VerdaCrypt ransomware appears to be a malicious program that locks your files by encrypting them, making them inaccessible until a ransom is paid, often in Bitcoin. It’s known for threatens to leak your data if you don’t pay, a tactic called double extortion. In this post, I’ll tell you what this threat is and how to remove it from your device.
VerdaCrypt Ransomware Overview
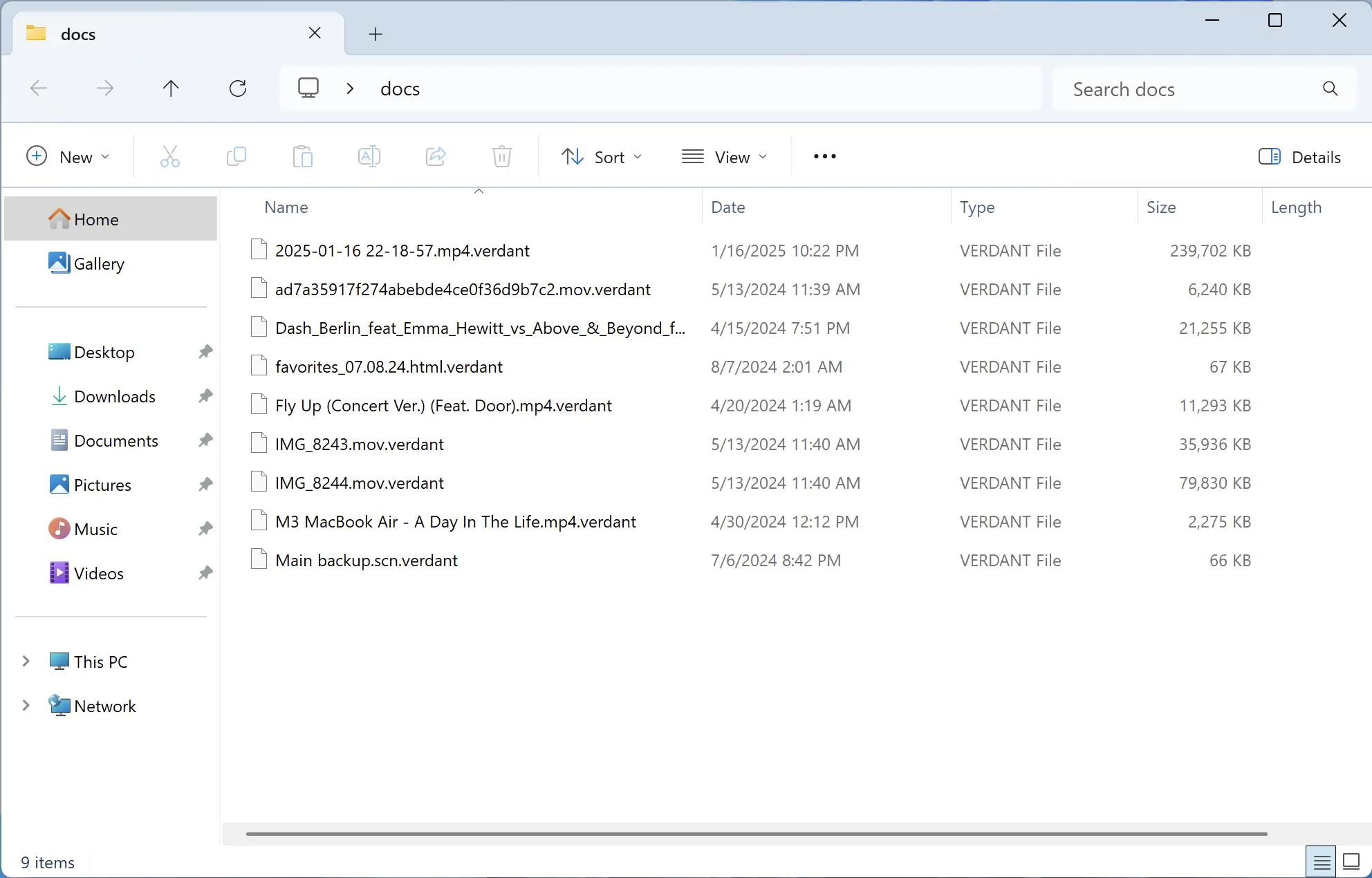
VerdaCrypt is classified as a ransomware-type program, a category of malware designed to encrypt victims’ data and demand payment for decryption. It was discovered by cybersecurity researchers during routine inspections of new malware submissions to profile platforms, indicating its active presence in the wild. This ransomware use the “.verdant” file extension, which it appends to encrypted files, rendering them inaccessible. This extension serves as a marker of infection, distinguishing VerdaCrypt from other ransomware variants.
