exploitation of these vulnerabilities requires the management interfaces of the SonicWall devices to be exposed to the internet. This exposure increases the risk of attacks as it allows remote, unauthenticated attackers to target the vulnerabilities.
Bishop Fox, a cybersecurity firm, recently scanned SonicWall devices with internet-facing control interfaces. Out of 233,984 devices, 178,637 (76%) were susceptible to at least one vulnerability, and 146,087 devices (62%) were vulnerable to both bugs. Moreover, these 146,087 devices are susceptible to a vulnerability that was publicly disclosed almost two years ago.
Vulnerability consequences
The exposure of such a significant number of firewalls to potential attacks is alarming, particularly given SonicWall’s customer base, which spans over 500,000 businesses across more than 215 countries. Also, the vulnerabilities identified in over 178,000 SonicWall firewalls can have several severe consequences:
| Devices Vulnerable To: | Count | Percent of Total |
| CVE-2022-22274 | 146,116 | 62% |
| CVE-2023-0656 | 178,608 | 76% |
| Both CVEs | 146,087 | 62% |
| At least one CVE | 178,637 | 76% |
Denial of Service (DoS) Attacks
The main threat posed by these vulnerabilities is the ability for attackers to carry out DoS attacks. This can lead to the affected firewalls becoming unresponsive or crashing, thereby disrupting the network services they protect. In a DoS scenario, critical network functions could be halted, impacting business operations, communication, and access to essential digital resources.
Remote Code Execution (RCE) Risks
Although the primary concern is DoS attacks, there’s also a potential for remote code execution. If exploited, this could allow attackers to run arbitrary malicious code on the affected device. This scenario is particularly alarming because it could enable attackers to gain unauthorized access to network resources, manipulate data, or establish a foothold for further attacks within the network.
Immediate Response and Mitigation
In response to these findings, urgent measures are recommended. Users of SonicWall NGFW are advised to immediately remove the device’s web management interface from public access and to update the firewall’s firmware to the latest version. A test script has been developed to determine the vulnerability of a device to these flaws without causing a crash. We also recommend the following tips:
- Review and update firewall rules and security policies regularly. Ensure that only necessary ports and services are open and accessible.
- Utilize intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor network traffic for suspicious activities and block malicious traffic.
- Conduct regular security audits and vulnerability assessments of network devices.
- Implement network segmentation to limit the spread of an attack within the network.
- If necessary, consult cybersecurity experts for advice on protecting your network and to ensure that all mitigation strategies are effectively implemented.





