If you’re seeing Trojan:Win32/Yomal!rfn detected by your antivirus, don’t panic – but don’t ignore it either. This cryptic warning just appeared on your screen, and now your computer feels like it’s running through molasses. Strange processes could be consuming your system resources. You might notice unexpected network activity even when you’re not actively using the internet.
This guide will help you remove this threat completely. Follow these step-by-step instructions to eliminate the threat. We’ll start with methods you can try right now.
| Detection Name | Trojan:Win32/Yomal!rfn |
| Detection Engine | Microsoft Defender Antivirus (Windows Security) |
| Threat Type | Heuristic behavioral detection – Generic trojan family |
| First Discovered | 2023 (ongoing detections) |
| Primary Function | Data theft, credential harvesting, backdoor installation, system modification |
| Target Systems | Windows 10, Windows 11, Windows Server environments |
| Common Infection Vectors | Malicious email attachments, software bundling, drive-by downloads, exploit kits |
| Typical File Locations | %TEMP%, %APPDATA%, %PROGRAMDATA%, System32 folder |
| Network Activity | Connects to remote command & control servers, downloads additional payloads |
| Persistence Methods | Registry modification, scheduled tasks, startup folder entries |
| Risk Level | High – Can lead to complete system compromise and data theft |
| False Positive Rate | Medium – Heuristic detection may flag legitimate software |
Understanding Trojan:Win32/Yomal!rfn
Trojan:Win32/Yomal!rfn is a detection name used by Microsoft Defender Antivirus. It’s a heuristic detection, which means your antivirus spotted suspicious behavior patterns. This doesn’t point to one specific malware family.
Your antivirus noticed something fishy and sounded the alarm. It might not know exactly what kind of problem you’re dealing with. The flagged threat could be anything from spyware to backdoors or even harmless software behaving strangely.
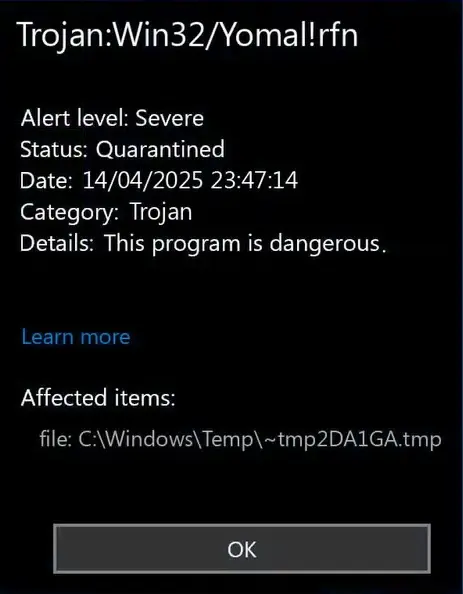
Because of this uncertainty, you shouldn’t panic immediately. But you also shouldn’t ignore it. Real threats can hide behind these generic detection names.
Signs Your System Is Infected
Determining whether your system has real malware requires observation and common sense. Modern threats usually operate silently. They avoid detection as long as possible.
