Secureworks experts have found that Chinese hackers from two groups that specialize in espionage and theft of intellectual property from Japanese and Western companies use ransomware to hide their actions.
Let me remind you that we also wrote that Chinese Hacker Group Revealed after a Decade of Undetected Espionage, and also that Chinese Hackers Attack 0-day Follina Vulnerability.
Analysts write that the use of ransomware in spying campaigns allows hiding traces, complicate the attribution of attacks and distracts the attention of IT specialists of the victim company. In addition, in this way the theft of confidential information is disguised as financially motivated attacks.
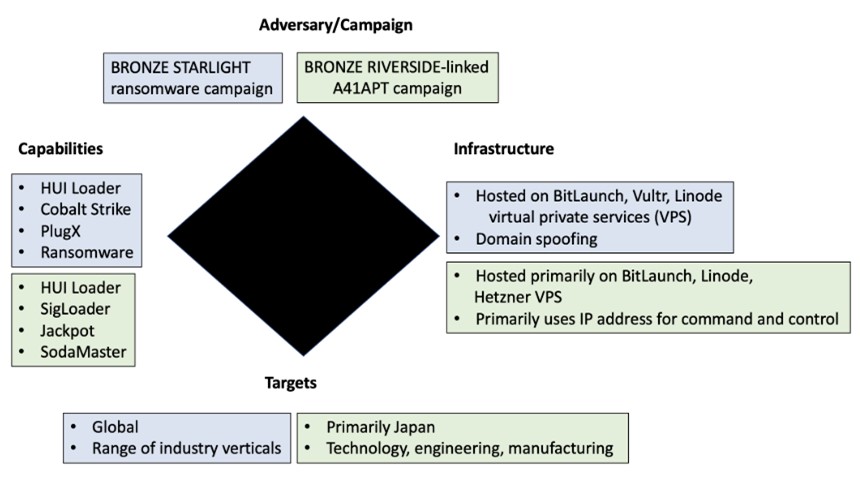
A similar disguising method is practiced by Bronze Riverside (APT41) and Bronze Starlight (APT10). Both use the HUI loader to deploy remote access Trojans, PlugX, Cobalt Strike, and QuasarRAT.
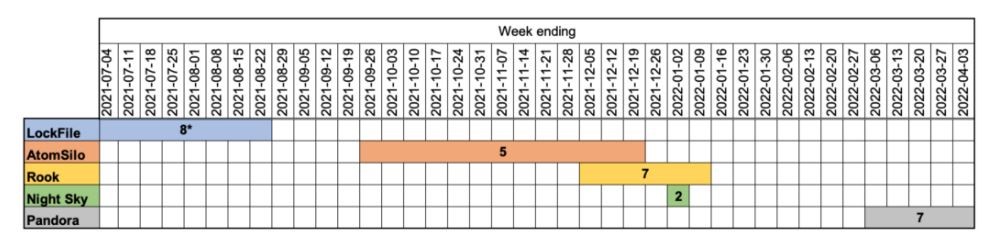
Starting in March 2022, the Bronze Starlight group used Cobalt Strike to deploy ransomware (including LockFile, AtomSilo, Rook, Night Sky, and Pandora) on their victims’ networks, according to researchers. These attacks also used a new version of the HUI loader, which is able to intercept Windows API calls and disable Event Tracing for Windows (ETW) and Antimalware Scan Interface (AMSI).
Studying the configuration of Cobalt Strike beacons in three different attacks using AtomSilo, Night Sky, and Pandora malware revealed a common control server address for them. It is also noted that this year the same source was used to upload samples of the HUI bootloader on Virus Total.
It is noted that in the studied cases, the activity of LockFile, AtomSilo, Rook, Night Sky and Pandora was unusual when compared with ordinary financially motivated ransomware attacks. So, the attacks were aimed at a small number of victims, lasted a short period of time, and then the hackers completely abandoned the project and moved on to the next one.
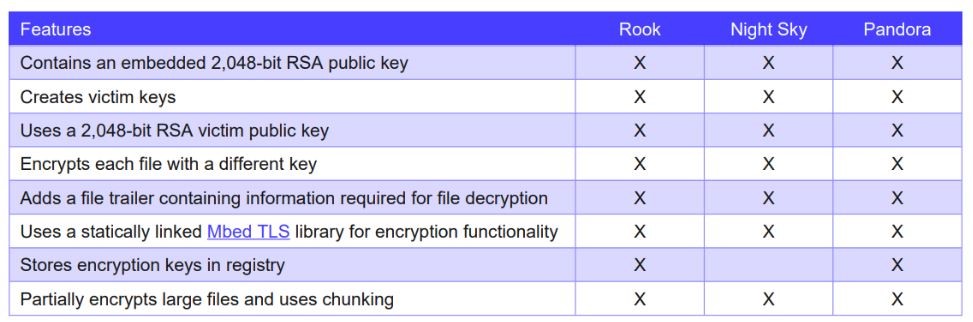
Secureworks writes that Pandora and the latest version of the HUI loader have code similarities. LockFile and AtomSilo also look similar, while Night Sky, Pandora, and Rook are based on the Babuk malware source code, but also have a lot in common.
Experts summarize that Bronze Starlight clearly has no difficulty creating short-lived ransomware variants that are only needed to disguise spying operations as ransomware attacks and complicate attribution. The fact is that the studied ransomware is based on publicly available or leaked source code, and Chinese hackers are known for willingly sharing tools and infrastructure with each other. That is, in such cases it is extremely difficult to track attribution, possible connections, and speak with confidence about any conclusions.




