The day after the release of the fix for one of the most dangerous vulnerabilities in the history of Windows, security researcher Saleem Rashid demonstrated how it can be used to present a malicious site as any site on the Internet in terms of cryptography.
The talk is about the vulnerability CVE-2020-0601 in the cryptographic library crypt32.dll in Windows. The root cause of this vulnerability is a flawed implementation of the Elliptic Curve Cryptography (ECC) within Microsoft’s code.
According to both the NSA, the DHS, and Microsoft, if this bug (tracked as CVE-2020-0601) is exploited, it can allow an attacker to:
- launch MitM (man-in-the-middle) attacks and intercept and fake HTTPS connections
- fake signatures for files and emails
- fake signed-executable code launched inside Windows
Experts from the US National Security Agency discovered the problem and reported Microsoft about it.
“US authorities reacted to the vulnerability very openly and proactively. The NSA released a rare security alert about the bug, and the DHS’ CISA department issued an emergency directive, giving government agencies ten days to patch systems by applying the January 2020 Microsoft Patch Tuesday updates”, — writes ZDNet.
On Wednesday, January 15, Saleem Rashid posted a screenshot on Twitter showing how the music video of Never Gonna Give You Up by popular singer of the 1980s, Rick Astley, plays on Github.com and NSA.gov. Using the vulnerability, the researcher was able to spoof Github and the NSA sites in Edge and Chrome browsers.
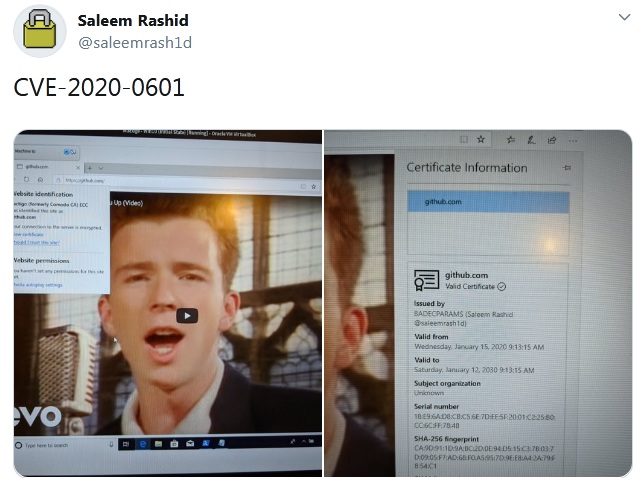
Created by Rashid exploit consists of 100 lines of code, but it can be easily compressed to 10 lines if you trim “a few useful features”, the researcher told Ars Technica.
Although exploiting the vulnerability is not so simple, and to carry out an attack, must be met a number of conditions, the NSA called it highly dangerous, and PoC attack presented by Rashid explains why.
According to a security notice published by the agency, an experienced hacker can “very quickly” figure out how to exploit it.
The NSA first reported an error at Microsoft. It is believed that in this way the NSA is trying to improve its image in the cybersecurity community after the disasters of EternalBlue and Shadow Brokers, when hackering tools developed by the NSA leaked to the Internet and were used for serious cyberattacks.
By the way, many well-known information security experts tend to agree with the opinion of colleagues from the NSA.
“This is what Salim just demonstrated: using a [short] script, you can create a certificate for any site, and it will be trusted in IE and Edge with standard Windows settings. This is terrible. The problem affects VPN gateways, VoIP, almost everything that uses network communications”, — said Kenn White, head of security at MongoDB.
Security experts and cryptographers like Thomas Ptacek and Kenneth White have confirmed the vulnerability’s severity and wide impact — although it does not impact the Windows Update mechanism, which would have allowed a threat actor to fake Windows updates.
The danger is real for all versions of Windows, and even if for many years you resist changes, upgrade your Windows 7. Microsoft engineers have released a farewell patch for the system – this is your last chance to survive with the “seven” for some more time in the cruel world of cybethreats 2020.
However, GridinSoft products still protect you. Anyway, the system is worth updating )