Watch for these warning signs:
- Unusual system slowdowns without obvious cause
- Strange background processes you don’t recognize
- Internet usage spikes when you’re not browsing
- Programs crashing unexpectedly
- Files becoming corrupted or inaccessible
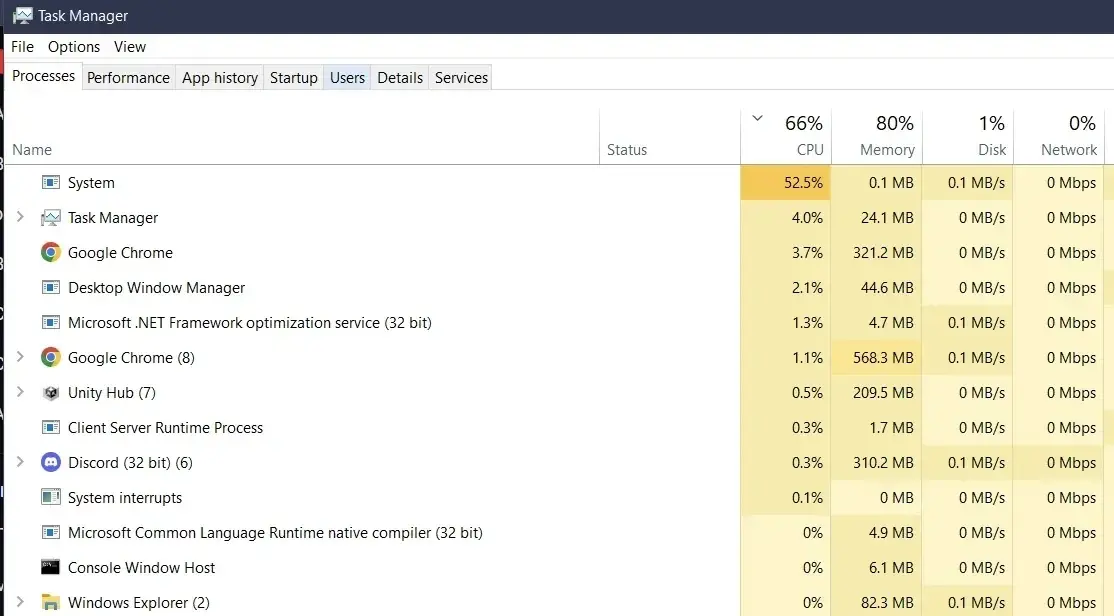
High CPU usage with no specific hungry applications visible should make you worry. Console windows that blink and disappear suddenly are another red flag. Your system security habits matter for preventing these issues.
A clear indicator of real infection appears after a few days. Your email or social media accounts might start sending out spam. This suggests credential theft has occurred. Someone has compromised your passwords.
Manual Removal Steps
Manual removal requires patience and attention to detail. These steps will help you eliminate threats that automatic tools might miss. Follow each step carefully.
Step 1: Boot into Safe Mode
Safe Mode prevents malware from loading with Windows. This makes removal easier and safer.
- Press Windows + R keys together
- Type “msconfig” and press Enter
- Click the “Boot” tab
- Check “Safe boot” option
- Select “Minimal” option
- Click “Apply” then “OK”
- Restart your computer
Step 2: Identify Malicious Processes
Task Manager helps you spot suspicious running processes. Malware often disguises itself with legitimate-sounding names.
- Press Ctrl + Shift + Esc to open Task Manager
- Click the “Processes” tab
- Look for processes with high CPU usage
- Check processes with random names or unusual locations
- Right-click suspicious processes and select “End task”
- Note the process names and file locations
Step 3: Delete Malicious Files
Remove files from common malware locations. These directories often hide backdoor components and other threats.
- Open File Explorer (Windows + E)
- Navigate to C:\Users\[Username]\AppData\Temp
- Delete suspicious executable files
- Check C:\ProgramData for unknown folders
- Examine C:\Windows\System32 for recent suspicious files
- Clear C:\Users\[Username]\Downloads of questionable downloads
Step 4: Clean Startup Programs
Malware often adds itself to Windows startup. This ensures it runs every time you boot your computer.
- Press Windows + R and type “shell:startup”
- Delete any suspicious shortcuts
- Press Windows + R and type “shell:common startup”
- Remove unknown startup items here too
- Open Task Manager (Ctrl + Shift + Esc)
- Click “Startup” tab and disable suspicious programs
Step 5: Registry Cleanup
Warning: Editing the registry can damage Windows if done incorrectly. Create a backup first.
- Press Windows + R and type “regedit”
- Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Delete suspicious entries
- Check HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Remove unknown startup entries
- Search for recently created registry keys with random names
Step 6: Check Scheduled Tasks
Malware can create scheduled tasks to maintain persistence. These run automatically at specific times.