A key characteristic of VerdaCrypt is its employment of double extortion tactics, which is not something new and has already been found in other ransomware. Beyond simply encrypting files, it also threatens to publish or leak sensitive data online if the ransom is not paid. This increases pressure on victims—especially businesses and institutions—who are concerned about reputational damage or legal consequences.
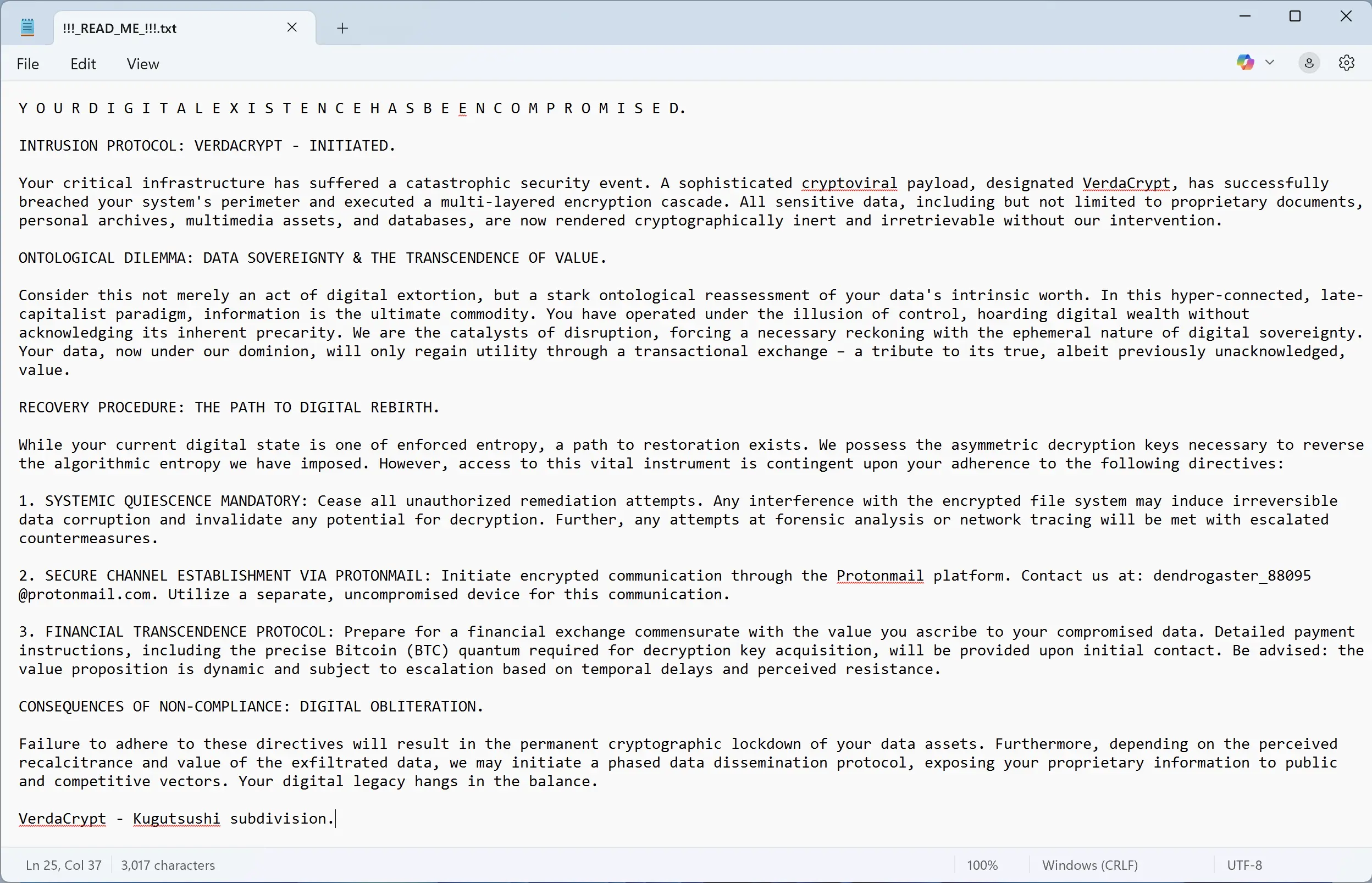
The ransom demand is typically delivered via a text file named !!!READ_ME!!!.txt, which is placed prominently on the desktop or within affected folders. It instructs victims to contact the attackers through encrypted communication platforms like Protonmail, using addresses such as [email protected]. Payment is usually requested in Bitcoin, with the amount potentially escalating over time. Attackers may also discourage alternative recovery attempts by warning that such actions could render files permanently inaccessible.