- Type “Task Scheduler” in Windows search
- Open Task Scheduler as administrator
- Expand “Task Scheduler Library”
- Look for tasks with suspicious names or recent creation dates
- Right-click and delete unknown scheduled tasks
- Check the “Actions” tab for task details before deletion
Automatic Removal with GridinSoft Anti-Malware
Manual removal can be complex and time-consuming. For a faster, more reliable solution, GridinSoft Anti-Malware offers automatic detection and removal of heuristic threats. Professional anti-malware software can find hidden components and registry changes that you might miss.
These tools understand modern malware behavior patterns better than manual methods. They can detect threats that hide using advanced techniques.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Browser Cleanup
Browser-based threats often accompany system infections. Some malware specifically targets web browsers to steal credentials or redirect searches.
Remove Malicious Browser Extensions
Malicious extensions can monitor your browsing and steal login credentials. Similar tactics are used in information stealing campaigns.
Google Chrome
- Launch the Chrome browser.
- Click on the icon "Configure and Manage Google Chrome" ⇢ Additional Tools ⇢ Extensions.
- Click "Remove" next to the extension.
If you have an extension button on the browser toolbar, right-click it and select Remove from Chrome.
Mozilla Firefox
- Click the menu button, select Add-ons and Themes, and then click Extensions.
- Scroll through the extensions.
- Click on the … (three dots) icon for the extension you want to delete and select Delete.
Microsoft Edge
- Launch the Microsoft Edge browser.
- Click the three dots (…) menu in the top right corner.
- Select Extensions.
- Find the extension you want to remove and click Remove.
- Click Remove again to confirm.
Alternatively, you can type edge://extensions/ in the address bar to access the extensions page directly.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner.
- Select Extensions ⇢ Manage extensions.
- Find the extension you want to remove and click the X button next to it.
- Click Remove to confirm.
Alternatively, you can type opera://extensions/ in the address bar to access the extensions page directly.
Reset Your Browser
If you suspect browser-based threats, reset your browser completely. This removes persistent changes that malware might have made.
Google Chrome
- Tap on the three verticals … in the top right corner and Choose Settings.
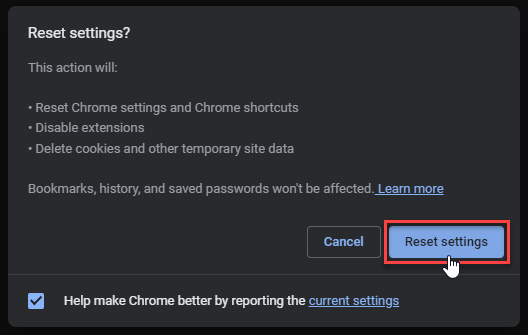
- Choose Reset and Clean up and Restore settings to their original defaults.
- Tap Reset settings.
Mozilla Firefox
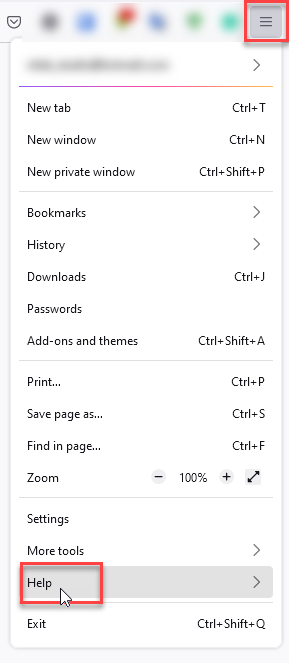
- In the upper right corner tap the three-line icon and Choose Help.
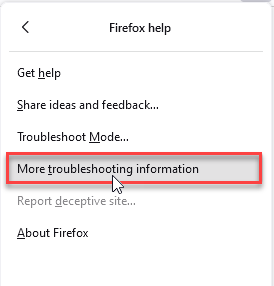
- Choose More Troubleshooting Information.
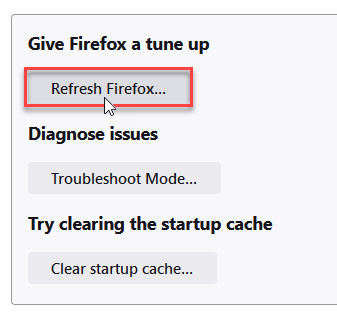
- Choose Refresh Firefox… then Refresh Firefox.
Microsoft Edge
- Tap the three verticals.
- Choose Settings.
- Tap Reset Settings, then Click Restore settings to their default values.
Opera
- Launch the Opera browser.
- Click the Opera menu button in the top left corner and select Settings.
- Scroll down to the Advanced section in the left sidebar and click Reset and clean up.
- Click Restore settings to their original defaults.
- Click Reset settings to confirm.
Alternatively, you can type opera://settings/reset in the address bar to access reset options directly.
Prevention and Protection
Preventing infection is easier than cleaning up afterward. Most malware enters systems through user actions or security weaknesses.
Email attachments remain a primary infection vector. Be cautious with files from unknown senders. Don’t open executable files unless you’re absolutely certain of their legitimacy. Phishing attempts often deliver malware through seemingly innocent attachments.
Software downloads from unofficial sources pose significant risks. Stick to official websites and app stores. Avoid cracked software and games, which commonly contain hidden malware.
Keep your system updated. Security patches fix vulnerabilities that malware exploits. Enable automatic updates for Windows and your installed programs. This applies especially to web browsers and popular software targets.
Use reputable antivirus software with real-time protection. Free solutions provide basic coverage, but paid options offer better detection rates. Consider solutions that specialize in ransomware protection if you handle sensitive data.
Regular system backups protect against data loss. Store backups on external drives or cloud services. Test your backup restoration process occasionally. This preparation helps you recover from severe infections or data breaches.
Frequently Asked Questions
What is Trojan:Win32/Yomal!rfn and why is it dangerous?
Trojan:Win32/Yomal!rfn is a heuristic detection name used by Microsoft Defender. It indicates suspicious behavior patterns that could represent various types of malware. The danger depends on the actual threat behind the detection, which could steal data, install backdoors, or compromise your system security.
How did Trojan:Win32/Yomal!rfn get on my computer?
This threat commonly spreads through email attachments, malicious downloads, infected USB drives, or exploit kits targeting browser vulnerabilities. It might also come bundled with pirated software or enter through compromised websites.
Can I remove Trojan:Win32/Yomal!rfn manually?
Yes, manual removal is possible using the steps outlined in this guide. However, it requires technical knowledge and careful execution. Professional anti-malware tools often provide more thorough removal with less risk of missing components.
Is it safe to delete files flagged as Trojan:Win32/Yomal!rfn?
Generally yes, but verify the file locations first. Legitimate system files are rarely infected, but malware often mimics system file names. When in doubt, quarantine files instead of deleting them immediately. This allows restoration if needed.
How can I prevent Trojan:Win32/Yomal!rfn infections?
Maintain updated antivirus software, avoid suspicious email attachments, download software only from official sources, keep Windows updated, and practice safe browsing habits. Regular system scans and backups provide additional protection.
What if manual removal doesn’t work?
If manual methods fail, use professional anti-malware software like GridinSoft Anti-Malware. These tools can detect hidden components and persistent threats that manual removal might miss. Consider seeking professional help for severe infections.
Should I be worried about false positives?
Heuristic detections like Yomal!rfn can sometimes flag legitimate software. However, it’s better to investigate thoroughly than ignore potential threats. If you’re certain a file is legitimate, you can add it to your antivirus exclusions after verification.
Can this malware steal my personal information?
Potentially yes. The threat behind this detection could include information stealing capabilities. Change your important passwords as a precaution, especially for banking, email, and social media accounts.
Quick Summary
Trojan:Win32/Yomal!rfn detection requires immediate attention. This heuristic warning indicates suspicious system behavior that could represent serious threats.
Manual removal involves booting into Safe Mode, identifying malicious processes, cleaning startup programs, and removing suspicious files. Browser cleanup and registry editing complete the manual process.
Automatic removal tools provide more reliable results with less effort. Professional solutions can detect hidden components that manual methods might miss.
Prevention focuses on safe computing practices. Avoid suspicious downloads, keep systems updated, and maintain reliable backup procedures. These habits prevent most malware infections.