Operational Mechanisms
VerdaCrypt’s infection methods are consistent with common ransomware distribution strategies. It primarily spreads through phishing emails, which may contain malicious attachments, such as documents with embedded macros, or deceptive downloads. These emails often exploit social engineering tactics to trick users into opening infected files. Additionally, VerdaCrypt can be distributed via torrent websites or other untrusted sources, exploiting system vulnerabilities or being delivered through trojans.
Once installed, the ransomware executes an encryption payload that targets various file types, including documents, multimedia, and databases, using advanced cryptographic algorithms. These algorithms ensure that decryption without the attackers’ unique key is virtually impossible, enhancing the ransomware’s effectiveness. The only clarification is that this process excludes encryption of critical system files, which allows the infected system to work. This is done in order to give the victim the opportunity to pay the ransom.
The encryption process involves appending the “.verdant” extension to compromised files, signaling their locked status. VerdaCrypt can also spread across local networks and external storage devices, increasing its impact. The ransom note, !!!READ_ME!!!.txt, not only demands payment but may include dramatic language, such as “YOUR DIGITAL EXISTENCE HAS BEEN COMPROMISED,” to instill urgency and fear. This note provides instructions for contacting the attackers and specifies the ransom amount, often in Bitcoin, as said above.
Removal Strategies
Removing VerdaCrypt requires a combination of automated tools and manual steps to ensure the malware is eradicated from the system. The primary recommendation is to use reputable anti-malware software, such as GridinSoft Anti-Malware. It is critical to back up files before attempting removal to avoid potential data loss, especially given the ransomware’s impact on file accessibility.
Removal steps include booting the system in Safe Mode with networking, which can be enabled using the “msconfig” command to select Safe Boot, and then restarting. Next, you need to run a scan with GridinSoft Anti-Malware. Its enhanced malware detection system will find and eliminate the threat, so you will have no problem with the recovery steps and futher usage of the PC. Download it by the banner below, and don’t miss out on 6-day free trial that unlocks the full potential of the program.
Can I Get My Files Back?
Unfortunately, as of the latest research, there are no known public decryption tools specifically designed for VerdaCrypt. The encryption used is robust, and only the cybercriminals who developed the ransomware possess the necessary keys for decryption. Cybersecurity experts strongly advise against paying, as it does not guarantee data recovery and may encourage further criminal activity.
The most reliable recovery method is restoring files from backups. If an organization or an individual has valuable information or something established, they need to take care of uninterrupted access to valuable files in any scenario. You are encouraged to maintain regular backups on unplugged storage devices or remote servers, such as cloud services, to ensure data can be recovered without interacting with attackers.
Victims are also encouraged to report incidents to authorities, such as the IC3 Internet Crime Complaint Centre in the US (IC3), Action Fraud Police in the UK (Action Fraud), or the official portal of the German police (German Police), to aid in tracking and combating such threats.